Associating SAML attributes with organizations and teams in Red Hat Ansible Automation Platform.
SAML is an openly available protocol that permits Identity Providers (IdP) to transfer authorization credentials to a Service Provider (SP). Through this, the IdP delivers an XML document, also known as an assertion, to the SP which contains a set of attributes that identify the user who is logging in.
In Ansible Automation Platform, these attributes can be utilized to determine the organization and team of the user. To illustrate this, let’s consider an example where Microsoft Azure’s Active Directory functions as the IdP, and Ansible Automation Platform serves as the SP.
The following procedure outlines all the required steps to enable SAML authentication on AAP:
- Navigate to Azure portal: http://portal.azure.com
- Log in ensuring you have enough permissions to create Enterprise Application/Azure AD SAML Toolkit
- In the Search Resources, type: Enterprise Applications
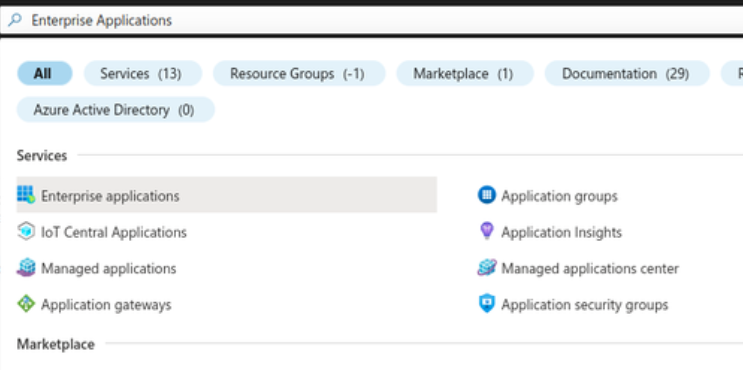
- Click on New Application
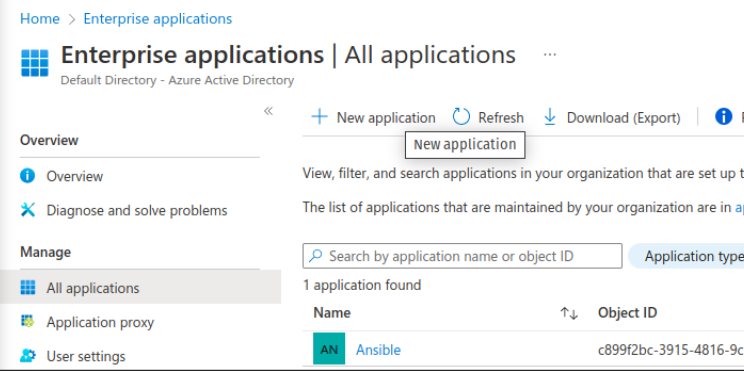
- In the Browse Azure AD Gallery, type Toolkit and click on Azure AD SAML Toolkit
- Specify the name of the new application in a new window and click Create:
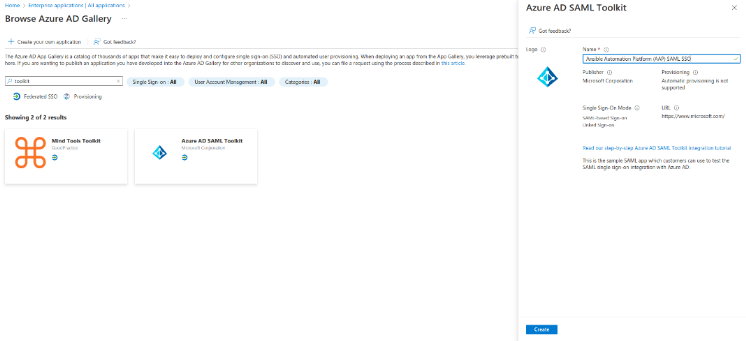
- You can expect a view similar to the following:
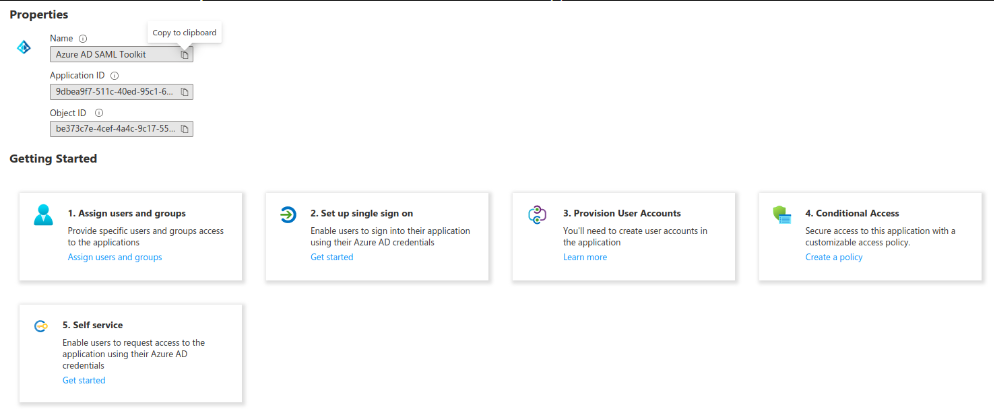
- Click on Assign Users and groups
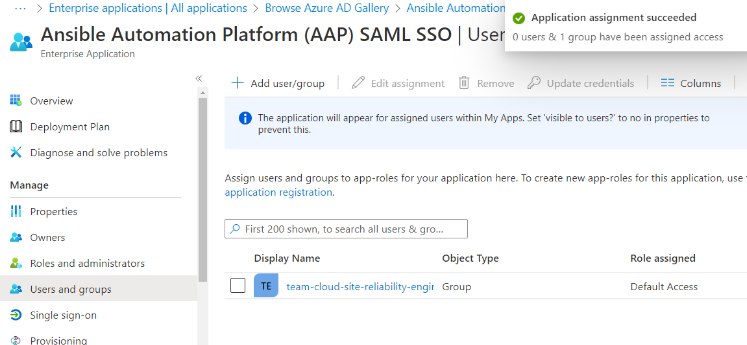
- Click on Add User/Group and select all required groups, making sure the ID is also noted down. Click Assign
| Group | ID |
| team-cloud-site-reliability-engineering-sandpit | 411605cd-d9b0-40f3-b9c2-dbda5b2f2ede |
- Once all the groups are selected, click Select. You should see the result similar to the following:
- In the left pane, click Single sign-on and select SAML:
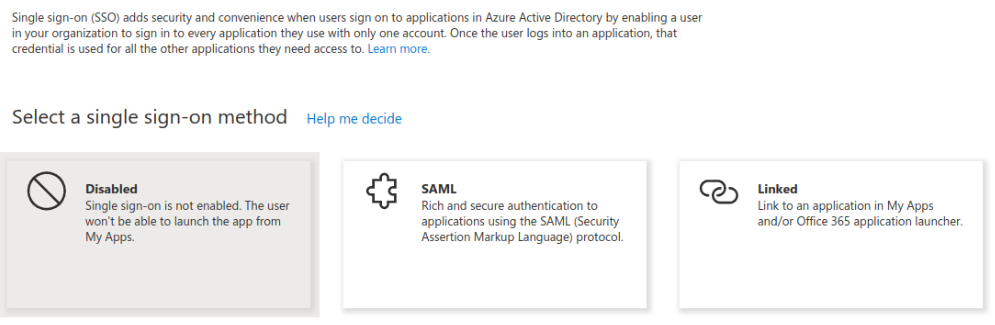
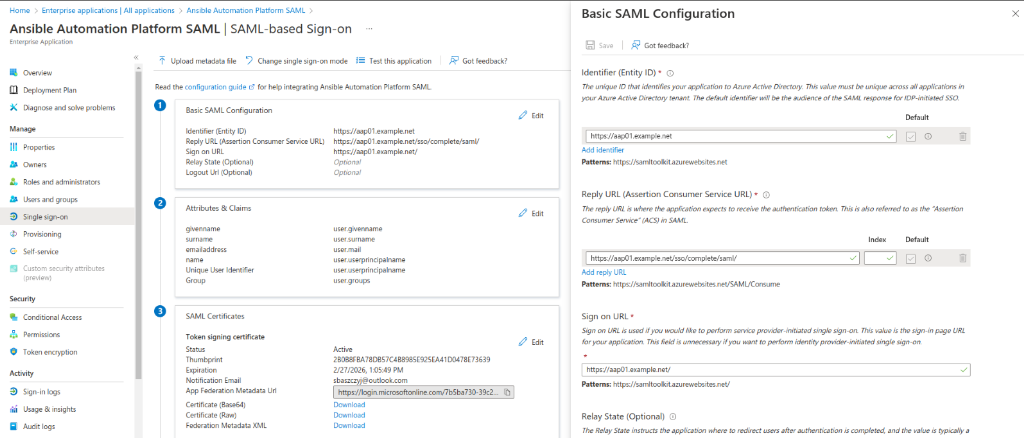
Specify the following for Basic SAML Configuration and populate the fields as per the table below:
| Field | Value | Description |
| Identifier (Entity ID) | https://aap01.example.net | Unique Identifier. Can be anything as long as the value in Azure SAML and on AAP will be the same |
| Reply URL | https:// aap01.example.net /sso/complete/saml/ | Reply URL. See the note below |
| Sing on URL | https://aap01.example.net / | URL of the AAP Controller |
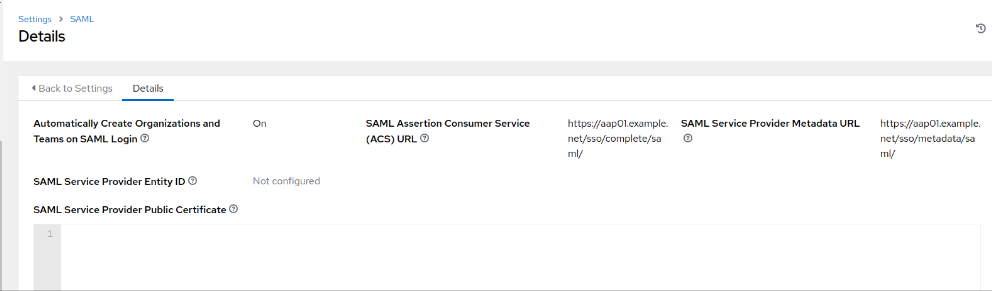
Note: Reply URL Can be found in AAP configuration. Click on Settings –> SAML and find SAML Assertion Consumer Service URL:
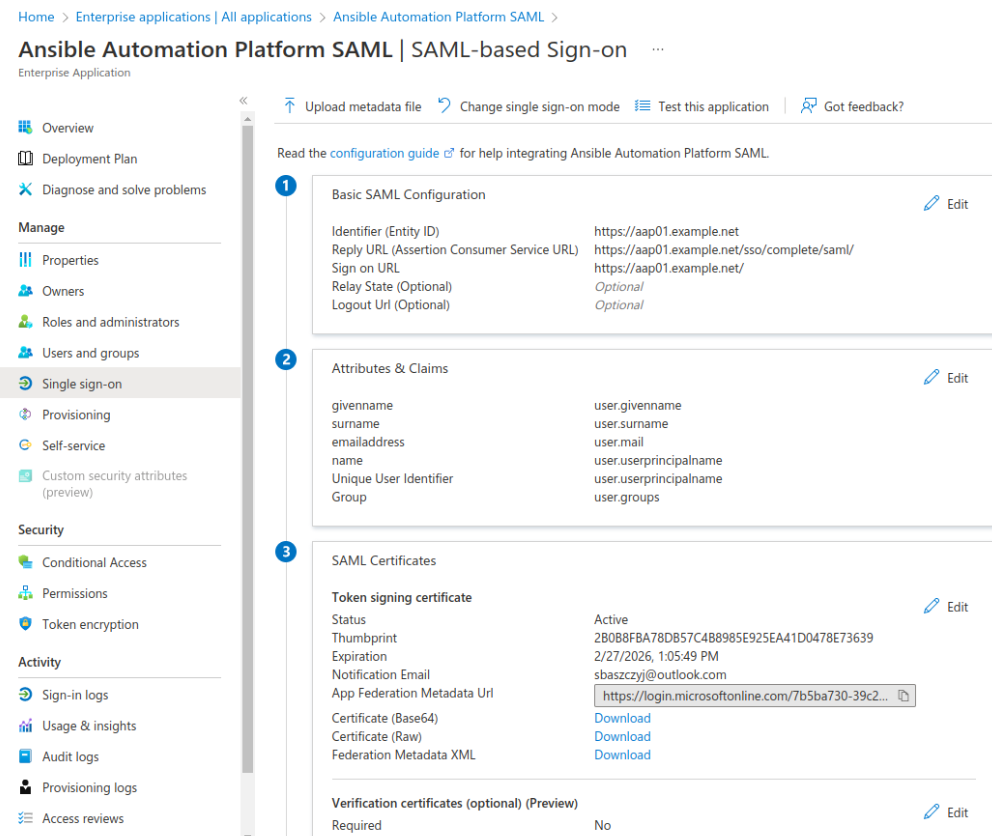
- Click on Edit in Attributes and Claims:
- Add Group ID as an attribute and click Save
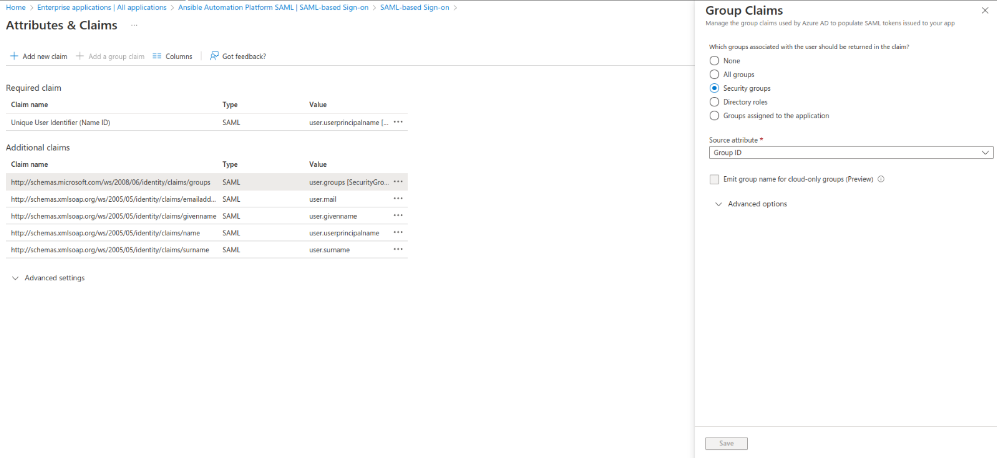
- The list of Claims will resemble the following:
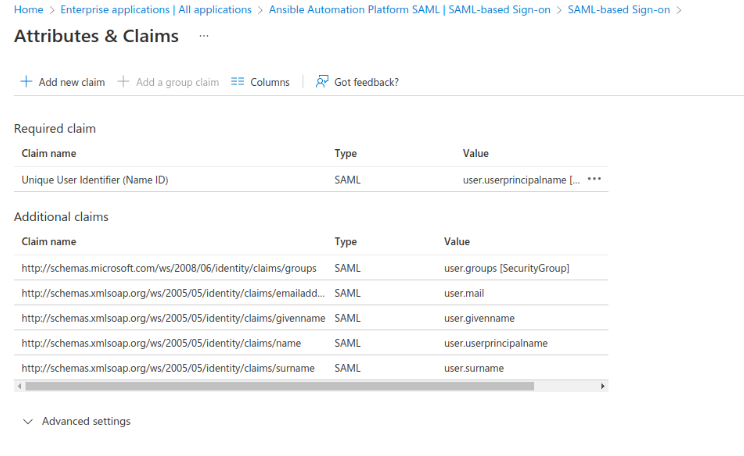
- Download the Federation Metadata XML file and provide it to the team responsible for configuration of the AAP SAML
Ansible Automation Platform Configuration
- Navigate to AAP and log in as admin
- Navigate to Settings → SAML
- Scroll the page to the bottom and click Edit
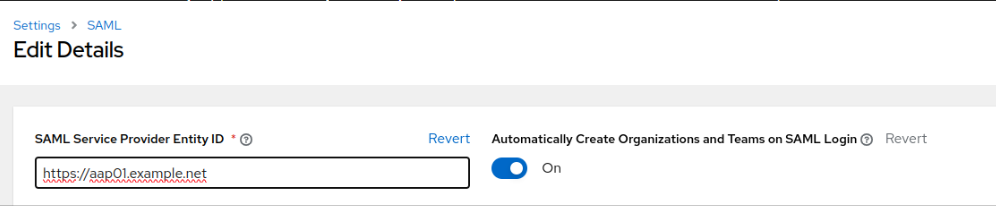
- Scroll the page to the top and specify SAML Service Provider Entity ID:
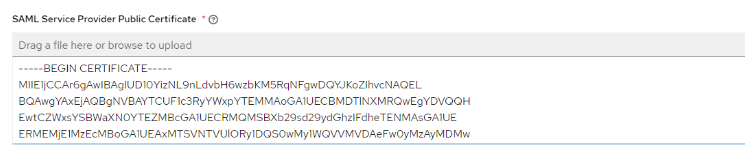
- Specify the SAML Service Provider Public Certificate. The Public Certificate has to be certificate generated by CA and cannot be self-signed certificate. In case you are using the AAP in cluster configuration, that would be the certificate that was generated for the Load Balancer FQDN. If you have only one node in the cluster, provide the certificate that has been already loaded on AAP. It can be found in /etc/tower/tower.cert
- Specify the SAML Service Provider Private Key. Similarly, to the above, it is the key that has been generated with the certificate for the Load Balancer (in case cluster configuration) and for the stand-alone configuration – the key can be found in /etc/tower/tower.key
- Specify SAML Service Provider Organization Info. For example:
{
"en-US": {
"displayname": "Your Company",
"url": "https://aap01.example.net",
"name": "Your Company"
}
} - Specify SAML Service Provider Technical Contact. For example:
{
"emailAddress": "Your Email",
"givenName": "Your Name"
} - Specify SAML Service Provider Support Contact. For example:
{
"emailAddress": "Your Email",
"givenName": "Your Name"
} - Define SAML Enabled Identity Providers. All the data is available in the Federation Metadata XML file the Azure team should provide
{
"azure": {
"attr_first_name": "http://schemas.xmlsoap.org/ws/2005/05/identity/claims/givenname",
"attr_display_name": "http://schemas.xmlsoap.org/ws/2005/05/identity/claims/displayname",
"attr_email": "http://schemas.xmlsoap.org/ws/2005/05/identity/claims/emailaddress",
"attr_last_name": "http://schemas.xmlsoap.org/ws/2005/05/identity/claims/surname",
"entity_id": "https://sts.windows.net/c28b2d80-129e-4693-88bd-5f43e59072f9/",
"url": "https://login.microsoftonline.com/c28b2d80-129e-4693-88bd-5f43e59072f9/saml2",
"x509cert": "MIIC8DCCAdigAwIBAgIQcGRe2t0tzqlJvySsQ2r6wjANBgkqhkiG9w0BAQsFADA0MTIwMAYDVQQDEylNaWNyb3NvZnQgQXp1cmUgRmVkZXJhdGVkIFNTTyBDZXJ0aWZpY2F0ZTAeFw0yMzAyMjQwMjU3MTlaFw0yNjAyMjQwMjU3MTlaMDQxMjAwBgAMTKU1pY3Jvc29mdCBBenVyZSBGZWRlcmF0ZWQgU1NPIENlcnRpZmljYXRlMIIBIjANBgb55FI2tt3UDUKR8yx3vqNmTRl9h+N3ekDzi9TWU7nMTRMzDjRQTJzDOjLXHfwYAnKxG454IHg9gB1P9Ng9ozAoxDpIQFrGSiUTSOUHwMFfAy6+p+Zz08oS2uQMa7qREwqqqb/IOqOkCrHt3aQP+ELWchwsLoML0Y1K/gR7gmNLLJM+1NJmJTHPnnF6tFeU8eyT+qbmbE+OI7xaQrkzvwZ7itsqgebMu94N6RYRJNm+3UT6D8FwRYe3vkmwGK9mfUejMd7cDHXx+2Uupg/A8zEFGHkQIDAQABMA0GCSqGSIb3DQEBCwUAA4IBAQCRfwe1QtCXqacR6oWendMSWd7JYydhIEEP1E2FOqe39xM90A4cYBPg8Ri+dLV+hPwC9D4tE7orziP8acLw5Mh5l7UKwYFDH3IOAPKUjRQqhCd4mGwvsaboCyaUazh4mhdhZbZd60wySAx/bTMwbY1wWV0g6OF4+PaZBUqu+3gZkOKqy3003FPTGgl6pHIU77V6ad9jvhNFzxUznpRLdwY+eXEL3rvvWwKIMJ3t9oZsd8lw3F77NwQJZrSdxWbYrMfaoZR39H2KHBut6pSYJKbJ/JIuRtcf+UbC6pYW9jwHGQYb6VXPcXzrxox6lYh24Z83oPyRI2R9P8NMMI7w",
"attr_user_permanent_id": "name_id",
"attr_username": "http://schemas.microsoft.com/identity/claims/displayname"
}
} - Specify the SAML Organization Map. For example:
{
"Default": {
"users": true
},
"Cloud": {
"users": true,
"admins": [
"user@example.net"
]
}
} - Specify SAML Organization Attribute Mapping
{
"saml_attr": "organization",
"remove": true
} - Specify SAML Team Attribute Mapping
{
"team_org_map": [
{
"team_alias": "Engineering",
"organization": "Cloud",
"team": "4116cd-d9b0-40f3-b9c2-bda5b2fede"
}
],
"saml_attr": "http://schemas.microsoft.com/ws/2008/06/identity/claims/groups",
"remove": true
} - Click Save
- Log in to one of the AAP Controller nodes and execute the following command to download SAML Service Provider Metadata:
wget https://aap01.example.net/sso/metadata/saml/ Configuration for System Administrators
The following configuration is required to enable users of a specific AD Group to be set as System Administrators:
In SAML Settings, add the following configuration in SAML User Flags Attribute Mapping field. Where the ‘is_superuser_value’ is set to an Azure AD Group ID. In this situation, we have the ID of the following AD Group: team-cloud-superadmin. The ‘is_superuser_attr’ is set to the SAML claim which was configured before (please the configuration above).
{
"is_superuser_attr": "http://schemas.microsoft.com/ws/2008/06/identity/claims/groups",
"is_superuser_value": [
"c3338f53-5be5-4d6c-9baa-b2b0c81282bc"
]
} Azure SAML configuration – Finishing touches
- Navigate to Azure portal and find the application created earlier (Ansible Automation Platform (AAP) SAML SSO)
- Click – Upload metadata file
- Select the file and click Add. The configuration file will populate all the relevant fields necessary to finalize configuration of SAML
- Testing and aligning the mapping as per your requirements can now be completed
Conclusion
To conclude, by utilizing the SAML protocol, Red Hat Ansible Automation Platform can be set up to allow Microsoft Azure Active Directory to transfer authorization credentials to determine the organization and team of the user logging in. By following the procedure outlined in this guide, you can enable SAML authentication on AAP and streamline the process for user management. Get started today by following the step-by-step instructions and experience the benefits of SAML authentication for your organization, contact us today.
Related Articles
How to configure Ansible Automation SAML SSO with Red Hat SSO
How-to guide on Ansible Tower Backup and Restore on Azure
Ansible Tower in Google Cloud Platform
Protecting the automation engine – Backup for Ansible AWX Project