In this blog, we’re diving into the intricate world of Microsoft Azure Conditional Access. Imagine Conditional Access as the protective shield guarding every authorisation attempt within your directory. Now, while it offers a plethora of controls, the question arises: How do we ensure we’ve covered all the bases and left no room for security gaps?
Let’s explore Conditional Access and discover effective ways to identify and address potential vulnerabilities in your organisation’s security.
Conditional Access
Conditional Access is your go-to armour when it comes to fortifying the access points in your Azure directory. It allows you to scrutinise user attributes, group affiliations, guest statuses, app-specific details, actions being performed, and even factors like user risk and sign-in risk.
The beauty of Conditional Access lies in its ability to craft policies that dictate responses—be it blocking unauthorised attempts or allowing access with specific controls in place, such as Multi-Factor Authentication (MFA) or device health checks.
THE CHALLENGE: GAPS IN PROTECTION
The challenge arises when we ponder the possibility of missing out on a specific combination of factors. What if you forgot to block certain actions or security threats? This creates a gap in your coverage, leaving a potential vulnerability unnoticed. So, how do we identify these gaps and fortify our security measures?
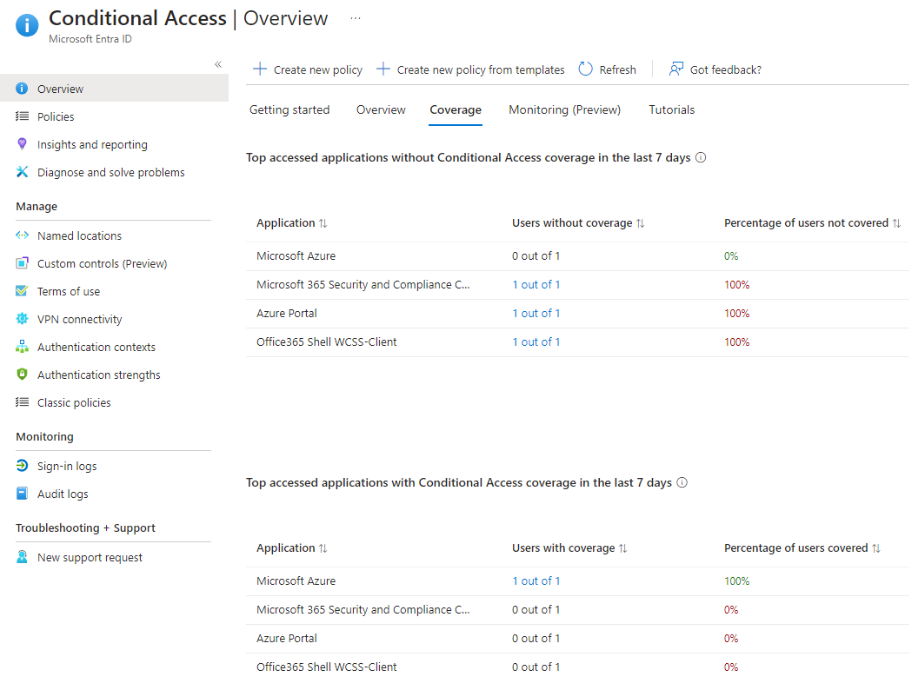
COVERAGE IN CONDITIONAL ACCESS
One way to start is by heading to the Azure portal. Under Conditional Access or the overview section, explore the “Coverage” tab. Here, you’ll find insights into the top access applications lacking Conditional Access coverage. This is a quick way to spot potential gaps in the last seven days and prioritise addressing them.
GAP ANALYSER WORKBOOK
For a more detailed analysis, turn your attention to the Identity Gap Analyser Workbook. This powerful tool allows you to delve deeper into the nuances of your Conditional Access strategy. Modify the time range to suit your needs and explore key aspects such as Legacy authentication usage, unprotected applications, compromised user sign-ins and more.
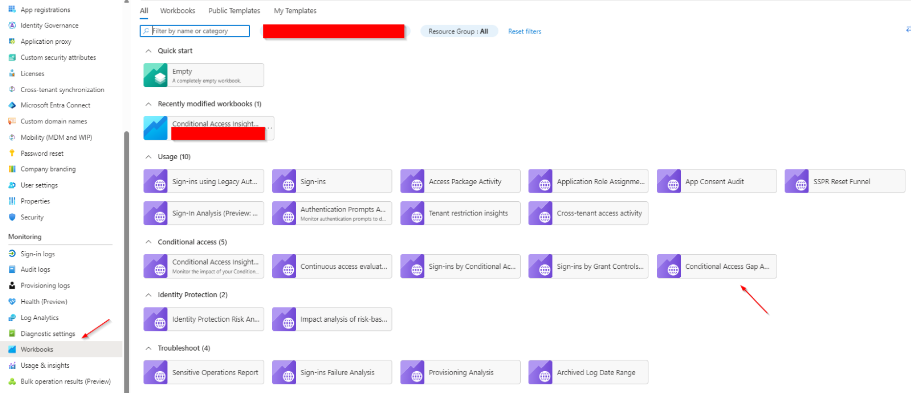
The Gap Analyser within the workbook provides a comprehensive view of potential vulnerabilities. Are you unknowingly allowing Legacy authentication? Are there applications lacking protection? Is your user base exposed to compromised sign-ins? These are critical questions, and the Gap Analyer equips you with the answers.
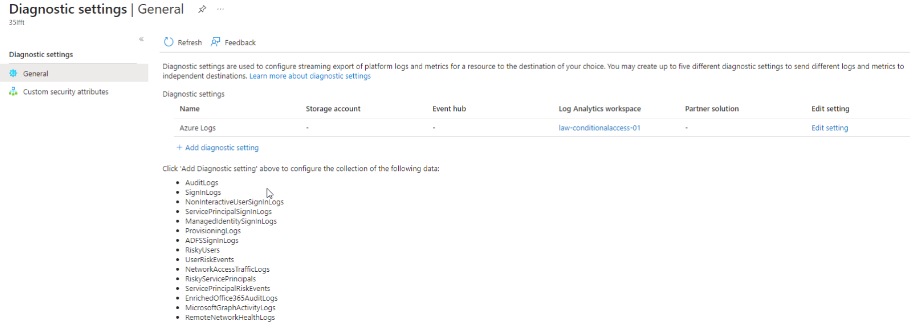
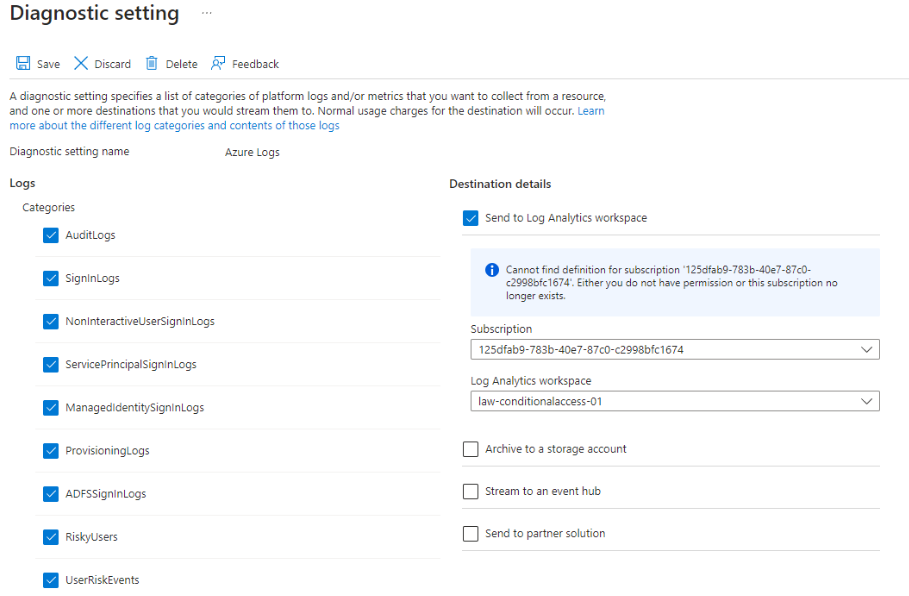
REQUIRED LOGS
To make the most of the Gap Analysis, ensure you’re sending sign-in logs to a Log Analytics workspace. This step is crucial for the workbook to fetch the required data. Set up diagnostic settings to include sign-in logs, and you’ll have a treasure trove of insights at your fingertips.
POLICY TEMPLATES
Armed with the knowledge of the gaps in your Conditional Access, it’s time to take action. Azure now offers Policy Templates, saving you from creating policies from scratch. These templates cover various scenarios, from remote work to securing administrators and addressing emerging threats. Pick a template that aligns with your needs and customise it accordingly.
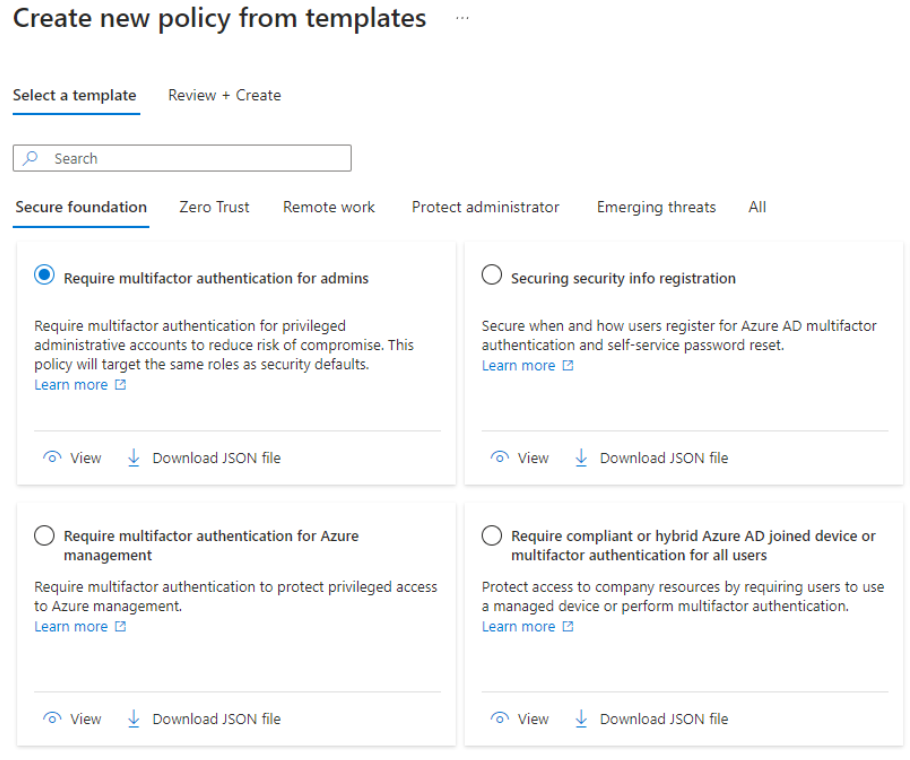
GRADUAL DEPLOYMENT OF NEW POLICY
As you embark on implementing a new Conditional Access policy, be sure to adopt a cautious approach. Start by enabling it in “report only” mode. This allows you to assess the impact the policy would have without affecting users negatively. Examine the logs, understand the implications, and once confident, proceed with gradual deployment.
STRENGTHEN YOUR CONDITIONAL ACCESS POLICY
In the ever-evolving landscape of cybersecurity, finding and addressing gaps in your organisation’s Conditional Access is paramount. Microsoft Azure provides powerful tools to not only identify vulnerabilities but also to fortify your defences effectively. Whether it’s through quick coverage checks or in-depth gap analysis, the key is to stay vigilant and ensure your security measures evolve with the dynamic threat landscape.
If you need assistance in strengthening your security architecture, Insentra is here to help. Check out our Secure Workplace services or contact us today.











