In today’s rapidly evolving digital landscape, collaboration has become the heartbeat of organizations worldwide. The ability to seamlessly share, create, and innovate together has emerged as a powerful catalyst for growth and success. However, alongside this transformative connectivity, a new set of challenges has emerged, particularly concerning the security of collaborative environments. Organizations leveraging Microsoft 365 (M365) face the daunting task of safeguarding valuable information amidst a complex web of dispersed applications and diverse data types. The ever-looming threats of data breaches and human error add an additional layer of urgency to the need for robust security measures.
From large regulated enterprises operating within specific industries to smaller companies, data holds immense importance across the board. While external adversaries pose a constant threat to system integrity, it is crucial to acknowledge that the majority of data leakage occurs due to end-user errors.
As per a report from Cisco there are more number of mobile devices in use than people on this planet 😊. Given the world we live in, trend toward greater mobility and efficient collaboration across the web and devices is increasing more than ever.
The M365 productivity suite has allowed users to modernise the way they work by allowing them to work from anywhere and with many people collaboratively. Within the realm of M365, when sharing files and folders, users are presented with a pop-up dialogue offering different options, each with its own implications, including:
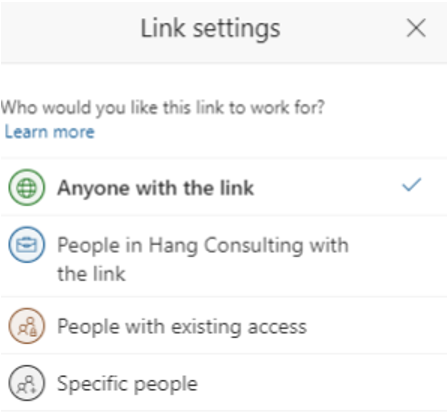
Anyone with this link: This choice carries significant risks, especially for external users, even though anonymous links are typically disabled.
People within the organization with the link: This option is frequently used during migration efforts.
People with existing access: Implicit permissions granted through large groups, including distribution groups.
Specific people: Explicitly defined individuals, often operating in broken inheritance situations common in Office Apps and Teams.
Sadly, this is dependent on the users fully comprehending the implications of each of these options. Furthermore, organizations are reliant on their end users to do the right thing on a consistent basis. This knowledge gap leaves organizations vulnerable and highlights the need for a robust solution.
What are the current challenges?
As organizations strive to unlock the potential of secure collaboration, they face an uphill battle in the ever-evolving cyber threat landscape. Within the realm of Microsoft 365 (M365), the complexities intensify, requiring a robust defence against data breaches and security vulnerabilities. Every good thing comes at a price and so does Microsoft’s solutions. At the time of writing this blog the license requirements to do the following was:
- Microsoft 365 E5/A5/G5/E3/A3/G3, Microsoft 365 Business Premium, SharePoint Online Plan 2, OneDrive for Business (Plan 2), Exchange Online Plan 2
- Office 365 E5/A5/G5/E3/A3/G3
- Microsoft 365 E5/A5/G5/F5 Compliance and F5 Security & Compliance
- Microsoft 365 E5/A5/F5/G5 Information Protection and Governance
However as Microsoft changes what can be achieved with their licenses from time to time, this link provides an overview.
Let’s delve into the challenges that organizations encounter on their quest for secure collaboration and the profound impact they can have.
Challenge 1: The Elusive Document Repository
Picture this: your organization maintains a document repository, be it a Teams site or a SharePoint Online (SPO) site. Yet, an alarming knowledge gap exists – who exactly has access to these repositories? This crucial piece of the puzzle remains a mystery, leaving organizations vulnerable to potential breaches. Failing to comprehend the scope of access rights is akin to playing a high-stakes game of hide and seek with your sensitive data.
Challenge 2: The Quest for Visibility
Microsoft offers a solution – generating permission reports to gain insights into internal and external users. While this approach sheds light on access permissions, it falls short when it comes to understanding user behavior and the true frequency of data access. For instance, how can you determine how many times your repository’s data has been accessed in the past 30 days? The answer lies in generating an audit report, a time-consuming process that impedes swift and proactive action.
Challenge 3: The Sensitive Data Conundrum
In today’s era of stringent regulations and compliance requirements, safeguarding sensitive data is paramount. But how can organizations identify the presence of such data within their repositories? Enter the data loss prevention (DLP) report. While crucial for compliance efforts, generating this report in isolation fails to provide a comprehensive view of the repository’s content. Without a clear understanding of what sensitive data resides within, organizations navigate treacherous waters, vulnerable to potential breaches and regulatory non-compliance.
Challenge 4: The Cost of Manual Reporting
The costs associated with manual reporting cannot be overlooked. Organizations grappling with the labor-intensive task of merging three disparate reports – permission, audit, and DLP – face a drain on resources and productivity. The time and effort invested in creating these reports manually far outweigh the value they deliver. Moreover, in the ever-changing landscape of permissions, activities, and content types, maintaining accurate and up-to-date reports becomes an uphill battle, fraught with risks.
In a world where cyber threats loom large, organizations cannot afford to overlook these challenges. The consequences of data breaches and non-compliance can be devastating, both financially and in terms of reputation. As the stakes continue to rise, the demand for a comprehensive solution that provides visibility, automation, and actionable insights becomes increasingly critical.
Unleash secure collaboration with AvePoint PI and Insentra Managed Services
In the realm of cybersecurity, securing collaboration within a Microsoft 365 (M365) tenant is a critical endeavour. AvePoint Policies and Insights (PI) emerges as the ultimate solution to fortify your organisation’s collaboration efforts while maintaining robust cybersecurity measures.
PI acts as a centralized hub that extracts valuable data from the Microsoft Graph, conducting comprehensive assessments and analyzes. By leveraging this automation, organizations gain a deeper understanding of their current state of secure collaboration and can proactively address potential vulnerabilities.
With AvePoint PI, organizations can reap a multitude of benefits:
- Comprehensive Risk Management: PI allows organizations to define their unique risk thresholds and select the most relevant regulations and Office 365 permission controls. This customisation enables organizations to prioritise critical issues, ensuring that potential risks are swiftly identified and mitigated.
- Uncovering Hidden Exposures: PI’s powerful capabilities enable organizations to easily identify content with anonymous links or Teams with shadow users. By shining a light on these hidden exposures, organizations can take immediate action to eliminate potential security risks.
- Timely Insights: PI empowers organizations with tenant-wide object- or user-based search capabilities, delivering the Microsoft 365 insights they need, precisely when they need them. This rapid access to crucial information enables organizations to make informed decisions swiftly and effectively.
- Proactive Monitoring: With dynamic dashboards, PI enables organizations to monitor critical access controls and sensitive data over time. By tracking and analyzing access patterns, organizations can detect anomalies and take proactive measures to mitigate potential security breaches.
By leveraging AvePoint PI, organizations establish a comprehensive framework for secure collaboration, bolstering operational efficiency and minimising cybersecurity risks. The solution’s automation capabilities not only save time and effort but also provide ongoing insights and notifications, ensuring that policy enforcement and end-user education remain seamlessly integrated.
In the face of the intricate challenges posed by secure collaboration within Microsoft 365 (M365) tenants, AvePoint Policies and Insights (PI) emerges as a game-changer. However, harnessing the full potential of PI requires expert guidance and implementation. That’s where Insentra, your trusted cybersecurity partner, steps in to bridge the gap between challenges and solutions.
Insentra’s deep expertise in cybersecurity and M365 implementation allows us to seamlessly integrate PI into your organisation’s environment. Our team of dedicated professionals works closely with you to understand your unique requirements and design a tailored strategy that maximises the benefits of PI while addressing your specific challenges.
By leveraging Insentra’s Managed Policies and Insights (PI), you gain access to a range of comprehensive solutions that drive secure collaboration and mitigate risks effectively. Here’s how Insentra can help:
- Strategic Planning: Our experts collaborate with your team to identify your organisation’s security objectives, regulatory compliance needs, and specific collaboration challenges. We then develop a roadmap that aligns PI’s capabilities with your desired outcomes, ensuring a customized and efficient implementation.
- Smooth Deployment: Insentra’s proven methodology ensures a seamless deployment of PI within your M365 environment. Our experienced consultants handle all aspects of the deployment, from pre-implementation assessments to configuration and testing. This results in a smooth transition, minimising disruption to your day-to-day operations.
- Tailored Policies: Insentra understands that every organization has unique security requirements. We work closely with your team to define and implement policies within PI that align with your risk appetite and compliance mandates. This tailored approach ensures that PI operates as an extension of your organisation’s security framework.
- Continuous Monitoring and Alerting: Effective security requires proactive monitoring. Insentra’s managed services for PI include ongoing monitoring and alerting capabilities. Our experts keep a vigilant eye on your collaboration environment, promptly identifying and addressing any security incidents or policy violations. This proactive approach helps you stay one step ahead of potential risks.
- Actionable Insights: Data is the key to informed decision-making. Insentra’s experts leverage PI’s powerful analytics and reporting features to generate actionable insights. We transform raw data into meaningful visualisations and reports, enabling your organization to make informed security decisions and drive improvements in secure collaboration practices.
- Training and Support: People are often the weakest link in security. Insentra provides comprehensive training and support to educate your users on secure collaboration practices within M365. Our experts conduct engaging workshops and provide ongoing support to empower your workforce with the knowledge and skills needed to navigate PI effectively.
With Insentra’s Managed Services for PI, your organization can harness the full potential of AvePoint’s solution while benefiting from our extensive cybersecurity expertise. Together, we can create a robust and secure collaboration environment within your M365 tenant, reducing risks, enhancing compliance, and driving productivity. Contact us today to unlock the power of secure collaboration within your organization.










