In today’s digital world, user authentication is crucial for ensuring the security of web applications. While some web applications support Kerberos Single Sign On (SSO), others rely on OpenID and SAML authentication. This is where Red Hat SSO (RH SSO) comes in, providing a solution to federate users from various sources.
In this blog, we will explore how to use RH SSO and Red Hat idM (FreeIPA) to authenticate web users. RH SSO, a JBoss application, offers Single Sign On for online applications with OpenID and SAML2. One of its standout features is the ability to use Kerberos tickets to replace password-based authentication, adding an extra layer of convenience and security.
What is RH SSO
Red Hat SSO is a JBoss application that can federate users from a variety of LDAP servers, including 389-Server, OpenLDAP, and Microsoft Active Directory. It provides Single Sign On (SSO) for online applications with OpenID and SAML2.
The ability to use Kerberos tickets from clients to replace password-based authentication is a very neat feature.
Requirements
The following guide is based on the commercially supported products provided by Red Hat, namely RHEL8, Red Hat SSO and Red Hat idM. It is expected that this guide will also work with the upstream products: Keycloak (Red Hat SSO) and FreeIPA (Red Hat idM).
- A base installation of RHEL8
- A subscription for RHEL8 and JBoss EAP
- A configured and working FreeIPA/Red Hat IdM environment
- An instance of WordPress (optional)
My setup consists of:
- Three (3) idM servers (one primary and two replicas)
- Two (2) RH SSO servers in a HA configuration (the configuration is not in scope for this document)
- Two (2) mariadb/galera servers in HA configuration for RH SSO
The following system specs have been used for the setup presented above:
- CPU: 4vCPUs
- Memory: 4GB
- Disk: 60GB
Integration with Red Hat idM
Ensure your SSO server is enrolled in the idM domain.
We need to do some preparation work:
- Create Kerberos Service Principal for the HTTP server
- Fetching the Kerberos Keytab
Create the Kerberos Service Principal
- Log into the RH SSO server
- Obtain the admin kerberos ticket
subscription-manager register
subscription-manager attach --pool=pool_number kinit admin
klist - Create Service Principal
ipa service-add HTTP/rhsso01.example.net - Download the keytab
ipa-getkeytab -p HTTP/rhsso01.example.net -s idm01.example.net -k /etc/krb5-keycloak.keytab - Set correct permissions for the keytab
chown root /etc/krb5-keycloak.keytab
chgrp jboss /etc/krb5-keycloak.keytab
chmod 640 /etc/krb5-keycloak.keytab Create the user for ldap bind
- Log into one of the idM servers
- Run the following ldapmodify command
[root@idm01 ~]# ldapmodify -x -D 'cn=Directory Manager' -W <<EOF
dn: uid=ssobind,cn=sysaccounts,cn=etc,dc=example,dc=net
changetype: add
objectclass: account
objectclass: simplesecurityobject
uid: system
userPassword: tower123
passwordExpirationTime: 20320101000000Z
nsIdleTimeout: 0
EOF The above command has to be modified to meet your requirements, where:
| DN | Description |
| uid=ssobind | This is the bind user. It can be whatever you choose |
| dc=example,dc=net | This is your domain |
| userPassword | This is the password. Make it simple. |
| passwordExpirationTime | Depending on when you are reading this … you might modify this date |
- Verify the bind user and the password
ldapsearch -D "uid=ssobind,cn=sysaccounts,cn=etc,dc=example,dc=net "
-W -h idm01.example.net
-b "cn=accounts,dc=example,dc=net"
uid=nesiuser01 We are ready to create the User Federation
Create RH SSO User Federation
- Log into RH SSO using browser
- Select the Realm you want to modify (top right corner)
- Click on User Federation and click Add Provider
- Fill out the form as following:
| Option | Setting |
| Edit Mode | READ_ONLY |
| Vendor | Red Hat Directory Server |
| Username LDAP Attribute | uid |
| RDN LDAP attribute | Uid |
| UUID LDAP attribute | ipaUniqueID |
| User Object Class | inetOrgPerson, organizationalPerson |
| Connection URL | ldaps://idm01.example.net |
| Users DN | cn=users,cn=accounts,dc=example,dc=net |
| Authentication Type | Simple |
| Bind DN | uid=ssobind,cn=sysaccounts,cn=etc,dc=example,dc=net |
| Bind Credential | your password |
| Allow Kerberos authentication | On |
| Kerberos Realm | EXAMPLE.NET |
| Server Principal | HTTP/rhsso01.example.net |
| Keytab | /etc/krb5-keycloak.keytab |
| Use Kerberos For Password Authentication | On |
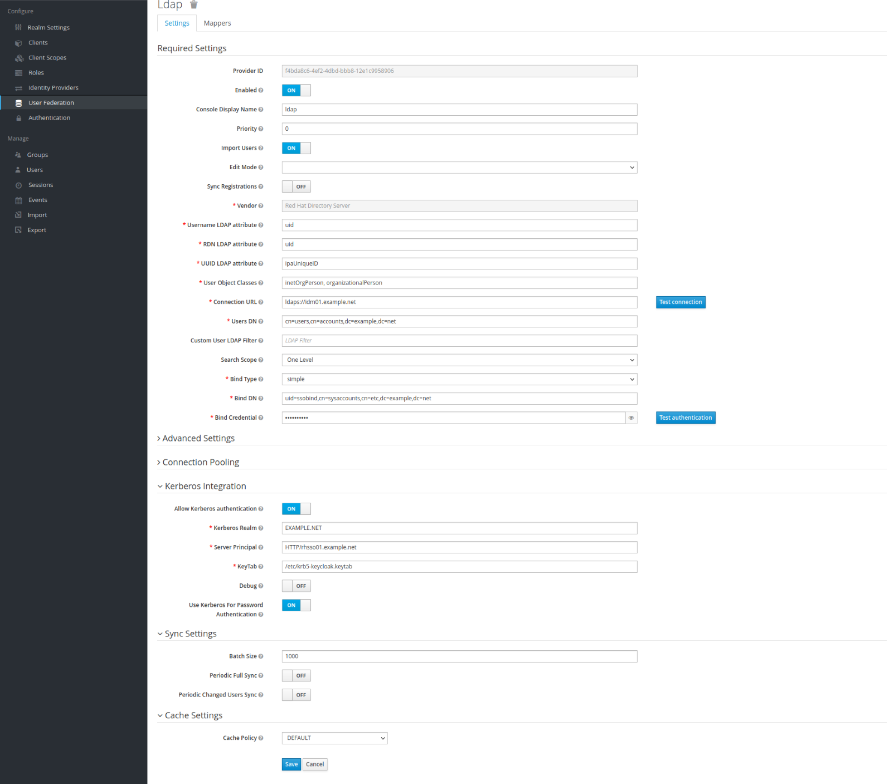
- Save the configuration
- Click on Test Connection (next to Connection URL) to verify connection to ldap server
- Click Test authentication to verify the bind user/password
- Click on Synchronize all users. If you have any users in the idM, you should be able to see something like:
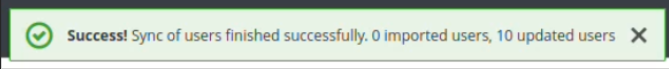
- Navigate to Users and click ‘View all users. You should be able to see all the imported users
If you want to learn more about RH SSO User Federation with Red Hat idM and how it can benefit your web applications, contact us today! Our team of experts is ready to assist you in implementing this solution and enhancing the security of your digital assets.