A recent feature release, in public preview by Microsoft, is a major step to simplifying and improving the B2B authentication experience with Azure AD. This feature now makes it possible for an Azure AD tenant to accept authentication tokens from a different Azure AD tenant. To find more information please refer to the Microsoft documentation on Cross-tenant access with Azure AD External Identities and John Savill has an excellent YouTube video, on Azure AD Cross-Tenant Access deep diving into how the solution works.
I am sure many of us are familiar with the pain of managing multiple different MFA registrations when collaborating with customer tenants. Each individual tenant requires its own MFA registration, individual sign-ins to each tenant, and the list goes on.
Well now, with cross-tenant access policies becoming available, we have the option of configuring policies that allow our Azure AD tenant to accept user sign-ins, and more importantly authentication tokens, from businesses we work with, or share data with on a regular basis, that also have an Azure AD tenant.
The cross-tenant access policies preview features can be found in the Azure AD portal, under the external identities blade.
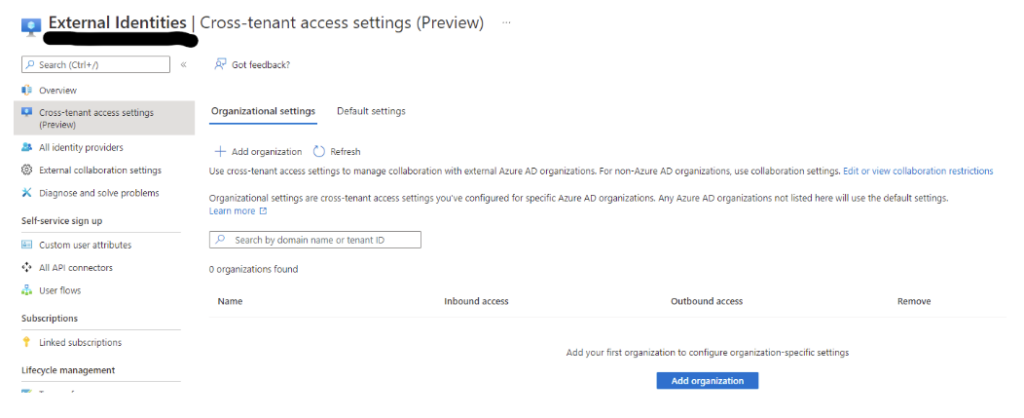
Once an organization is added, using either the tenant ID or.onmicrosoft.com organisational name, the below settings can then be configured for both inbound and outbound authentication. These settings can be assigned to all users or apps, or selected users, groups, or apps, however this requires obtaining the object id’s from the partner organization to do so.
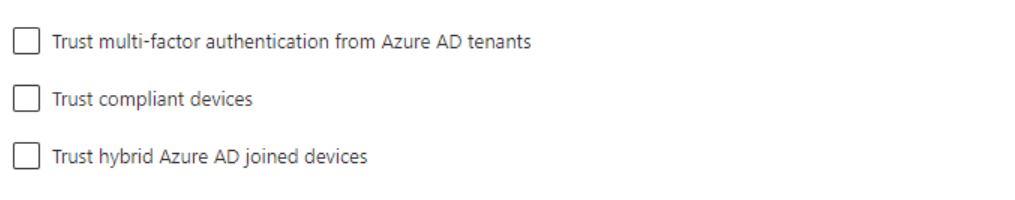
By enabling the above configuration to another Azure AD tenant, authorized B2B users from the partner tenant will now have a single sign-on experience when accessing resources in our tenant.
The scenario I have described is an inbound concept, however this will also work when thinking about an outbound scenario.
If we have a partner business that requires us to frequently access resources in their tenant, then the same configurations can be applied in the partner’s Azure AD tenant, to enable single sign-on for our users, to our partner’s resources.
A crucial point that needs to be made here, is that cross-tenant access policies are an authentication solution only, at this point in the preview, they do not provide access to resources in either ours, or our partner’s tenants. Manual configurations for resource permissions still need to be applied for the guest accounts to be able to access said resources.
In saying that, this is an important first step on that journey and will still provide relief for many of us.
I hope this provides some valuable information for some of you out there!










