INTRODUCTION
Insider threats are a growing concern for organizations regardless of size and/or industry. The amount of sensitive data organizations generate and collect is growing at an alarming rate, and it is crucial to protect it from being stolen, misused or exposed. Insiders, be they current employees, contractors or third-party vendors, can pose a significant risk to an organization’s sensitive data and intellectual property.
Several trends are driving the growth of insider threats, particularly the increasing reliance on remote work and remote access to corporate systems. With more employees working from home or on the go, it has become easier for insiders to access and potentially misuse sensitive data.
Another trend contributing to the rise of insider threats is the growing complexity of corporate systems and networks. As businesses adopt more advanced technologies and software, it becomes more difficult to monitor and control access to sensitive data, thus creating opportunities for insiders to exploit vulnerabilities and steal or misuse data.
The impact of insider threats can be severe, both in terms of financial losses and reputational damage. According to a study by the Ponemon Institute, the average cost of an insider threat incident is $15.4 million and it takes an average of 85 days to contain1. A survey by the Center for Strategic and International Studies found that 44% of respondents experienced an insider threat in the past year.
Evidently, insider threats can have a significant impact on an organizations. To mitigate the risks posed by these threats, organizations must take proactive measures to protect their sensitive data and build an effective insider threat mitigation program. This eBook will explore various forms of insider threats, how to identify and protect against them and how to build and operate an effective insider threat mitigation program.
1 Source: Ponemon institute 2022 Cost of Insider Threats Global Report
2 Source: Center for Strategic and International Studies (CSIS) and McAfee’s “The Human Factor Report: Insider Threats in the Age of Digital Transformation”
Insider Threats: Protecting Your Organization from Within
What is an Insider Threat
Intentional Insider Threat
Intentional insider threats are carried out by individuals who deliberately use their access and privileges to cause harm to an organization. These individuals may have personal or financial motives or they may seek to compromise an organization’s security posture for political or ideological reasons. Examples of intentional insider threats include:
- employees who steal proprietary information to use for personal gain or to give to competitors
- individuals who seek to sabotage an organization’s operations or damage its reputation
- insiders who provide sensitive information to external factors such as hackers or nation-states.
Unintentional Insider Threat
Unintentional insider threats are caused by individuals who may not have malicious intent but inadvertently compromise an organization’s security posture. These individuals may be careless with sensitive information, unaware of security best practices, or simply make a mistake. Examples of unintentional insider threats include:
- employees who accidentally download malware
- individuals who expose login credentials or sensitive information online
- insiders who fall for phishing scams or other social engineering attacks.
Other Types of Insider Threat
Third-party threats – situations where outsiders with access to an organization’s sensitive data or systems misuse their access e.g. a vendor who breaches the terms of a service agreement.
Insiders in collusion with external bad actors – situations where an employee is coerced or bribed into providing sensitive data or access to an attacker such as a nation-state, competitor or cybercriminal.
Insider threats come from all levels of the organization and are not limited to lower-level employees. Often managers and senior executives are a more significant threat due to their access priveledges. Identifying insider threats and understanding their potential motivations is crucial to effectively implement risk mitigation strategies.
Common types of Insider Threats and their Cost
1
Careless or Negligent Employees/Contractors: 56% of reported insider threat incidents were the result of a careless employee or contractor. These individuals may not have malicious intent yet their actions can still result in a data breach. The average cost per incident caused by a negligent insider is USD$484,931.
2
Criminal or Malicious Insiders: Criminal or malicious insiders are individuals who deliberately use their access and privileges to cause harm to an organization. These insiders may have personal or financial motives, or may seek to compromise an organization’s security posture for political or ideological reasons. According to the report, malicious or criminal insiders were behind 1 in 4 incidents with an average cost per incident being USD$648,062.
3
Cybercriminal Credential Theft: Credential theft is the act of stealing users credentials to access critical data. The report found incidents involving credential theft represented 18% of all reported incidents… almost double the previous study. Credential theft is the costliest to remediate with an average cost per incident being USD$804,997.
Frequency of Insider related Incident worldwide
Insider threats can have devastating impacts broader than just the financial costs. Some of these impacts include:
- Loss of sensitive data: The loss or theft of sensitive data, such as intellectual property, customer information, or financial data can have a significant impact on an organization’s ability to compete and its legal liability – particularly when it comes to personal information.
- Reputational damage: Insider threats can lead to reputational damage which inevitably negatively impacts a business. For example, a data breach involving sensitive customer information can lead to a loss of trust which can and usually is difficult to regain.
- Legal liabilities: Insider threats can lead to legal liabilities such as fines, lawsuits and various other penalties. For example, a data breach involving sensitive personal information can result in penalties under regulations such as the General Data Protection Regulation (GDPR).
- Loss of business: Insider threats can lead to the loss of business as customers, partners and suppliers may choose to do business with competitors who are perceived to be more secure.
- Downtime: Insider threats can also cause downtime in business operations, which can result in a loss of productivity and revenue.
Understanding the potential impact of insider threats often helps security teams and business leaders to better prioritise and address risks. Insiders can cause major damage such as stealing sensitive data, disrupting operations and even stealing money. It’s crucial for companies to have a robust insider threat program in place to protect sensitive data and intellectual property and reputational risk.
COST OF INSIDER THREAT
The average annual cost per incident for the three types of incidents
$15,378,635
Average activity cost by days to contain the incident
Average trend in activity cost per incident for 7 activity centres
Overall
$645,997
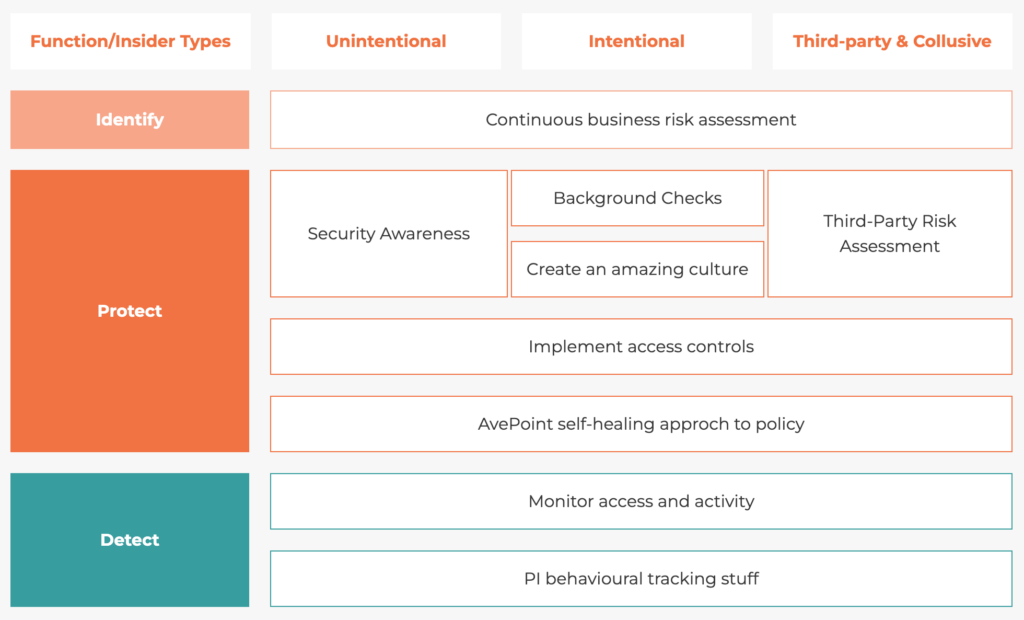

Identifying Insider Threat
Recognising The Signs Of Insider Threat
There are several Insider Threat warning signs including:
- Unusual access to sensitive data: Insiders who pose a threat may try to access sensitive data or information outside of their normal job responsibilities. This could include attempting to access sensitive data not relevant to their role, or attempting to access data at unusual times, such as after hours or on weekends.
- Changes in employee behaviour: Insiders who pose a threat may exhibit changes in their behavior such as increased stress, agitation or paranoia. They may also display signs of dissatisfaction or discontent, such as a sudden interest in job opportunities elsewhere or a lack of motivation.
- Use of personal devices for work purposes: Insiders who pose a threat may use personal devices, such as laptops or smartphones, to access sensitive data or conduct activities outside of their normal job responsibilities. This can be particularly concerning if the insider is trying to take sensitive data with them when they leave the organization.
- Access to sensitive data by third party vendors: Insiders who pose a threat may grant access to sensitive data to third party vendors, for reasons such as providing them with a competitive edge or for financial gain.
- Sudden financial strain: Insiders who suddenly face financial strain may become motivated by financial gain.
- Abnormal network behaviour: Insiders who pose a threat may exhibit abnormal network behavior, such as uploading
or downloading large amounts of data, connecting to unfamiliar servers, or using anonymous proxy servers.

Understanding the Motivations Behind Insider Threats

Insider threats can have a variety of motivations or can come about without any motivation at all. Understanding these is essential for identifying and mitigating risks within an organization. Some of the most common motivations behind insider threats include:
- Financial gain: Employees may be motivated to steal or sell sensitive data or intellectual property for financial gain, either for themselves or for competitors. This can include stealing trade secrets, customer lists or other valuable information.
- Revenge: Whether it be because they were passed over for a promotion or are having a bad experience at the company, a vengeful employee poses a significant threat.
- Ideological or political reasons: Employees may be motivated to harm the organization for ideological or political reasons, such as wanting to expose corruption or wanting to damage the company’s reputation.
- Lack of security awareness: Employees who are not trained and in organizations where security awareness is not a formal program may unknowingly put an organization at risk.
- Social engineering: with bad actors seeking multiple ways to penetrate an organization, it is possible employees become the target of and manipulated by social engineering tactics to steal sensitive information.
- Misplaced technology: some employees may be motivated by misplaced technology, this includes using unsecured personal devices or cloud storage services to store or share sensitive information.
By understanding the motivations behind insider threats, organizations can better identify and mitigate risks within their environment. They can also provide targeted training to the employees who are most at risk of falling for these motivations, this will help increase the security posture of the organization.
5 Signs Your Organization is at Risk of Insider Threats
1
Lack of Employee Training: Without a formal security awareness training program, employees and their organizations are at risk of innocent mistakes which open holes and gateways into the company.
2
Lack of Device Security Awareness: Employees are unaware of the steps they should take at all times to ensure that the devices they use (both company issued and BYOD) are secured at all times.
3
Unsecured Cloud Data: No ability to ensure employees cannot send highly confidential data to an unsecured location in the cloud, exposing the organization to risk.
4
Disregard for Security Policies: Employees break your organization’s security policies to simplify tasks and no monitoring exists to trap these breaches.
5
Failure to Keep Devices and Services Up-to-Date: Devices and services must be patched and upgraded to the latest versions at all times.
3 Identifying Common Risk Factors
Insider threats can occur in any organization, but there are certain risk factors that increase the likelihood of an incident. Some of the most common risk factors include:
- Access to sensitive data: Employees with access to sensitive data, such as intellectual property, financial data, or customer information are more likely to be involved in insider threats.
- High turnover rate: Organizations with high turnover rates may be more susceptible to insider threats if employees feel motivated to take sensitive data or other assets when leaving the company.
- Remote or hybrid work environment: With the shift to remote and hybrid work environments, organizations may have difficulty maintaining security controls and visibility into employee activity.
- Inadequate security training: Employees who are not properly trained on security best practices and protocols may be more likely to fall victim to phishing scams or other social engineering tactics.
- Lack of oversight: Organizations with a lack of oversight or monitoring of employee activity may be more susceptible to insider threats, as malicious or negligent actions may go undetected.
- High-stress environments: High-stress environments can lead to employees feeling stressed, undervalued and put at risk of committing an insider threat.
- Lack of security culture: organizations with a lack of security culture may be more susceptible to insider threats. This can occur when employees are not aware of the importance of data security, or if they do not understand the security policies in place.
By identifying common risk factors, organizations can better understand the areas of their environment most susceptible to insider threats and take appropriate mitigation measures.

How Insentra Indentifies Insider Risks
Our cyber risk assessment process is part of our Information Security Management System; which is ISO27001 certified. You could use an ISMS to manage risk, or you could use the NIST Cybersecurity Framework, the CIS Risk Assessment Method or any number of industry-focused frameworks which incorporate a risk assessment methodology. The framework you choose is not the most important part. What is important is that you pick one and start using it. Don’t reinvent the cybersecurity framework. Use a proven, trusted framework… the operative word being ‘use’.
Anything worth doing is worth doing badly. Start using it today. Start using it before you fully understand it. Make mistakes and learn from them. Using ISMS, we (Insentra and our interested parties) Identified our cybersecurity objectives and used those objectives to determine related risks. This method is holistic: We looked at the business as a whole and determined where Insider Threats could be dangerous for us and this is a cyclical, ongoing process. It is done on a regular schedule and also done whenever the organization undergoes significant changes.
By conducting regular business risk assessments and being aware of the indicators, motivations, and stages of an insider threat, organizations can better identify and mitigate risks. This will help them to protect their sensitive data, intellectual property, and other critical systems from insider threats.
Protecting Against Insider Threats
Unintentional Insider Threats - Security Awareness
When it comes to protecting your organization from cyber threats, there’s no denying the importance of investing in top-of-the-line security tools and hiring expert cybersecurity professionals. But even with all that firepower, your organization is only as strong as its weakest link – and that weakest link could, and often is, an employee who isn’t quite up to speed on the latest cyber threats. But there’s no need to panic – the solution is simple: education. By providing your employees with a comprehensive security awareness program, you’ll turn them into human firewalls – individuals who are equipped with the knowledge and skills to identify and fend off cyber threats. With a well-informed workforce, you’ll be able to sleep soundly knowing that your organization is as secure as it can be.
A comprehensive security training program can be a game-changer for your organization. By providing your employees with regular training and testing, you can ensure that they are well-informed and equipped to handle the latest cyber threats. This includes:
1
2
3
4

Intentional Insider Threats
Background checks to prevent bad actors from entering the organisation
Background checks can help to identify potential insider threats by providing information about an individual’s past actions and behaviors. This can include information about their criminal, employmentand financial history and other relevant details. By conducting a background check, organizations can learn more about an individual and make informed decisions about whether they pose a risk to the organization.
There are several reasons why background checks are important for identifying and mitigating insider threats. First, they can help to identify individuals who may have a history of criminal behavior or financial instability, which can be indicators of a potential insider threat. Second, they can help to identify individuals who may have a history of unethical or questionable behavior, such as violating company policies or engaging in fraud. Finally, background checks can provide orgnaisations with valuable insights into an individual’s overall character and trustworthiness, which can be important considerations when determining their suitability for a role that may involve handling sensitive information or assets.
When conducting a background check, it’s important not to let unconscious bias make you miss out on the right employee for the wrong reasons. It’s best to have a set of conditions you are trying to rule out in your ideal candidate pool. If possible, have someone who is otherwise not involved in the selection process sift through the background checks.
Create an amazing culture to prevent turning good people into bad actors
Creating a positive and supportive organisational culture is an underappreciated preventative step in preventing good employees from becoming bad actors. While background screening processes can help to minimise the risk of hiring individuals with malicious intent, it’s also essential to take proactive steps to support and nurture your employees.
At Insentra, we understand the importance of this preventative step and have made it a foundational aspect of our culture. We don’t have a traditional Human Resources department (what would Kant think of “Human Resources”?) we have a Vibe department that focuses on understanding and supporting the well-being of our employees.
You’re hiring people to perform their job but you can’t forget the first three words of this sentence. People have thoughts and feelings. They have highs and lows. They endure the full gamut of human experience all while helping you create your widgets and fill out your TPS reports. To get the most out of your people, you need to know how they are going and support them appropriately.
By fostering and supporting an organisational culture that values and nurtures its people, we create a positive work environment where people are happy and motivated to do their best work.

Numbers: We ask our crew to share their personal and professional well-being on a scale of 1-10 at the beginning of every meeting. This allows the participants to understand how one another are feeling If someone responds with a low number, the meeting leader will ask if there is anything we can do to help, allowing us to address issues and provide support before they turn into bigger problems. By allowing crew to pay attention to their emotions and take the time to process them, they can better understand their thoughts and feelings and work through any issues or challenges that may be causing them stress or discomfort. This can help reduce anxiety and depression and promote a greater sense of overall well-being. Because we know each other’s numbers, we can be flexible in our expectations and manage outcomes realistically.
Crew Talent Manager: At Insentra, we understand the importance of fostering a culture that values and nurtures its people. That’s why we have a dedicated role within our organization focused on encouraging individuals to be their authentic selves and create an environment free from fear, judgement and loneliness. This role is responsible for providing support, guidance and a safe space for our crew to share their thoughts, feelings and concerns, and to help them navigate through any challenges they may be facing. In this way, we are able to create an environment where our crew can thrive and be their best selves.
Third-Party
Third-Party Risk Assessment
How much risk your supply chain represents will depend on how integrated your third- parties are into your organization. You can achieve this using a supplier evaluation policy and procedure. We do this using a risk management platform which tracks the cybersecurity maturity of all of our Third-Parties. We also use a risk rating organization to ensure that the claims our Third-Parties make about their cybersecurity maturity are seen to be true in the real world.
Technical Controls
Many technical controls can be effective in mitigating all types of insider threats. Some options include:

- Access controls: These controls can limit which systems, data and networks an employee has access to based on their role and responsibilities. The tighter these controls are, the less information can be breached by
insiders either intentionally or unintentionally. - Encryption: Encrypting sensitive data can help to protect it from unauthorised access, even if it falls into the hands of an insider.
- Two-factor authentication: This adds an extra layer of security by requiring employees to provide a second form of authentication (such as a one-time code sent to their phone) in order to access sensitive systems. This makes it more difficult to unintentionally leak data and also impedes a collusive attack.
Zero Trust
- The Zero Trust approach is a terrific way to bolster our protection against insider threats. Several principles are central to a zero trust approach and all are relevant to Insider Threat protection:
- Verify before you trust: In a zero trust model, all access requests are treated as potentially malicious and are subjected to strict verification before access is granted.
- Limit access to the minimum required: The zero trust model emphasises the principle of least privilege where users are granted only the minimum level of access needed to perform their job duties.
- Monitor and enforce access controls: Access controls must be continuously monitored and enforced to ensure unauthorised access is detected and prevented.
- Secure all connections: In a zero trust model, all connections, both within and outside the network, are considered untrusted and are secured accordingly.
- Assume that all devices and users are untrusted: The zero trust model assumes that all devices and users, both inside and outside the network, are potentially malicious and must be treated as such.
The best way to get started with Zero Trust is through a Zero Trust Assessment.

Self-Healing Policy
“According to a study by IBM, human error is the main cause of 95% of cyber security breaches. In other words, if human error was somehow eliminated entirely, 19 out of 20 cyber breaches may not have taken place at all!” We’ve all heard that story where someone has made an error and the resolution is to review the countless audit logs to try and find the culprit. While ongoing review and education is important and a failure could be a great teaching moment, the implications to businesses where it involves data is risky and costly. What it was didn’t matter and there was a way to make course correction even where an error was made.
AvePoint Policies can prevent configuration drift with automated policy controls. Policies trigger alerts or roll-back of unauthorised changes and risky actions, including Teams name changes, external user settings and changes to permissions inheritance. Track improvements over time to prove your customers’ collaboration is secure.
How to Detect Insider Threats
Monitoring Behavior:

- Do you notice any unusual behavior from any employees, such as suddenly coming to work at odd hours or accessing information that is not related to their job duties?
- Have you noticed any employees exhibiting unusual stress or behavior changes, such as sudden changes in mood or attitude?
- Have you noticed any employees who seem disgruntled or who have expressed dissatisfaction with their job or the company?
- Have you noticed any employees who have had financial problems or have been the subject of financial investigations?
- Have you noticed any employees who have had conflicts with co-workers or management or who have a history of disciplinary action?
Asking these questions can help you identify employees who may pose a risk as insider threats. This should not be a kind of Spanish inquisition. If an employee is having troubles like the above, kind intervention could help them out of some serious problems and gain you even greater trust.
Monitoring Access and Activity
Monitoring using AvePoint Policies and Insights
By prioritising your critical issues for action by aggregating permission and activity data across your tenant, Managed Policies & Insights (PI) make it easy to monitor Microsoft 365 health. Providing tenant-wide security reports across your Microsoft cloud services, securing collaboration in Teams, Groups, SharePoint Sites and OneDrive has never been easier (or safer).
Managing your Policies & gaining Insights helps you to easily answer critical questions for your security team such as: Who has access to sensitive data? Have they accessed the data? Are any external users a threat? This will help you get insights to answer critical security questions about your Teams, Groups, Sites and OneDrive locations. You define what risk means to you, select the regulations or Microsoft 365 permissions and controls you care about most and PI will do the rest!

Conclusion
In conclusion, insider threats are a serious concern for organizations of all sizes and industries. From departing employees stealing trade secrets to negligent employees exposing login credentials, the potential impact of insider threats can be devastating. It is crucial for organizations to understand the different types of insider threats and take steps to prevent and protect against them. This includes conducting regular risk assessments, identifying indicators of insider threat, fostering a culture that values and nurtures its employees, and implementing security awareness and training programs. Furthermore, monitoring employee behavior and access to protected resources can aid in detecting anomalous activity and potential insider threats. By taking a proactive approach to insider threat management, organizations can minimise the risk and impact of these threats on their operations and customers.
Looking for a solution to help your organization prevent and mitigate insider threats? Look no further than AvePoint Policies and Insights. Our powerful tools and advanced analytics can help you identify and manage insider risk in real time, allowing you to take proactive steps to protect your sensitive data and intellectual property. From monitoring employee behavior to identifying potential threats before they escalate, our solutions can help you stay ahead of the curve and safeguard your organization against the costly impact of insider threats. Contact us today to learn more and take the first step towards greater security and peace of mind.
About Insentra
We Dare to be Different

Insentra is a collaborative IT Services partner delivering specialised Professional and Managed Services. Our Partner-centric model provides you direct access to industry expertise.
We believe great business relationships start with trust. We are 100% channel focused meaning we only transact and deliver services exclusively with our Partners.
Our dedication to you is based on our vision to be the number one channel services company on the planet. We do this by being the best version of ourselves, creating an outstanding environment for our team, loving the work we do and amazing each other and our partners in every way.
We are and always will remain a Partner obsessed company.
About Avepoint
Collaborate with Confidence

AvePoint provides the most advanced platform for SaaS and data management to optimize SaaS operations and secure collaboration.
More than 9 million cloud users rely on our solutions. Our SaaS solutions are also available to managed service providers via more than 100 cloud marketplaces, so they can better support and manage their small and mid-sized business customers.
Founded in 2001, AvePoint is a five-time Global Microsoft Partner of the Year and headquartered in Jersey City, New Jersey. For more information, visit https://www.avepoint.com.
DOWNLOAD BROCHURE

THANK YOU FOR YOUR SUBMISSION!





