In part one of this series covering Exchange Hybrid, we went over DAuth and OAuth and briefly described why Microsoft switched their Exchange Hybrid configuration to OAuth for Exchange delegation.
In part two of this series, we will take a look at how OAuth is used when establishing an Exchange Hybrid configuration (which federates your Exchange on-premises organization with Exchange Online) and review the InraOrganization Connector (IOC).
IntraOrganization Connector (IOC)
With the newer hybrid configuration, Microsoft creates one connector that points to Exchange Online and one connector that points to Exchange on-premises. These are called IntraOrganization Connector (or you can simply refer to them as intraorg connectors or IOCs) These IOCs tell each side how to communicate with the other side. Basically, they are pointers for the hybrid configuration.
If you connect to your Exchange on-premises management shell and typed Get-IntraOrganizationConnector, you’ll see a number of parameters, including the following:
- TargetAddressDomains – this will point to the <companyname>.mail.onmicrosoft.com domain
- DiscoveryEndPoint – this will point to the Autodiscover servers for Exchange Online
- Enabled – Should be set to ‘True’ if the OAuth configuration was successful. If set to ‘False’, then that means your OAuth configuration probably failed during the HCW and it is not falling back to the legacy DAuth for the connection requests
S2S OAuth 2.0
The name that Microsoft has given for its OAuth integration is S2S OAuth 2.0. S2S, standing for server-to-server authentication. Now, if you are really interested in getting a deep dive in this protocol, then you are in luck, here is an in-depth link that will gratify all of your OAuth 2.0 desires!
All joking aside, I just want us to focus on how these connections and requests are made. Microsoft has the following flow chart diagramed (full steps are detailed in this link) which details how a free/busy request is made from on-premises to Exchange online:
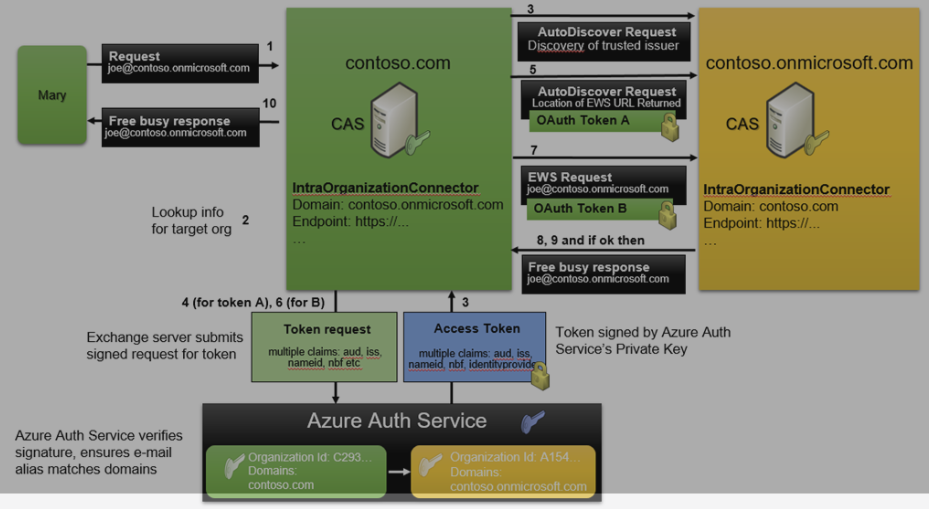
There’s a lot of steps to get the free/busy response back, but those steps are completed within an instant. Mary wants to see Joe’s calendar, so in the background, the Exchange server receiving the request looks up the target info, finds that Joe’s mailbox is in Exchange Online via Autodiscover. OAuth tokens are generated (two, as you’ll note) to verify the requesting side and responding side. Once verified (via the Azure Auth Service), the free/busy response for Joe’s mailbox is sent back to the Exchange on-premises server and into Mary’s mailbox. Mary can now see if Joe is free or busy when scheduling a meeting.
The same steps apply for requests coming from Exchange Online to Exchange on-premises.
Up Next
Up next in the final part of this series, discover more features of Exchange Online federation. Contact Insentra for expert guidance on planning and implementing your Exchange hybrid deployment, including IOC, OAuth 2.0, and more.