Whenever someone brings up PIM and PAM, I can’t help but smile and think of the kid’s TV show Bill and Ben (not the original…I’m much too young for that!) I’m not sure if the use of alliteration was a conspicuous decision, but it sure helps with remembering these solutions. The trick is trying to figure out which is which and what they do.
Microsoft provides in both their on-premises Active Directory and in Azure Active Directory (AAD). When implemented, both solutions go a long way towards enforcing zero standing access. Zero standing access is a principle which users do not have admin privileges by default, and when permissions are provided it is the bare minimum and for a limited time. While the on-premises versions require a fair amount of investment (in both time and infrastructure), in AAD they are relatively simple to enable and configure, and that is the focus of this blog.
The first thing we need to understand is what the differences are between PIM and PAM. PIM provides your organisation with the ability to discover, manage and monitor admin access across Azure AD, Azure and other Microsoft Online Services like Office 365 or Intune. PIM is scoped at the role level, so you might have your Global Admins request those privileges at the time they need them.
PAM provides similar management functionality, but at the task level. An example might be that you want to restrict the ability to create forwarding rules on mailboxes. In this case you can apply a policy which restricts admins from performing this task until an approval workflow has been completed. One of the big downsides of PAM in AAD is that it is currently only available for tasks in Exchange Online, although other workloads are on the roadmap.
To utilise these services in Office 365, you will need to have Azure AD Premium P2, Enterprise Mobility + Security (EMS) E5 or Microsoft 365 E5 licenses. If you are just looking to implement PAM; you will need Office 365 E5 licenses.
So, let’s take a high level look at implementing these services. I’ll start with PIM as it’s the solution which will cover more of your Office 365 solutions than PIM currently does.
PIM
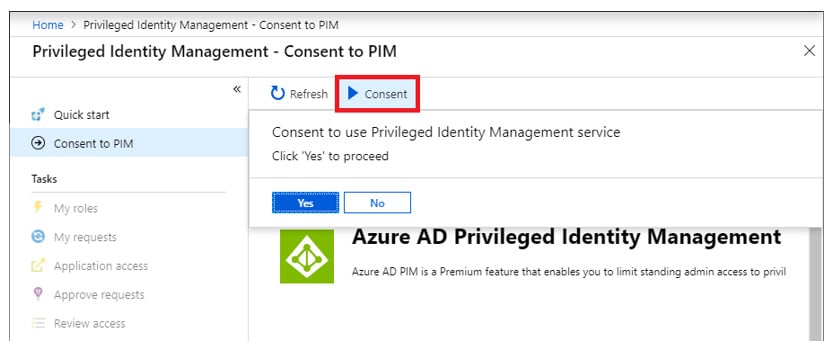
Firstly, PIM must be enabled via the Azure AD Privileged Identity Management service in the Azure portal. Clicking the “Consent” button will enable the service in your tenant. The person who performs this action is automatically assigned the Security Administrator and Privileged Role Administrator roles in AAD. Once the service is enabled, you also need to allow PIM to manage Azure AD roles. This is done by clicking the “Yes” option to sign up for PIM for Azure AD roles.
Each of the admin roles PIM can manage are able to be configured with the following options:
- Activation duration – the period of time a role is activated once approved up to a maximum of 72 hours
- Notifications – whether the admin is notified or not that their admin access has been activated
- Incident/Request ticket – whether an incident or request ticket number is required to be entered when requesting activation of the admin role
- Require approval – whether approval is required to activate the role and who those approvers or approver groups are
Once the roles have been configured, it’s now just a matter of adding your users to the role in PIM and selecting “eligible” as the activation type. Any users who were added to the role prior to PIM being enabled can be converted from permanent to eligible at this point as well. . One thing I strongly suggest is that you don’t go overboard with PIM. If users need an admin role for their day-to-day job and using PIM would greatly reduce their productivity, you should consider adding them to the role permanently.
For users to activate the role they need, they simply go to the PIM service in the Azure portal, click on ‘My roles’ and activate the appropriate role. Once the access has been approved the role will be activated for the configured duration without the need to log off and log back in.
The other benefit of PIM for your organisation is the monitoring function. You can use PIM to create access reviews for privileged Azure AD roles. This allows you to create a process where eligible and permanent members of a role are reviewed either by the member themselves or by another person or group. You can also configure recurring access reviews which occur automatically.
Other monitoring tasks in PIM include alerting (for example, administrators who aren’t using their privileged roles, potential stale accounts in a privileged role etc) and auditing.
PAM
As we talked about before, PAM takes a similar outlook to authorising role-based admin privileges and applies it at a more granular level to specific tasks. At this stage those tasks are restricted to Exchange Online tasks. While Microsoft call this service “Privileged access management in Office 365,” PAM still has a long way to go before it works across all the services in Office 365.
The first step in enabling PAM is to set up a mail enabled security group to which will contain members who can authorise PAM access requests. Once you have the group created, you can turn on PAM via the Microsoft 365 admin centre, Settings, Security and Privacy. During the initial set up you will need to select the group you created as the default approvers group.
If using PowerShell to enable PAM (Enable-ElevatedAccessControl), you can also define accounts which are not subjected to PAM policies, such as accounts used to run PowerShell jobs in the background.
With PAM now enabled in your tenant you can now create the PAM policies. PAM policies can be configured with the following options:
- Policy type – available options are task, role or role group
- Policy scope – currently the only option is Exchange
- Policy name – shows the restricted tasks depending on what policy type is selected
- Approval type – manual or auto. Auto approvals are used for high-use tasks which you would like audited, but you don’t necessarily need to have an approver grant access
- Approval group – mail enabled security group containing members who will be able to approve or deny requests for the given policy
Once the policy is in place, admins will now need to request access to perform the task, either through the Microsoft 365 Admin Centre or via PowerShell (New-ElevatedAccessRequest). Members of the applicable approval group will be notified of the request and they will be able to approve or deny it either via the Microsoft 365 Admin Centre or via PowerShell (Approve-ElevatedAccessRequest or Deny-ElevatedAccessRequest). If an approver doesn’t action the request within 24 hours, the request expires, and the admin will be required to submit a new one.
This is a high-level outline of PIM and PAM in Office 365, and I would encourage all organisations to work towards having zero standing access as much as possible in their Office 365 tenant, by implementing PIM at a minimum.
As always, reach out if you have any questions or need some assistance.











