Persistent firewall rules in Server 2016 & Windows 10
Firewalls are implemented in an attempt to reduce the impact of malicious attacks across an organisation, but they always come at a price. This can be from significantly increasing the configuration requirements across an environment to the point where everything is locked down so tight it makes implementing solutions cumbersome and troubleshooting even harder, to impacting performance of the systems where it is enabled.
In the many deployments we deliver each year, we recommend the Windows Firewall (now known as ‘Windows Defender’) service is enabled and active with rules on the machines to allow communication between them and the other services they interact with, although not so locked down there can be absolutely no other communications.
With the latest release of Microsoft Operating systems platforms, a key feature has been introduced called ‘App packages’, or ‘Modern Apps’, which come bundled with the O/S and are part of the Microsoft Modern App strategy. These new applications have introduced an issue within the Windows Defender service that can cause significant performance impact to the hosting systems, or connecting users, as well as impacting any troubleshooting of the firewall service.
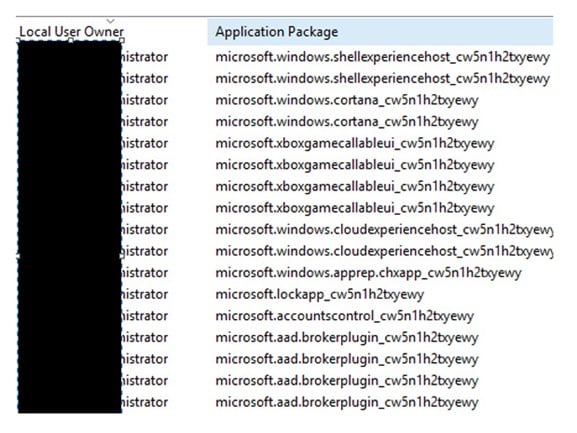
Every App Package has a unique identifier (SID) which is used by Windows defender to filter the modern apps. This can be on done based on UserID, Protocol or other conditions. This sounds logical and the package by package feature allows for great targeting of the firewall rules, and the App Packages automatically write their own rules to the firewall for each application at the start of the user session.
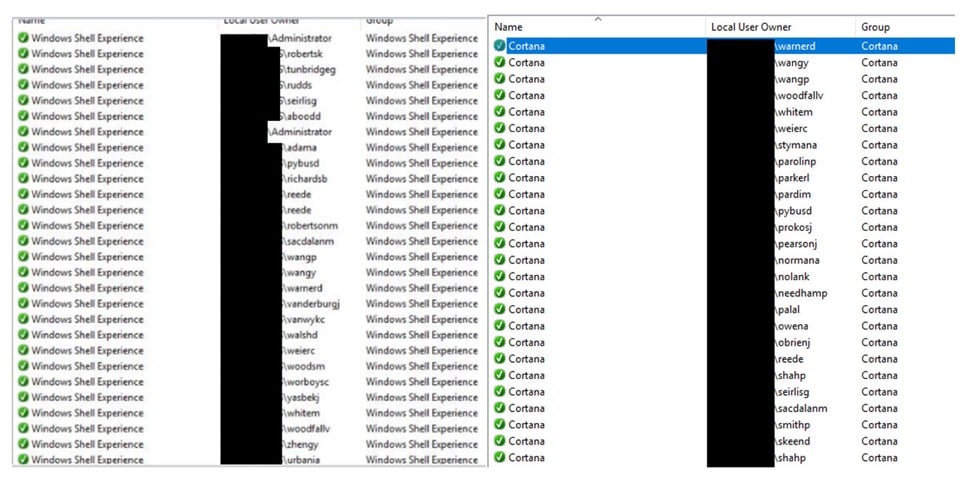
The issue is that the App packages don’t remove the rules that they placed in to the firewall at the end of a user session, nor do they reuse the rules on a second login of the same user. This can result in a single user creating hundreds of rules in the firewall for applications that are not required, worse still is that they are Any/Any rules.
Running the Xbox live services on a Windows 2016 server is unnecessary, unless your gaming laptop has just died the night before a Fortnight friend battle so removing these seems sensible. On all deployments of Citrix we implement, we use the Citrix optimiser toolkit (https://support.citrix.com/article/CTX224676) on the target servers and disable a number of the services that don’t need to be active in Enterprise environments, but there are a number that need to be there which include individual user-based firewall rules for the app package.
For most systems, the optimisation is enough to limit the impact of the user rules, but in some instances this is not the case. In Citrix XenApp or Microsoft RDS systems, where a high number of users connect to single server, the number of rules created can get out of control and impact performance.
This may not result in a major performance impact straight away on a system but has the potential to impact systems over time as well as impact troubleshooting issues as the rules are not removed by the OS when the user’s logout, or if the same user logs in to the server again.
An example of the potential impact is that the svchost.exe process consumes an excessive amount of compute on the server in dealing with all the rules it has to process.
Microsoft have not announced a ‘patch’ for Windows 10 and Windows Server 2016, but we are monitoring the blogs and feeds and hopefully they will release something later this year. For environments needing to clean up the rules now, there is little option other than running a scheduled task with a PowerShell script.
To get a picture of what apps are automatically creating firewall rules , open “C:WindowsSystemApps”
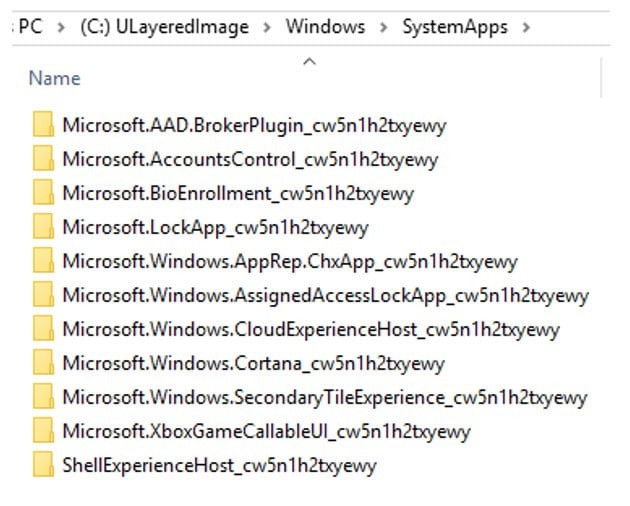
Four of the main culprits for the bloat of rules are:
- “Contact Support”: related to the Metro app “Contact Support which could be used to ask for help from Microsoft directly. If disabled, this app may not work
- “Search”: related to the Cortana app. If disabled, Cortana may not
- “Work or school account”: related to the Azure AD account. If disabled, the Azure AD accounts may not work
- “Your account”: related to the cloud service of your account (Microsoft account sync settings between machines)
Based on the above example, each time a user logs in they will have 11 firewall App rules created which will not be deleted once the user logs out. So, what do you do?
Determine the installed services from the SystemApps folder and edit your script to find and delete rules as required. Here is an example script:
Get-NetFirewallRule -DisplayName “*Microsoft*” | Remove-Netfirewallrule
Get-NetFirewallRule -DisplayName “*xbox*” | Remove-Netfirewallrule
Get-NetFirewallRule -DisplayName “*Parental*” | Remove-Netfirewallrule
Get-NetFirewallRule -DisplayName “*ShellExperience*” | Remove-Netfirewallrule
Get-NetFirewallRule -DisplayName “*Windows*” | Remove-Netfirewallrule
Feel free to use the above code if you want to, and you can’t wait for a fix from Microsoft, but please ensure you test this thoroughly in your environment to make sure it doesn’t impact anything critical.











