I have been working on several M365 related security projects recently. These primarily consisted of increasing the organisations security posture and working towards a Zero Trust architecture. For everything you need to know about Zero Trust please take a look at the Insentra Ultimate Guide to Zero Trust
REQUIREMENT
The customer (Contoso) is involved in external collaboration with many partners. This has become a critical business requirement for Contoso. Contoso have heavily invested in their Information Protection strategy, which Insentra assisted with, so they were happy they had the correct mechanisms in place to secure and protect their data. As a result, Contoso wanted to manage the method in which external users can access Contoso M365 services while protecting their data. Contoso wanted to allow external users to access their M365 services by only using a browser, all mobile apps and desktop clients should be blocked.
To achieve this requirement, the solution was to create a Conditional Access policy. As always, there are a few prerequisites that are needed before Contoso can achieve the desired solution
- Azure AD Premium P1
SOLUTION
To implement this solution you need to have one of the below Azure AD admin roles assigned to your account
- Conditional Access Administrator (least privilege)
- Security Administrator
- Global Administrator
All the configuration takes place within Microsoft Entra admin centre > Protect & secure > Conditional Access. To create this policy, please follow the below steps
- Create a new policy
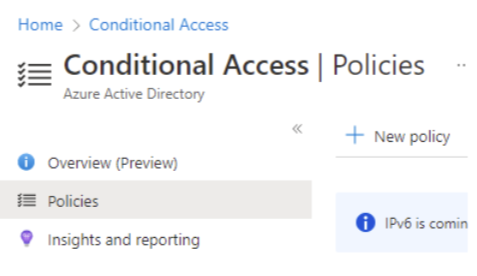
- Give the CA policy an appropriate name, preferably in alignment with Microsoft CA naming conventions, for example, “CA001: BLOCK – Block external users from downloading files in Office 365”
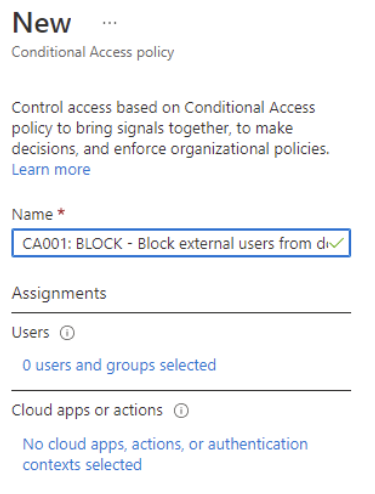
- Within Users > Assignments select “Guests or external users” and all for “Specify external Azure AD organisations (preview)”

- Within Cloud apps or actions > Select apps and choose “Office 365”. This will apply to all M365 services, if you require something more granular, for example, Exchange Online, then just select Exchange Online
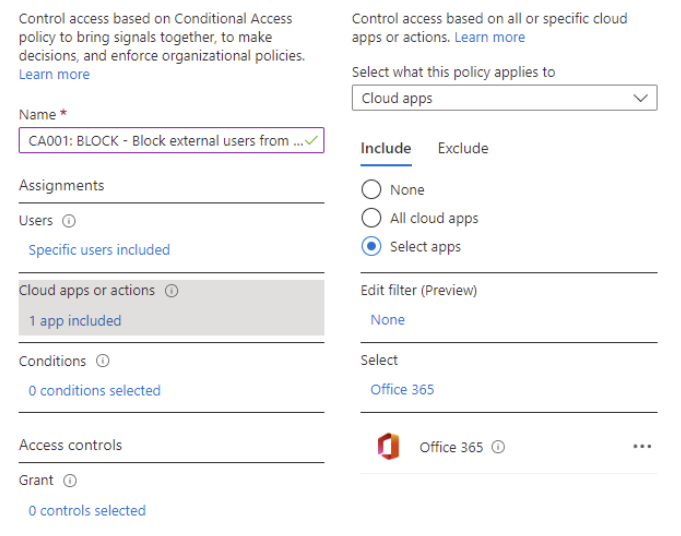
- Within Conditions > Client apps select the following options
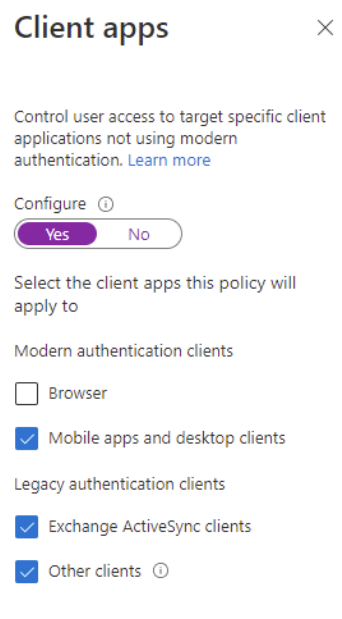
- Lastly, within Access controls > select Block
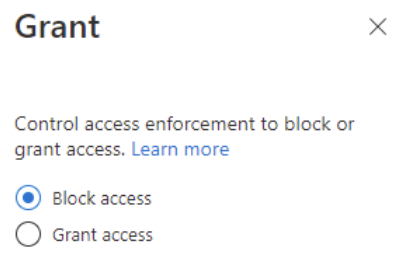
That is you good to go! I would recommend enabling this policy as “Report-only” for a few days and keep an eye on the logs to ensure the CA policy is behaving as you expect it. Once you have confirmed The CA policy is meeting your expectations, you can enable the policy to “On” and external users can now only access M365 services using a browser which supports Modern Authentication.
Hopefully this has been informative and helpful! If you need any further clarification, or a no thrills chat, contact us at Insentra or read more of my Insentra Insights.
CONCLUSION
In conclusion, the successful implementation of a Conditional Access policy allowed Contoso to meet their critical business requirement of securing their data while allowing external users to access M365 services via a browser. With Insentra’s assistance, Contoso was able to enhance their security posture and move towards a Zero Trust architecture. If you need similar help or want to learn more, contact Insentra or read their Insights. Don’t hesitate to take steps to strengthen your organisation’s security today.
RELATED ARTICLES
How to allow only work account access to apps using Intune
Securing and Optimising Access to Azure Storage Accounts with Azure Endpoints










