I have been working on several M365 related security projects recently. These primarily consisted of increasing the organisations security posture and working towards a Zero Trust architecture. For everything you need to know about Zero Trust please take a look at the Ultimate Guide to Zero Trust
Requirement
The customer (let’s call them Contoso) has utilised external collaboration quite extensively. Contoso were happy to add external users to Contoso’s internal Teams, however, they did not want external users to have the option to download any files so they can be used outside of Contoso’s environment. Contoso are still on their Information Protection journey so any kind of fancy labelling etc. was unfortunately not an option. With this in mind, we had to completely block access for external users. To achieve this requirement, the solution was to create a Conditional Access policy. As always, there are a few prerequisites that are needed before Contoso can achieve the desired solution
- Azure AD Premium P1
- Microsoft Defender for Cloud Apps
Solution
To implement this solution you need to have one of the below Azure AD admin roles assigned to your account
- Conditional Access Administrator (least privilege)
- Security Administrator
- Global Administrator
All the configuration takes place within Microsoft Entra admin centre > Protect & secure > Conditional Access. To create this policy, please follow the below steps
- Create a new policy
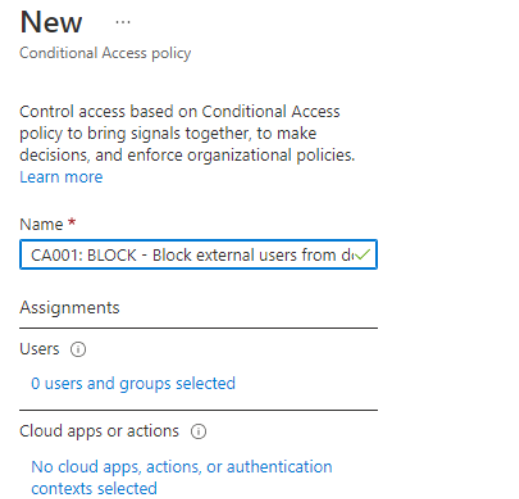
Give the CA policy an appropriate name, preferably in alignment with Microsoft CA naming conventions, for example, “CA001: BLOCK – Block external users from downloading files in Office 365”
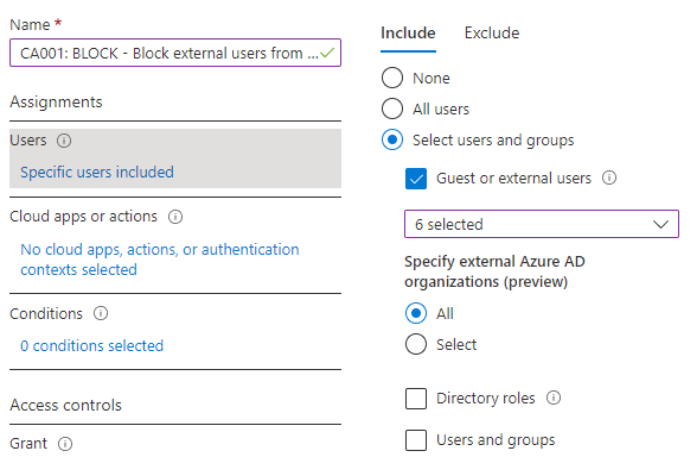
- Within Users > Assignments select “Guests or external users” and all for “Specify external Azure AD organisations (preview)”
- Within Cloud apps or actions > Select apps and choose “Office 365”. This will apply to all M365 services, if you require something more granular, for example, Exchange Online, then just select Exchange Online
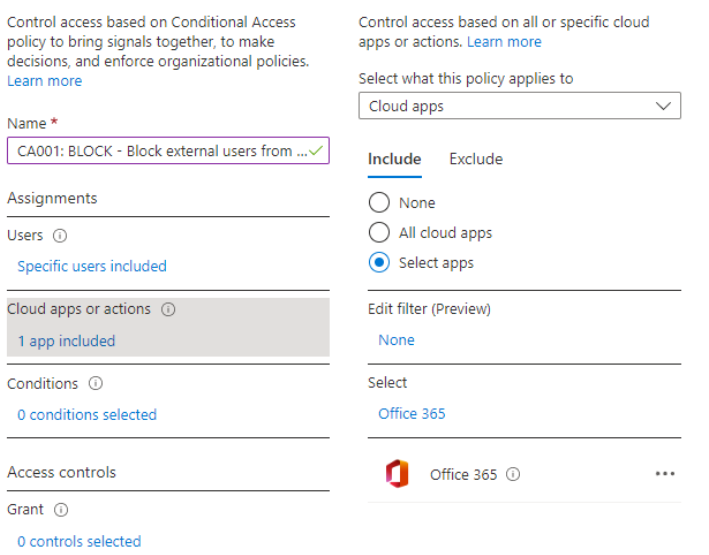
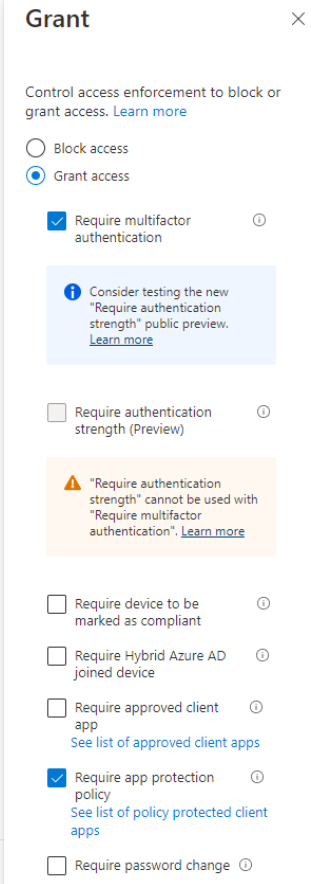
- Within Access controls > Grant select the following options. This will ensure external users must use MFA and can only access M365 services using an approved client app
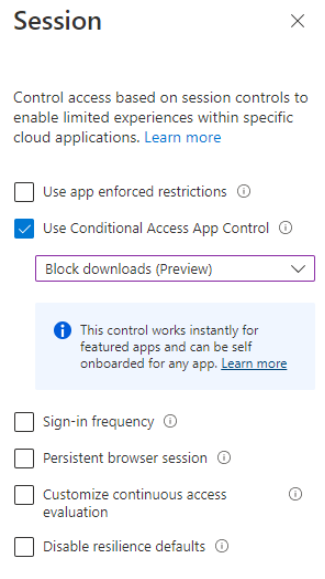
- Lastly, within Access controls > Session select the follow options. This will ensure the external users cannot download a local copy from any Contoso Teams they have been added to
That is you good to go! I would recommend enabling this policy as “Report-only” for a few days and keep an eye on the logs to ensure the CA policy is behaving as you expect it. Once you have confirmed The CA policy is meeting your expectations, you can enable the policy to “On” and you can now relax that external users cannot download any M365 files.
CONCLUSION
In conclusion, implementing a Conditional Access policy can help organisations like Contoso block external users from downloading files in Office 365, while ensuring their information is protected. Following the steps outlined in this article and enabling the policy as “Report-only” before going live can ensure the policy is working as expected. With this policy in place, organisations can confidently collaborate with external users while maintaining control over their data. Hopefully this has been informative and helpful! If you need any further clarification, or a no thrills chat, contact us at Insentra or read more of my Insentra Insights.
RELATED ARTICLES
How to allow only work account access to apps using Intune
Securing and Optimising Access to Azure Storage Accounts with Azure Endpoints