Ever had a recurring problem across your Windows PCs, that while simple to resolve, is highly time-consuming? Perhaps you have developed a procedure for your Service Desk to resolve the problem, or you’ve developed a scripted solution to further simplify triage. However, even these structured steps take time. What if we could take this a step further and automate the detection and resolution of recurring issues?
Let’s look at the case I handled, for example. A previous customer was working through the acquisition of multiple organisations, which included onboarding Windows PCs into Intune and Defender for Endpoint. This process significantly increased the total number of client applications within the environment. It also highlighted considerable variance in the configuration of Windows PCs and patch management of Windows and client applications.
As this organisation operated in a highly regulated industry, there was a requirement to manage security vulnerabilities quickly and with minimal user interruption. This involved a myriad of remedial activities that needed to be actioned rapidly. How were they able to address these issues swiftly without consuming too much manpower?
Enter Intune Remediations.
What is Intune Remediations?
Intune Remediations, previously known as Proactive Remediations, allow for administrators to automatically detect and resolve common problems across Intune-managed Windows PCs. This allows you to respond to and resolve requests in hours (not days) and develop a framework to standardise the configuration and deployment of Remediations in the environment.
How to Deploy Intune Remediations
To deploy Remediations within your Intune tenant, users will require:
- Microsoft 365 F3, E3, or E5
- Microsoft 365 A3 or A5
- Windows 10/11 Virtual Desktop Access (per user)
Microsoft details the licensing requirements in the Remediations documentation as well: Remediations – Licensing | Microsoft Learn
As of writing, Remediations is not available to users with Microsoft 365 Business Premium licenses.
How does Intune Remediations work?
Remediations use a pair of PowerShell scripts for all the heavy lifting. The first half is a detection script, as the name suggests, used to determine whether a condition exists on the target PC. The second is a remediation script, which includes the logic and actions to resolve the detected problem.
Remediations can be deployed with just a detection script, allowing for monitoring and reporting of a condition, or you can deploy detection and remediation scripts together to identify and resolve a problem.
How you choose to craft your detection and remediation scripts is largely up to you. Any condition or attribute can be used to determine whether an issue is present in a system. For example, we can use PowerShell to:
- Detect installed applications
- Review available disk space
- Search for files
- BitLocker status
- Entries in the Event Viewer
If you can work with it in PowerShell, odds are you can use PowerShell to detect it. It is also important to ensure your detection script returns the appropriate exit code.
- Exit 0: remediation is not required
- Exit 1: remediation is required
You can also use custom exit codes for other conditions and script error detection. Just remember that Intune will not trigger a remediation unless your detection script returns exit code 1.
Bonus Tip
Include logging and script outputs in your detection and remediation scripts. Not only will this simplify troubleshooting and help your fellow administrators, but Intune will also include the last console output in the Intune portal. By selecting the “Pre-remediation detection output” and “Post-remediation detection output” columns when monitoring your remediation, you will see the scripts output. I typically include a status or error message in my remediations to populate these fields.
What does a remediation look like?
A common request within this environment was addressing legacy applications installed across the organisation’s Windows PCs. We could have packaged each application and configured an “uninstall” assignment, however, we wanted to avoid sourcing application installation media.
Remediations are perfect for this use case. For this example, we will focus on Microsoft Silverlight.
Thankfully for us, Silverlight creates entries within the registry that we can use to as a detection. In my script, I have defined the locations PowerShell will search along with the filter used to identify Silverlight.
$RegUninstallPaths = @(
'HKLM:SOFTWAREMicrosoftWindowsCurrentVersionUninstall',
'HKLM:SOFTWAREWow6432NodeMicrosoftWindowsCurrentVersionUninstall'
)
$UninstallSearchFilter = {($_.GetValue('DisplayName') -like 'Microsoft Silverlight*')} Next, we need to create a loop to check each of our registry paths for Microsoft Silverlight and exit where we find a match.
foreach ($Path in $RegUninstallPaths){
Get-ChildItem -Path $Path | Where-Object $UninstallSearchFilter |
ForEach-Object {
Write-Output "Non-compliant: Silverlight found on device"
Stop-Transcript
Exit 1
}
}
Write-Output "Compliant: Silverlight not found on device"
Stop-Transcript
Exit 0 The detection script structure can be adapted for the remediation script. Below, I am looping through each registry path searching for Microsoft Silverlight. Once we have a match, we are kicking off an uninstall process with Msiexec.
foreach ($Path in $RegUninstallPaths) {
if (Test-Path $Path) {
Get-ChildItem $Path | Where-Object $UninstallSearchFilter |
foreach {
Write-Host "Found installation: $($_.PSChildName)"
$Arguments = '/X' + $($_.PSChildName) + ' /qn /l*v C:ProgramDataMicrosoftIntuneManagementExtensionLogsUninstall-3CX' + $($_.PSChildName) +'.log'
$Uninstall = Start-Process MSIexec.exe -ArgumentList $Arguments -Wait -NoNewWindow -PassThru
$ReturnCode = $Uninstall.ExitCode
Write-Host "Return Code: $ReturnCode"
}
}
} As always, use this code with mindfulness and ensure you have tested any code before deploying it into production.
Deployment of remediations is configured in Intune under “Devices” > “Scripts and remediations”. Provide a name and helpful description, then select the detection and remediation scripts. While configuring these settings, ensure “Run script in 64-bit PowerShell” is enabled to enforce the use of 64-bit PowerShell.
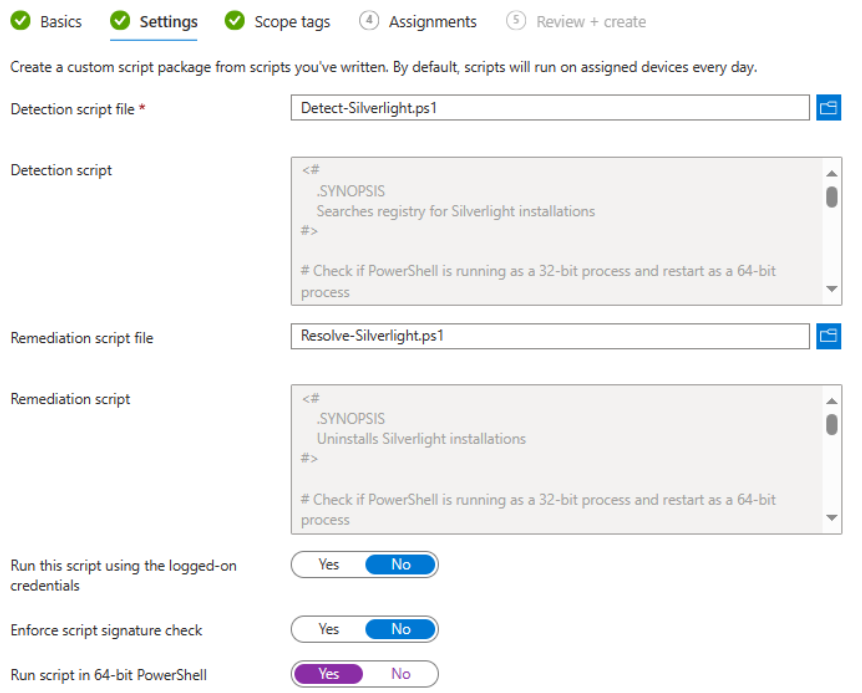
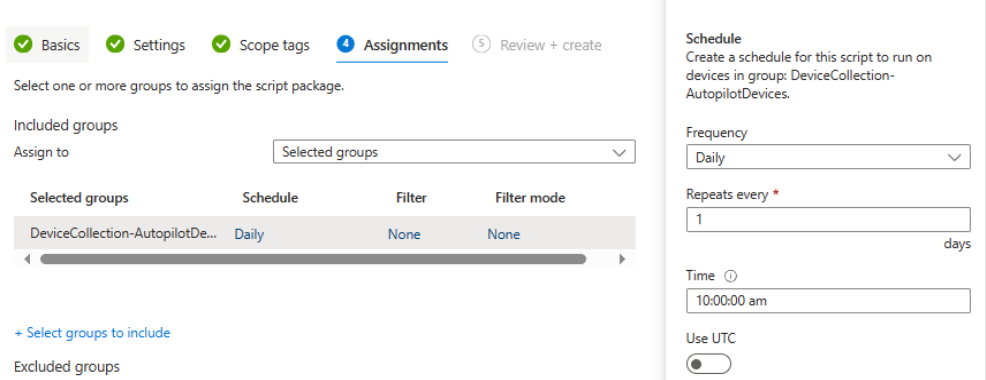
There are three options when configuring scheduling: once, hourly and daily. Select the option that is appropriate for your remediation and organisation. For Silverlight, I selected daily (repeats every one day) to ensure the application was removed as quickly as possible.
If a remediation needs to be executed immediately, we can now run remediations against specific devices on demand. Locate your Windows PC in the Intune console, click the three dots (…) in the top menu bar, and select “Run remediation (preview)”. Simply select the remediation and click “Run remediation”.
We have covered a fairly straightforward example of how a remediation can be used to automate administrative tasks in Intune. This concept can be expanded, where anything that you can detect or analyse with PowerShell can be crafted into a remediation. You may already have a library of PowerShell scripts that resolve common problems and could be adapted and deployed via remediations.
If you want to know any further information about adopting Microsoft Intune and how Insentra can help, our Managed Intune services may be exactly what you are looking for! You may also download our eBook “Taming the Device Zoo: The Ultimate Guide to Microsoft Intune” or contact us.











