I am sure everyone is familiar with the cattle and moat network security model where everything was secured within a perimeter. For example, this could be the four walls of your datacentre where you have all your applications. In this instance, your data and the resources are protected and kept within your secure network. Your users would connect via VPN (Virtual Private Network) to access the corporate network and do their day job. The idea here was if you could not connect to the secure network then you could not access any of these resources. What actually ended up happening was a lot of these resources just ended up unprotected. So, to keep users productive, businesses had to compromise on security. It was extremely hard for organizations to get the visibility they needed, to be able to integrate different solutions together and to establish end-to-end security, so they had to look for a new security model which would be able to meet today’s agile, modern workplace requirements where we have transitioned from local datacentres to public cloud. Perimeter networks have become obsolete as users can work from anywhere.
ENTER ZERO TRUST
We need to be able to meet our ever-changing modern workplace requirements where people are enabled towork from anywhere. We need to protect people, devices, applications and data from any location, and this is where the zero-trust model has really come into play. Before we go too far, I just want to mention the zero trust security model is a mechanism for you to be able to secure all your assets regardless of where they are. There is not one piece of technology or software which will suddenly light up zero trust for your business. Your security and IT professionals and everyone else need to go through a mindset change to be able to take on this new zero trust security model and it will take multiple initiatives, a road map and architecture.
THE PRINCIPLES OF ZERO TRUST
So, when we talk about Zero Trust and Microsoft we follow the following key principles:
- Verify explicitly – We need to make sure we are always authenticating and authorizing all of our available data points. The data points could be user’s identity, location, device health ( such as whether it is jailbroken or not), a service or workload which is trying to be accessed, data classifications etc
- Use least privileged access – For example if an admin needs to make a change in Azure, we are going to give them just enough time to complete the change and we are going to only give them access to make the change they need to make. We are not going to grant them full admin rights if they do not need it. Then of course we are going to make sure we protect our data throughout this journey
- Assume breach – we must be prepared to be humble about our environment and ask ourselves if an attacker were to get in in how would we minimise the blast radius? How do we easily stop them from moving laterally across the company? For this we need to have good visibility, keep driving threat detection and improving our defence against breaches
ZERO TRUST WITH MICROSOFT
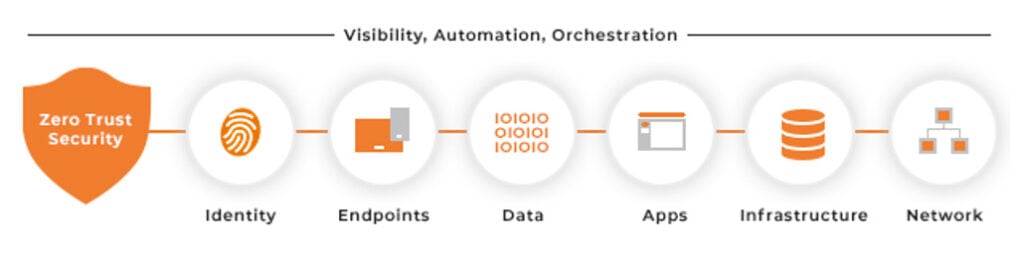
Microsoft’s zero trust model has six key components,
- Identities – Ensuring everyone has a strong Identity which we can authorize and authenticate across the environment
- Endpoints – Each endpoint used to access corporate data should be monitored to ensure it is being used by a trusted identity. Also, it is imperative to ensure relevant security polices are applied for personal as well as corporate devices and no jailbroken devices are able to access company data.
- Applications – For example, look at the SaaS applicationsemployees are using and if they have access to data, do they have the right permissions in place? Can we even control their access based on visibility and monitoring?
- Data -Where we can start putting policies around our data estate and making sure we start labeling and encrypting files and emails, so they do not go into the wrong hands
- Infrastructure – As we talked about earlier, we need to make sure people are using least privileged access andt also, we are detecting anomalies and trends which may not be what we are expecting so we can go ahead and proactively protect our infrastructure from attacks
- Network – Ensure we are not automatically allowing users in simply because they are within the internal network. We need to ensure everything is properly trusted from our users to our devices
For more on Zero Trust and security, consider these other articles:
Everything You Need to Know About Zero Trust
CIA Triad – The Mother of Data Security
Keep sane and until next time hasta-la-vista!










