In part 4 of the series we take our implemented environment and ensure it is expanded, governed and monitored correctly.
RUN
The features of the run phase are for ongoing maintenance, you are now running and there isn’t a lot more to deploy. These things are measures we have found which are good enough to upkeep and refine the service regularly:
- Set up Information Governance reviews (monthly, quarterly, etc)
- Integrate AIP logs into your SIEM or helpdesk system
- Retrain and educate users
- Integrate file share data stores
- Expand Information Governance policies
- Integrate other applications
- Upgrade Torsion to full protection
Setup Information Governance Reviews
Now we have implemented AIP it needs to be monitored and tuned. Someone needs to analyze logs, collect and aggregate feedback and recommend policy tuning. To begin with we suggest a bi-weekly or monthly review would be appropriate, then you could look to relax this after it’s embedded in the business.
Integrate AIP into your Security Information and Event Management (SIEM) Solution
If you have an SIEM solution configured and it’s your one source of truth for logs – integrating AIP logs into this should be relatively straight forward as you have already configured your Azure Analytics workspace. This can form part of your governance reviews.
Re-train and Educate Users
Over time you will notice trends in your logs such as sensitive information being shared in the wrong way or not classified properly, especially while you are tuning your policies. Updating users as they are using the system (especially if you don’t have the automated classification E5 features) will be required. Monitoring your DLP alerts and matching content with the Torsion system will assist you in identifying these scenarios where the wrong people have access or the wrong classification label has been used.
Integrate File Share Data
Or just migrate it?
If you can’t, then running the AIP Scanner can help identify and classify documents in shares.
Bespoke Scenarios
Sometimes you will run into a requirement which doesn’t fit your normal policies. It is possible to create a label specifically for this requirement and assign it to a user. For example, if we had a user who was dedicated to working on a top secret government project, we could assign this policy to this user and force the label on every piece of content they create until they are finished with the project. Then, if they want to remove the classification they must provide justification which will trigger an alert that can be investigated.
Expand Information Governance Policies
Looking to achieve ISO 27001/ 27002 or other compliance certifications? You probably need to expand what you have implemented by having further policies defined for information governance.
We used Microsoft Compliance Manager to go through the required controls for this certification, but there are many resources out there. An example of high-level controls are here:
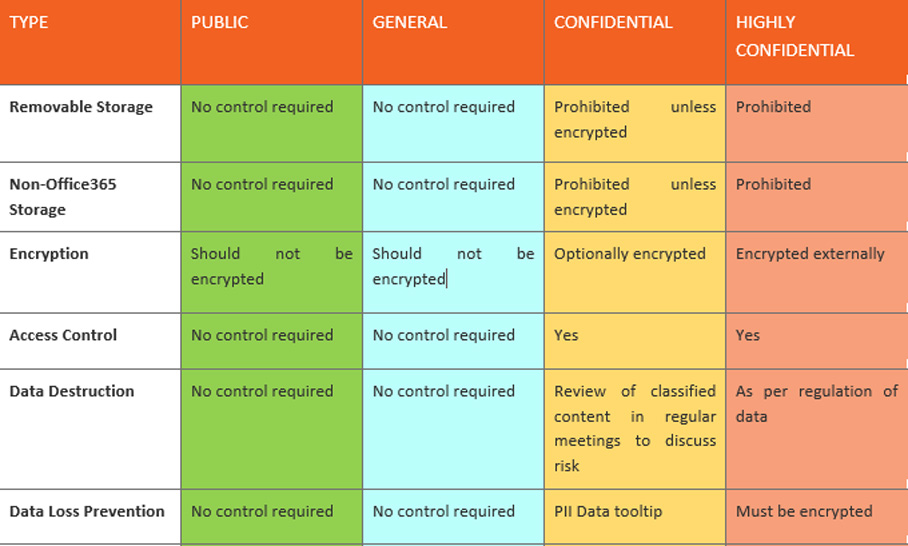
This stuff is good to have written down, especially when the auditers come a-knockin’!
Integrate Other Applications
AIP can now be referenced by the Graph API, so your current document management system could be integrated here using this. I am sure people smarter than me can figure out how to integrate all sorts of business processes!
Upgrade Torsion to Full Protection
Torsion implemented to “Full Protection” or as we call it “Level 3” further builds upon the foundation of visibility and ownership by moving into classification adherence and governance policies. At implementation level 3, Torsion has full integration with AIP and DLP and will continuously monitor and report upon access behaviors, information protection policy breaches, plus the security status of any given data area. To visualise what this looks like, think of the standard SharePoint view, where you typically see the “share” button in the top right, you would now see things like “Share with Torsion” and “Security Status OK”. Each of these buttons clicks through to give you the power to act on the information presented (Review or revoke access, or resolve security issues).
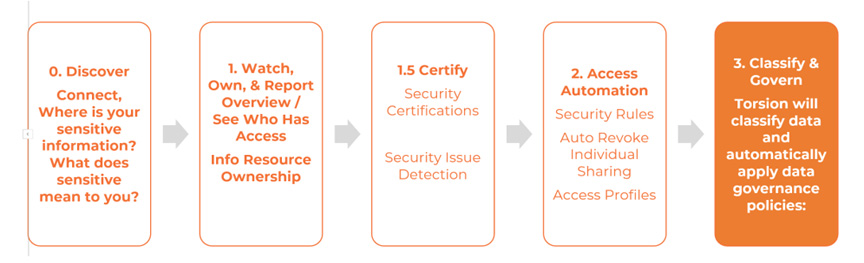
And that’s a wrap! Please reach out if you have any questions, or click to return to learn more about Azure Information Protection.










