This blog takes you on a short (relatively speaking) journey to achieve the unthinkable —nailing a flawless 100% in Essential 8 Compliance.
We achieve this feat with the help of one tool, Red Hat Insights.
What is Red Hat Insights?
Red Hat Insights is a predictive analytics and management tool designed to proactively identify and address potential issues in IT environments. It’s part of the broader suite of Red Hat management tools, focusing on maintaining system health, performance and security.
Key Features of Red Hat Insights
Here are some key features and benefits of Red Hat Insights.
- Proactive Identification of Issues – Insights utilises advanced analytics to predict and identify potential issues before they become critical
- Actionable Insights – Provides specific recommendations and actions to resolve identified issues
- Vulnerability Detection – Identifies security vulnerabilities and provides steps to mitigate them
- Compliance Management – Ensures systems comply with industry standards and internal policies
- Performance Optimisation – Monitors and optimises resource usage to improve system performance and efficiency
- Configuration Analysis – Checks system configurations against best practices to enhance performance
ACSC Essential Eight Recommendations
The ACSC Essential Eight is a set of baseline mitigation strategies recommended by the Australian Cyber Security Centre to help organisations improve their cybersecurity posture. It is particularly relevant for managing Linux servers in environments where security and compliance are critical.
Look, I am not going to lie to you. This is what the ASCS suggests for Linux:
Given the difficulty in implementing application control in Linux environments, the following mitigation strategies can be implemented to assist with reducing the residual risk of the exploitation of Linux workstations and servers.
Note: This list is not exhaustive and does not take into account specific use cases or differences between Linux distributions.
- Use unique restricted users for key at-risk services (e.g. Apache software runs under a restricted “apache” user role)
- Disable unrequired operating system functionality, including disabling unrequired network services
- Apply additional forms of security policy enforcement such as SELinux or AppArmor
- Implement appropriately hardened security configurations and permissions of key configuration files (e.g. /etc/security/access.conf, /etc/hosts, /etc/nsswitch.conf)
- Use the “noexec” parameter to mount partitions which users have write access to
- Perform an inventory of binaries, determine which ones users need to run. For all others, either uninstall them or remove the setuid permission
- Implement software-based firewalls for both internal and external network interfaces, for IPv4 and IPv6 (or disable IPv6 support)
- Perform tasks with least privileges
- Implement specific configurations based on server roles (e.g. if running Apache HTTP Server, harden as per Apache hardening guidance)
- As far as practical, implement vendor security guidance for specific Linux distributions
In short, what this means is a good CIS hardening will be more than enough to meet the requirements.
Comprehensive Recommendations for CIS Hardening
If you’re interested in a more comprehensive guide, here are the actual recommendations:
- Application Whitelisting: Implemented through tools like SELinux or fapolicyd (They actually talk about AppArmor which is primarily used on Debian-based distros, but fapolicyd has been around for at least 5 years… Well SELinux will do)
- Patching: Regularly updating Linux packages using tools like yum, dnf
- Cryptography: Ensure system-wide crypto policies are configured as expected, disabling legacy encryption algorithms and ensuring that dependent services (like SSH) are using recommended algorithms
- Software Integrity Checking: Implemented using the RPM package management system, which can check the hashes of installed software packages, including many that are important to system security
- User Application Hardening: Configuring software policies and firewall settings to secure user applications
- Restricting Administrative Privileges: Using sudo (or other solutions) to control access to administrative commands and reducing root access
- System Accounting with auditd: Crucial for security and compliance, as it provides detailed records of user actions, system events and configuration changes
- System Logging: Essential for monitoring system health, diagnosing issues and ensuring security. Logs can include information on user actions, system errors, access attempts and more
- Daily Backups: Automate regular backups
- Authentication: This is crucial to securing systems and ensuring only authorised users can access sensitive information and resources
And here you have it. If you still want to know more, you may check out Australian Cyber Security Centre’s documentation on Hardening Linux Workstations and Servers.
But if you really want your system to be hardened, I suggest checking Centre for Internet Security’s recommendations.
Insights Configuration for ASCS Essential Eight Compliance Check
The following section describes the steps required to enable Compliance Checks for RHEL8 servers:
Prerequisites
Before you proceed with the configuration, make sure you have the following requirements first:
- Red Hat Enterprise Linux 8+
- Red Hat Insights Client installed on the device and registered to Red Hat Insights (Internet connection required)
- Red Hat subscription to access cloud.redhat.com
- Red Hat account
Insights Client Installation
Make sure you have the repositories enabled and access to the internet as the insights client will require communication with the Red Hat cloud portals.
- Install Insights Client and other OpenScap compliance packages
# dnf install -y insights-client
scap-security-guide
openscap-scanner
openscap - After installing the Client, register your system with the Red Hat Cloud Insights using the following command. This will connect your RHEL 8 system to Red Hat Insights, and it will start uploading data for analysis
# insights-client --register - Enable the Insights client to auto-upload data daily
systemctl enable insights-client.timer
systemctl start insights-client.timer - By default, the insights-client’s timer is set to 1h. If you want to change the timer, use the following command:
# systemctl edit insights-client.timer
[Timer]
OnCalendar=hourly
RandomizedDelaySec=14400 - If you don’t want to wait for the daily automatic upload, you can manually upload data using this command:
# insights-client --upload - To ensure that your system is registered and is sending data, run the following command:
# insights-client --status - If everything is set up correctly, you should see a message similar to the one below:
# insights-client --status
System is registered locally via .registered file. Registered at 2023-02-09T16:09:54.762936
Insights API confirms registration. - Log into the Red Hat Cloud Insights web console to view your system’s data. Your system should appear in the inventory.
- Navigate to https://console.redhat.com/insights/dashboard and enter your credentials
- In the left pane, click Inventory → Systems
- Confirm the registered server is on the list of servers
- On cloud.redhat.com, navigate to Security→ Compliance→ SCAP Policies
- Click on Create new policy
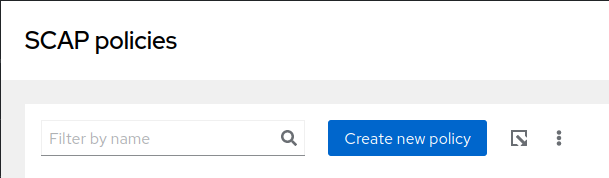
- Select the RHEL Version and select the Policy type. In our case, we are selecting Essential Eight Policy. After selecting, click Next
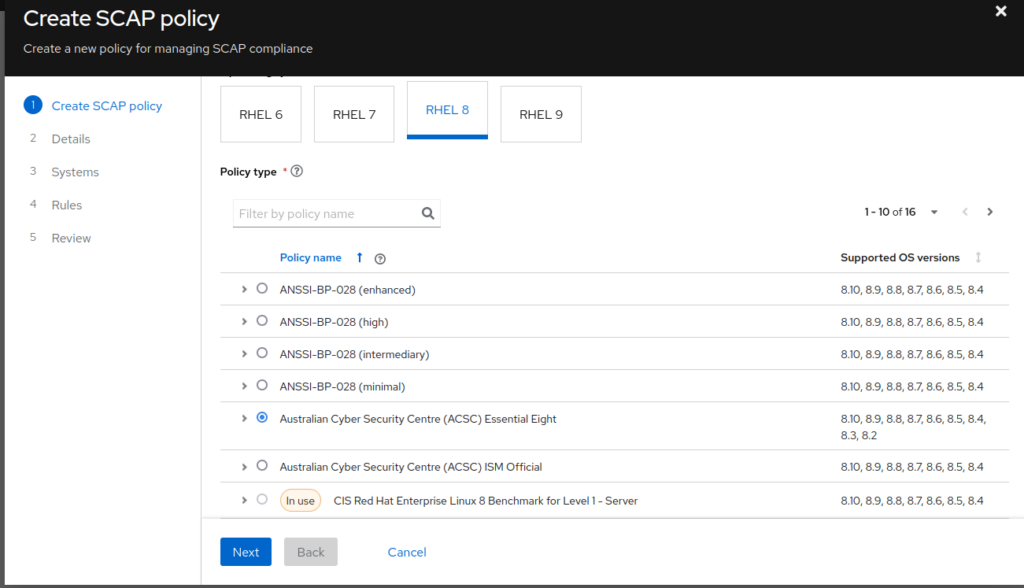
- Specify a unique name, describing the policy type and the RHEL version, specify the Compliance Threshold and click Next:
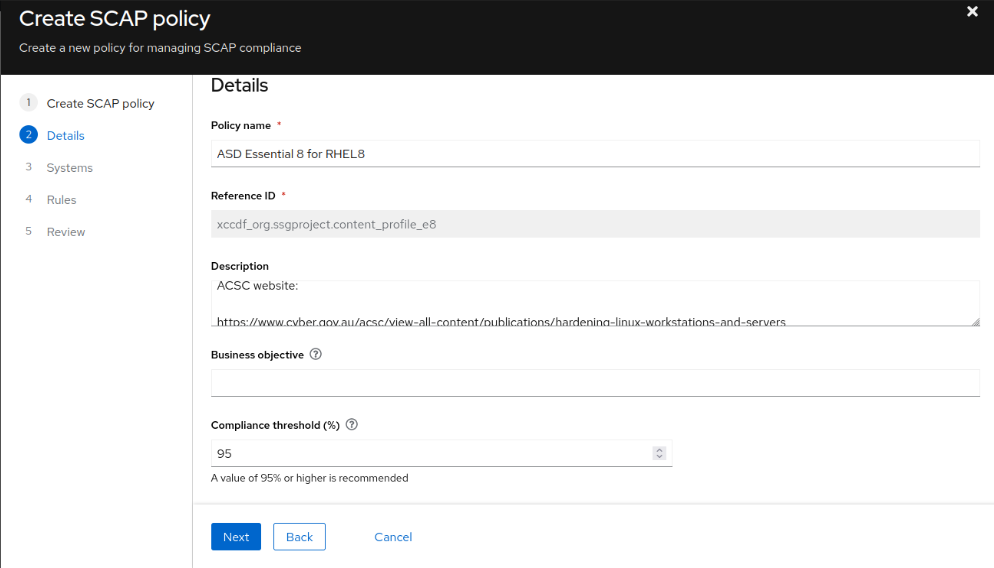
- Select the system(s) to run the compliance checks against and click Next
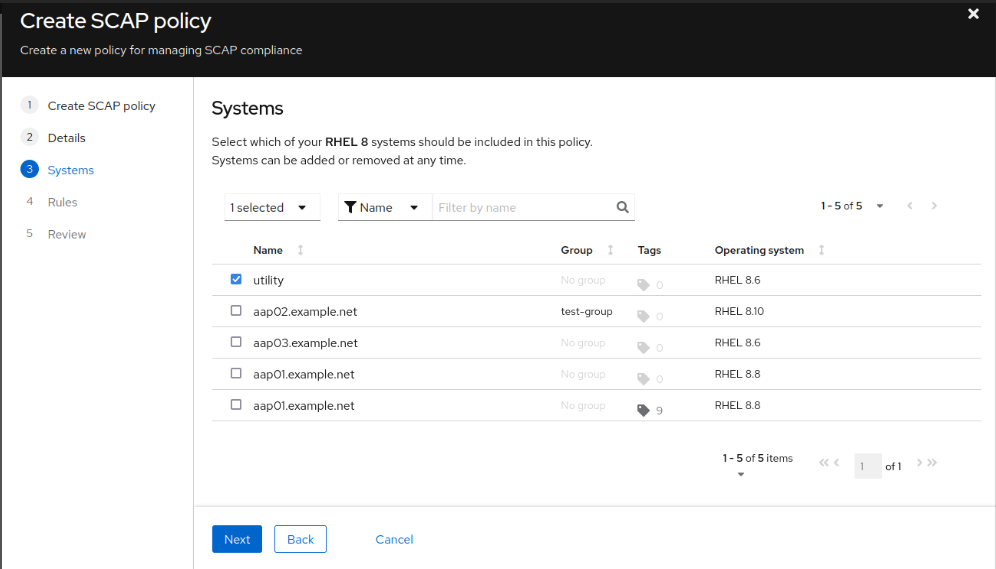
- Customise rules and click Next. Then, Click Finish after reviewing the configuration
- Connect to the host where the compliance will be checked and run the following command:
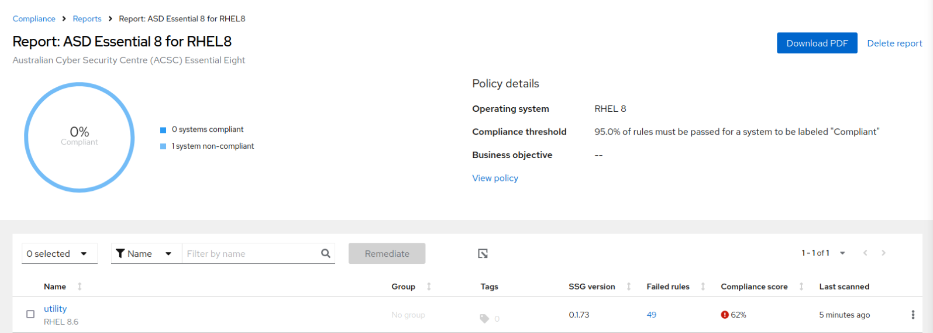
# insights-client --compliance - Navigate to Security→ Compliance→ Reports and verify the Reports
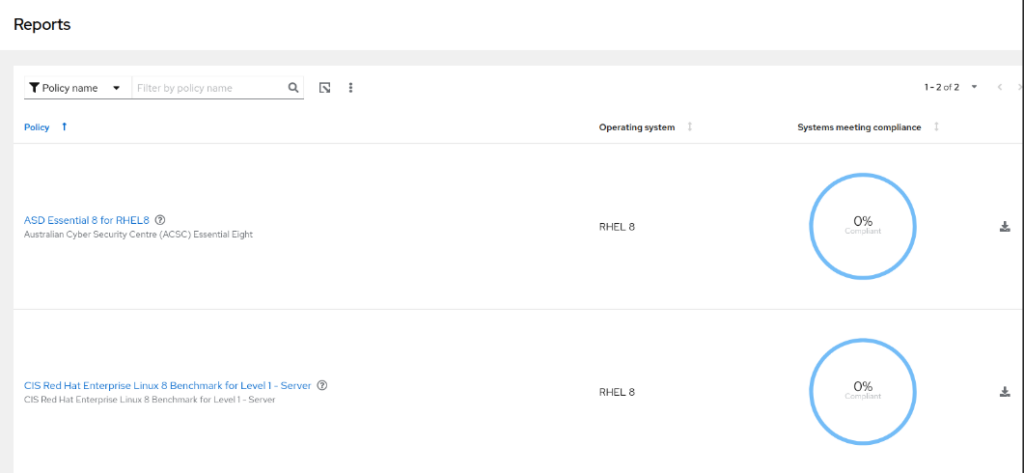
- Click on the ASD Essential 8 for RHEL8 policy link
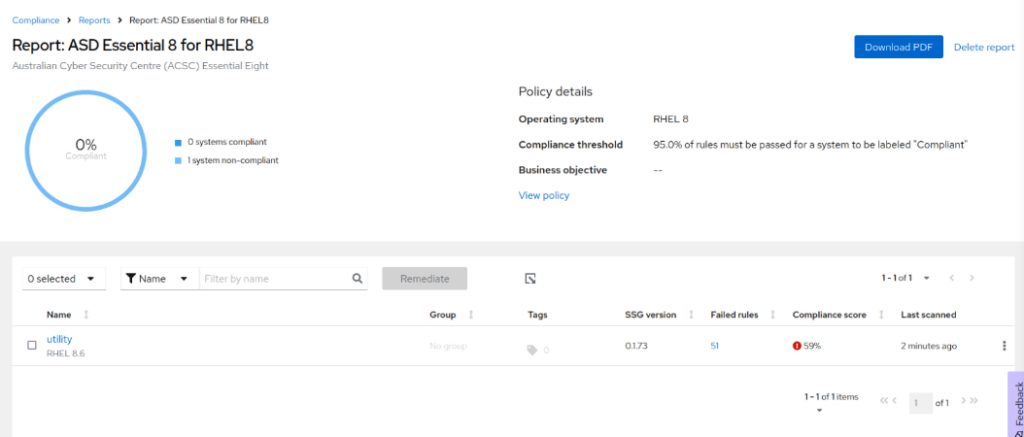
- Review failed tests by clicking on the server name
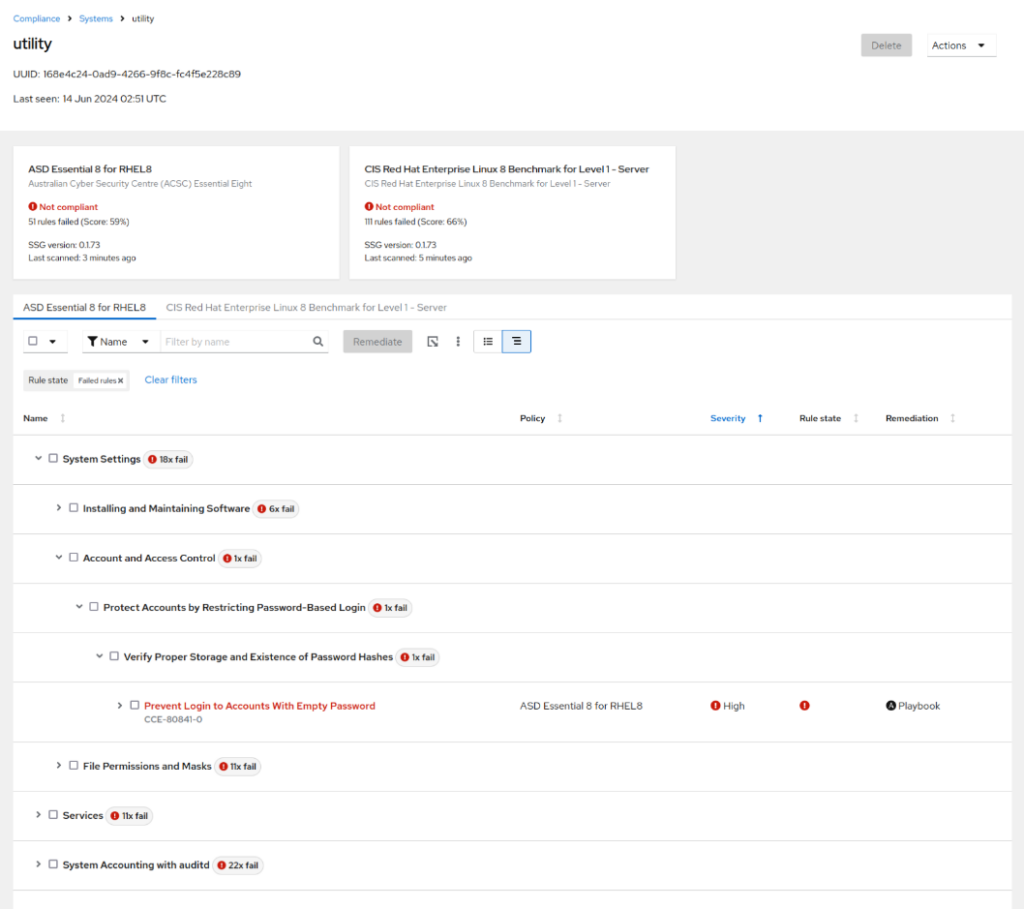
Addressing Compliance Violations
Addressing Compliance Violations is easy. Simply follow the instructions below.
- Select the violation(s):
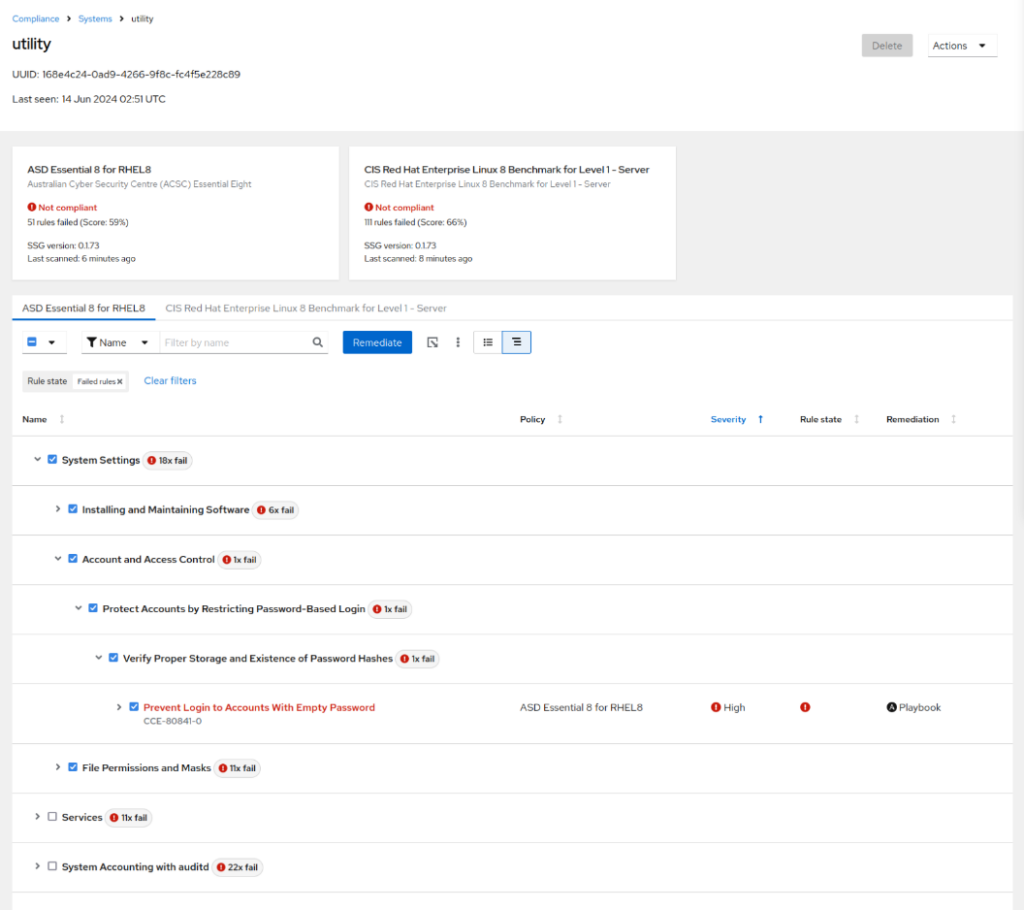
- Click Remediate, then Create New Playbook, then Next
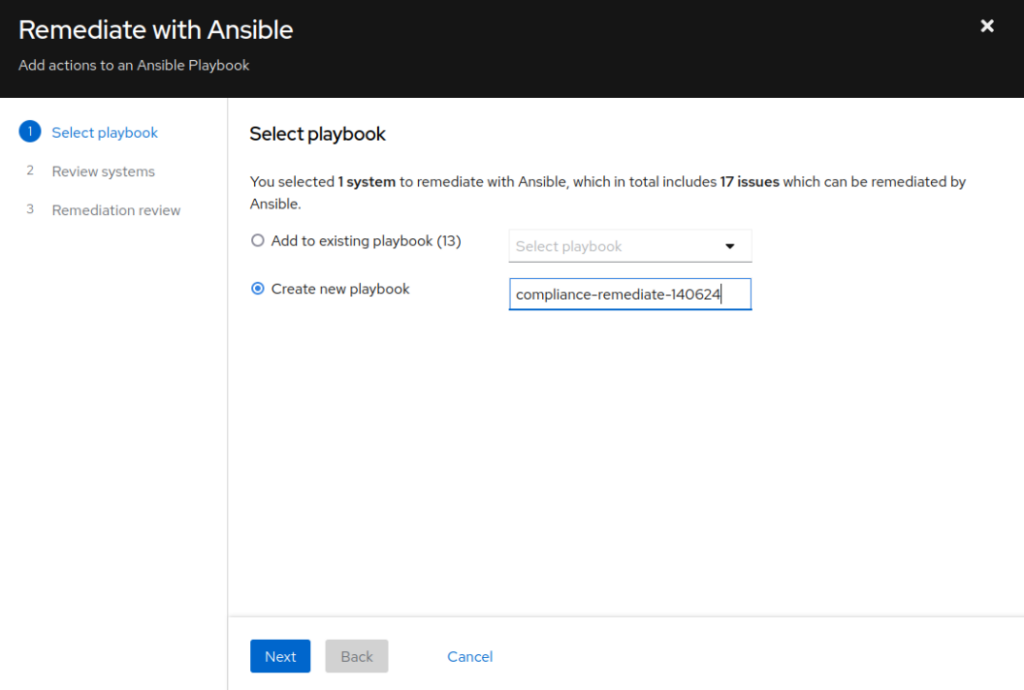
- Verify the systems being remediated and click Next
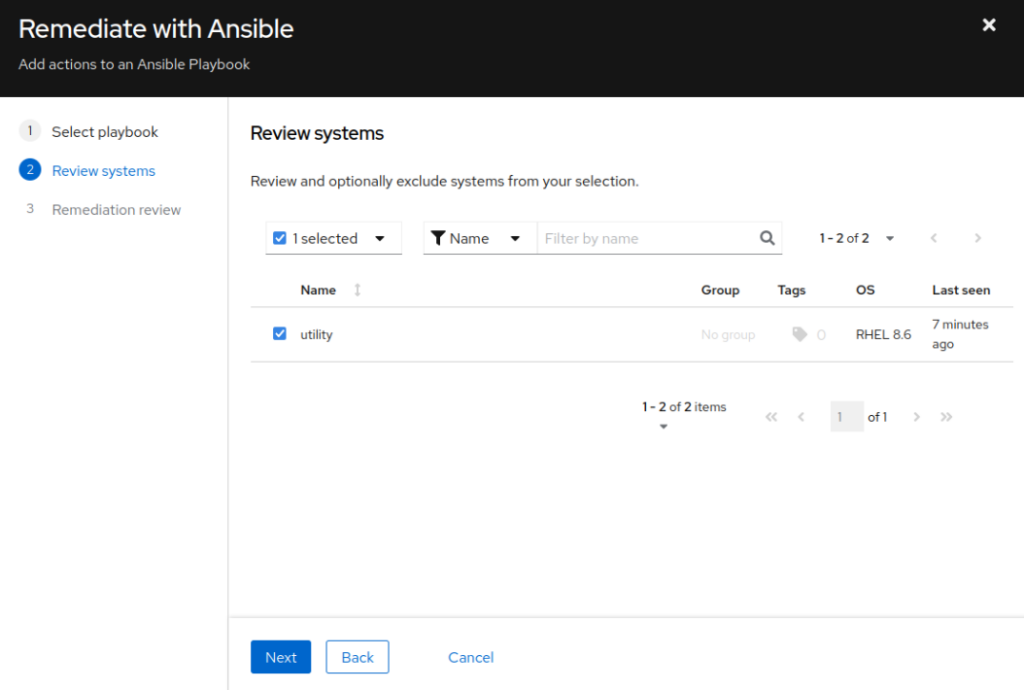
- Verify the Remediation Review and Turn off autoreboot, if necessary. Click Submit
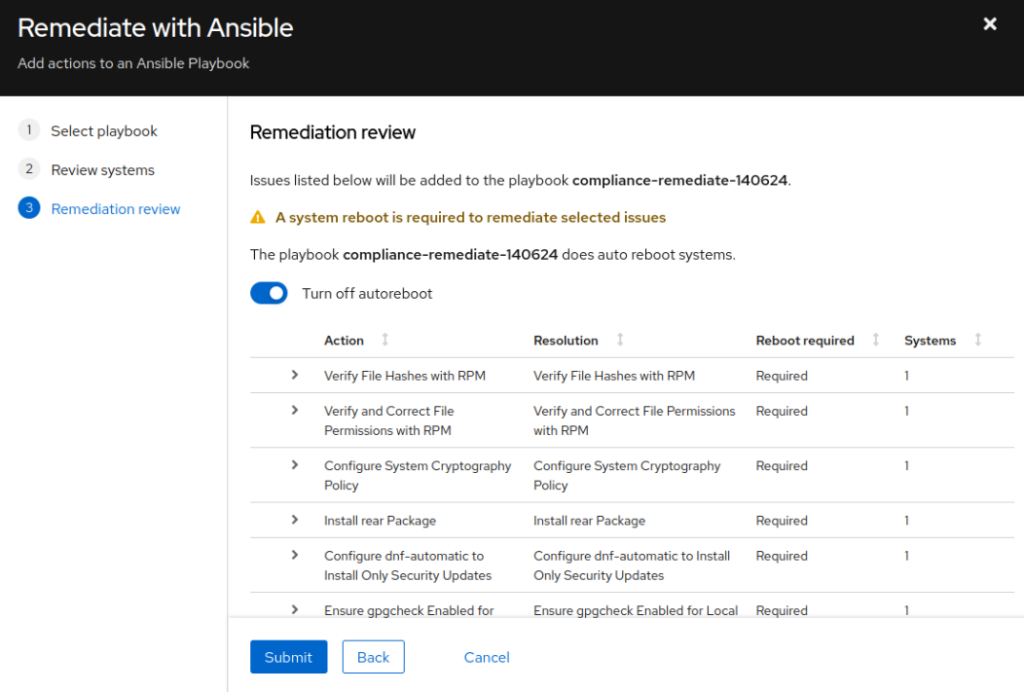
- If you do not have Ansible Automation Platform (AAP), click Open playbook compliance-remediate-140624 to download the Ansible playbook with the remediation tasks

- If you have the AAP and it is already configured to authenticate with Insights (if not – check my blog “Patching RHEL Vulnerabilities with Insights” on how to do it), navigate to Projects, find the project that synchronises the content from Insight and click Synchronise
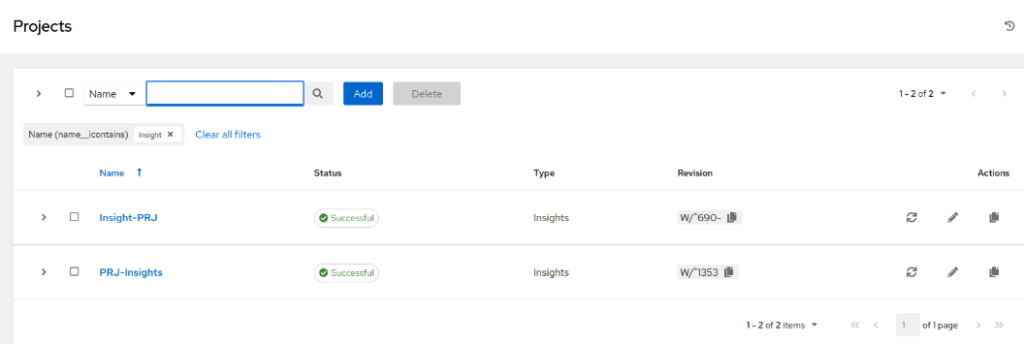
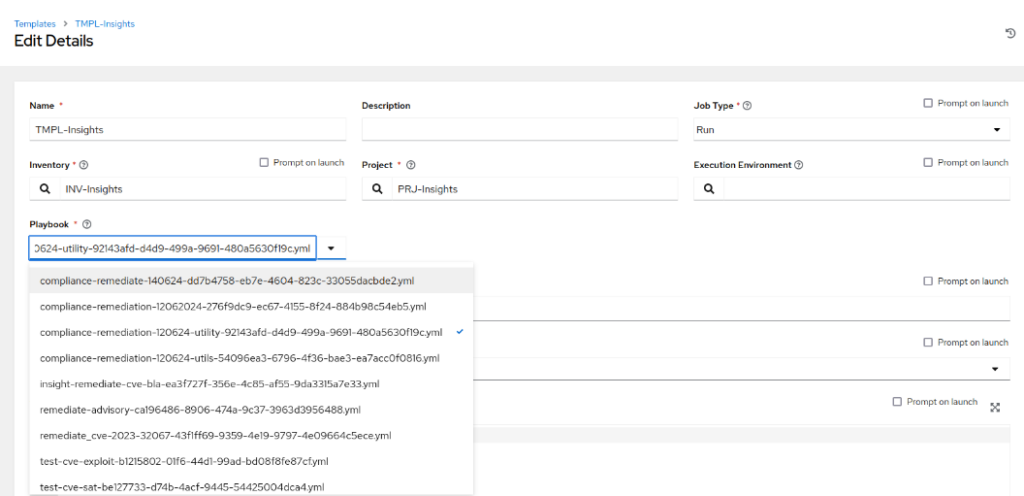
- Wait until the Project Job finishes successfully and navigate to the Templates. Find the Template you use with the Insights project, edit it and select the playbook we created in Insights section of cloud.redhat.com:
- Note that the Playbook has the name we entered in the previous steps: “compliance-remediate-140624”
- Save and Launch the Template:
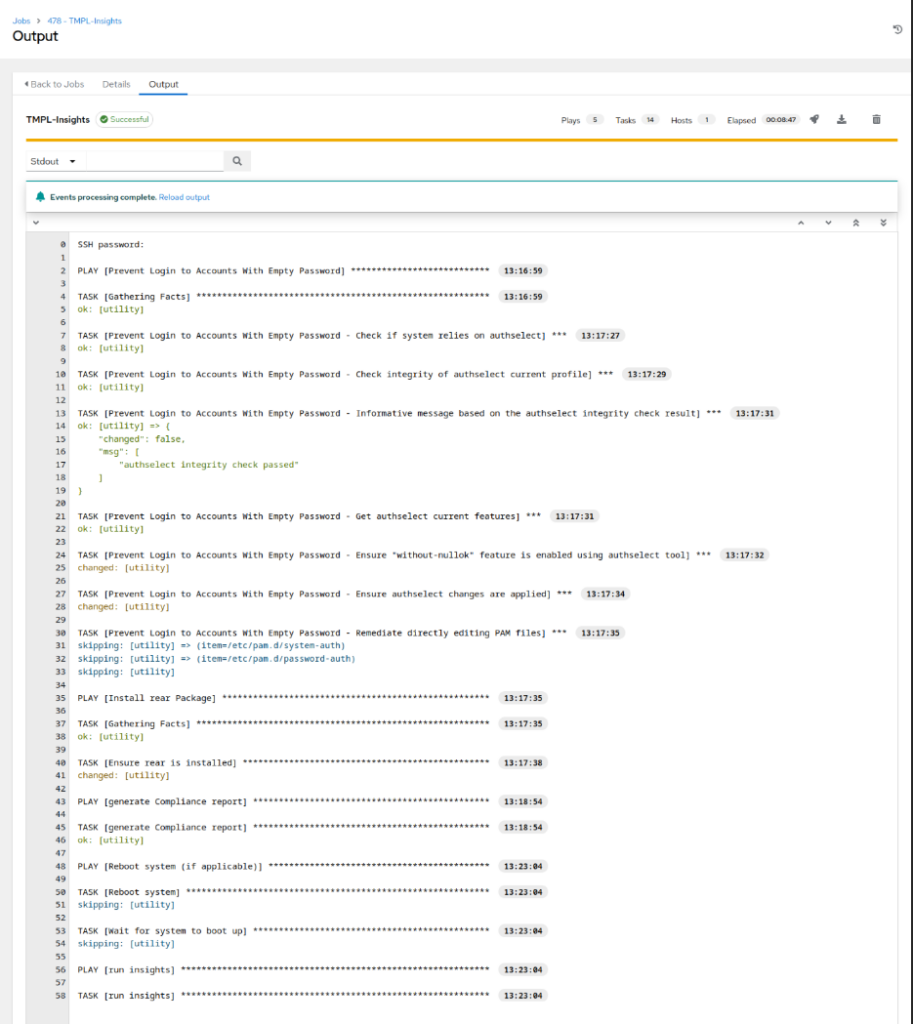
- Keep in mind that the Job might take a while, especially at the end when the insights-agent runs the compliance verification and uploads the report to cloud.redhat.com
- Verify the Compliance score after the remediations in Compliance→ Report on cloud.redhat.com/insights/compliance/reports. Note that the score improved from 59% to 62% (as I did not run all the remediations)
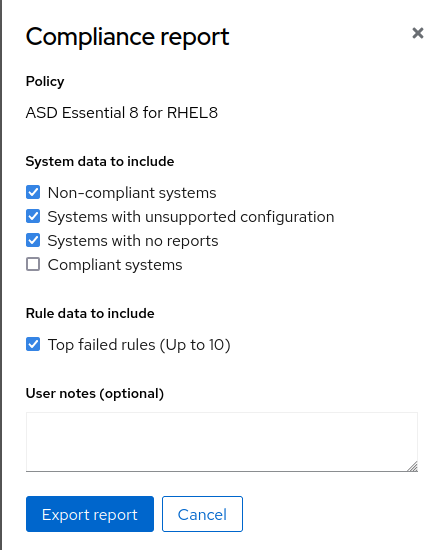
- Export the Report
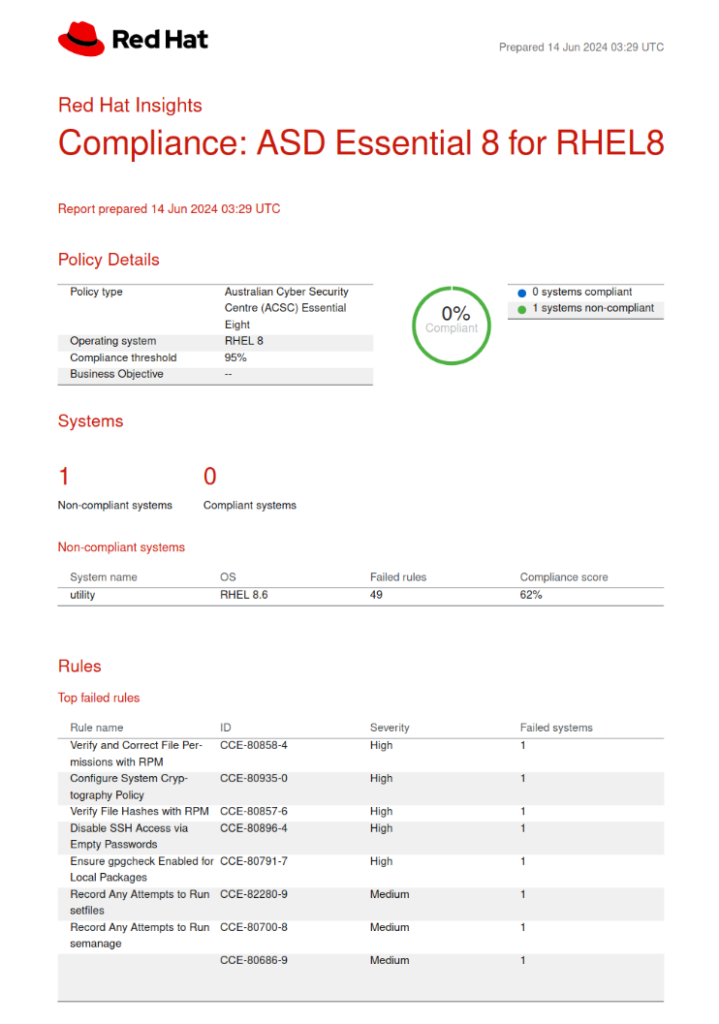
Sample Red Hat Insights Compliance Report
There you have it. I hope this guide helps you achieve the elusive 100% in Essential 8 Compliance. If you’d like to learn more about RHEL servers, check out my other blogs or reach out to Insentra for a consultation.











