I have to tell you a secret…Symantec Data Loss Prevention is my favorite Symantec Technology (don’t tell anyone). One of the aspects of Symantec DLP I think is the most powerful is how flexible it is. However this comes with a warning – as we all know with great power comes great complexity!
A couple of weeks ago I ran into a bit of a challenge at one of our clients using Symantec Data Loss Prevention 15 with Endpoint Prevent. My client had deployed the DLP agent out to a fairly large set of pilot users. All the DLP agents were reporting to the same detection server, therefore all were affected by the same policy group. The challenge started with how to configure DLP to scan some endpoints and avoid scanning others…and to do it all based on the logged in user’s Active Directory security group membership?
The first step was to set up Endpoint Prevent with two Agent Configurations. One which scanned all channels and one that scanned no channels:
- DLP Agent Configuration – Full Protection
- DLP Agent Configuration – No Protection

I created two Agent Groups and applied one Agent Configuration to each Agent Group:
- DLP Agent Configuration – Full Protection -> PCI Users – AD
- DLP Agent Configuration – No Protection -> Default Group
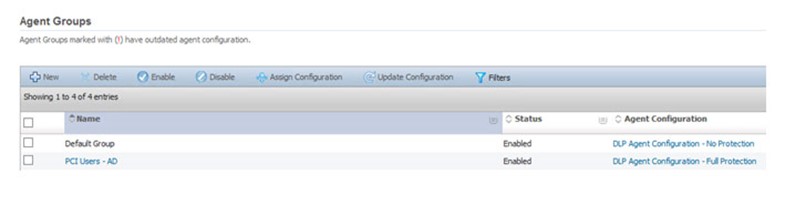
The question then had to be asked, how can we ensure all DLP agents are added to the correct Agent Group using an AD security group? The answer was to have the PCI Users – AD group evaluate an Agent Attribute. All other DLP agents would end up in the Default Group.
The challenge is currently there is no documented way to add DLP agents to an Agent Group using Active Directory security group. I will be honest, it took me about 8 hours to figure it out, but it was well worth it.
Pro Tip: Learn how to do LDAP queries! LDAPAdmin is your friend!
- LDAP Query Basics
- Symantec Data Loss Prevention Administration Guide (Version 15.0): Creating and managing agent attributes, p1915
Requirements
- Active Directory security group created.
- Active Directory security group DN, Example: CN=PCI_Users,DC=acme,DC=net,DC=au
- Users added to the Active Directory security group.
Method
1. Open the Enforce Console.
2. Hover over System, Agents and click on Agent Groups.
3. Click on Manage Agent Attributes (top right corner of the screen).
4. Click New.
5. Add the following information:
a. Name: User DN
b. Description: This Agent Attribute filters for the distinguished name of the logged in user.
c. Select Domain: User Domain
d. Search Filter: (sAMAccountName=$LoggedinUser$)
e. Active Directory Attribute: distinguishedName
Explanation: This filter searches Active Directory for the user object associated with the logged in user on the endpoint and returns the logged in user’s distinguishedName. The user’s distinguishedName is a requirement for the second Agent Attribute.
f. Click Save.
6. Click Apply Changes
7. Click New.
8. Add the following information:
a. Name: PCI User Group
b. Description: This Agent Attribute filters for the common name of the Active Directory security group, if the logged in user is a member.
c. Select Domain: User Domain
d. Search Filter: (&(objectclass=group)(distinguishedName=CN=PCI_Users, DC=acme,DC=net,DC=au)(member=$User DN$))’
e. Active Directory Attribute: cn
Explanation:
i. distinguishedName is the DN of the Active Directory security group that users are added to if they need to be scanned for sensitive data.
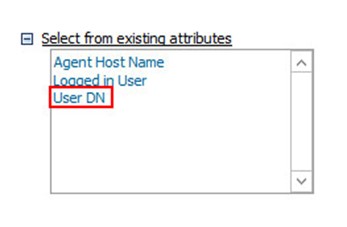
ii. $User DN$ is a variable which was created in the first agent attribute above. Add it by clicking on Select from existing attributes and selecting User DN.
iii. If the logged in user on the endpoint is a member of the Active Directory security group, the filter returns the value for cn which is PCI_Users. PCI_Users will be used in the Agent Group called PCI Users – AD.
9. Click Save.
10. Click Apply Changes.
11. Hover over System, Agents and click on Agent Groups.
12. Click on PCI Users – AD.
13. Click on the Select Agent dropdown and select PCI Users Group (Supported on Windows endpoints).
14. In PCI Users – AD, add the cn from above: PCI_Users
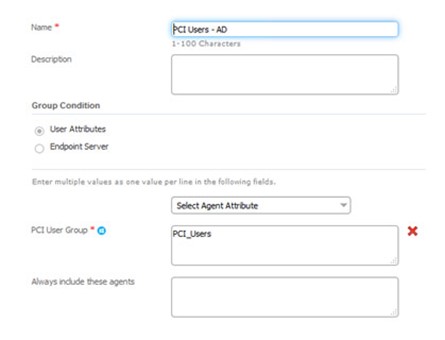
15. Click Save.
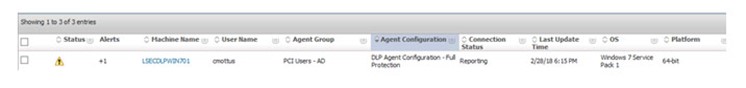
My user (cmottus) is a member of the PCI_Users Active Directory security group. When I start my endpoint and log in, the DLP agent evaluates all the Agent Attributes. It determines that my user is a member of the PCI_Users Active Directory security group, therefore my computer is put into the PCI Users – AD Agent Group.
Troubleshooting Tools
- LDAPAdmin – For testing Active Directory Filters (http://www.ldapadmin.org/)
- AttributeQueryResolver – Symantec Data Loss Prevention Administration Guide (Version 15.0): Verifying attribute queries with the Attribute Query Resolver tool, p1918.
Warning: When you add Agent Attributes to DLP, all Agent Attributes are evaluated by all DLP agents. DLP agents with logged in users who are not members of the AD security group will receive an warning:

At the time of writing, there is now way to silence this warning.











