Unless you have been living under a rock, you will know Red Hat Satellite 6.3 is now available.
The Back Play – Red Hat Satellite 6.x was initially shipped including puppet to provide the goods required for management and automation. Subsequently, Red Hat decided to invest heavily in Ansible and as a result, acquired the company behind Ansible Tower. Many have asked – “how come you have puppet on board in Satellite 6.x but not your own product?” Response – Red Hat took action by adding additional provisioning snippets in Red Hat Satellite 6.3 which allow full integration with Ansible Tower.
So how does it work?
Ansible Tower has a concept of “Templates”. In other words, Templates are responsible for bringing together multiple aspects of the configuration, namely: Project, Inventory and Authentication and some others. Ansible then executes the underlying ansible playbook which is a collection of templates aimed at provisioning the outcome you are looking to achieve. Furthermore, Ansible Tower provides a neat feature called ‘Provisioning Callback’.
So what is provisioning Callback?
Provisioning callbacks are a feature of Tower that allow a host to initiate a playbook run against itself, rather than waiting for a user to launch a job to manage the host from the Tower Console. Callback provides the ability to automatically configure a system after it has been provisioned by another system (such as AWS auto-scaling, OS provisioning system like kickstart or pre-seed) or for launching a job programmatically without invoking the Tower API directly. The Job Template launched only runs against the host requesting the provisioning.
In previous releases of Satellite 6.x you could ‘integrate’ Satellite with Ansible Tower to allow Ansible Tower to build the dynamic inventory. In other words – Ansible Tower was talking directly to Satellite and could query the database for the list of hosts configured on Satellite. This approach allowed Ansible Tower to have a list of hosts and after that the host using some other mechanism (usually a one-time service using curl to execute a specific URL) would execute the Template using Provisioning Callback. Although this approach worked quite well, it required additional manual steps and overhead.
So what did Red Hat do?
They listened to the community and in Satellite 6.3 they introduced aforementioned snippets. The beauty of this approach is that the provisioning of the machine using either kickstart or VM provisioning does not require any elaborate changes.
So lets do it.First of all, we need to have: Satellite 6.3 and Ansible Tower installed. Once we have them up and ready we need to allow the Ansible Tower to query the Satellite.
First, we need to create a Role in Satellite.
1. Navigate to Administer → Roles
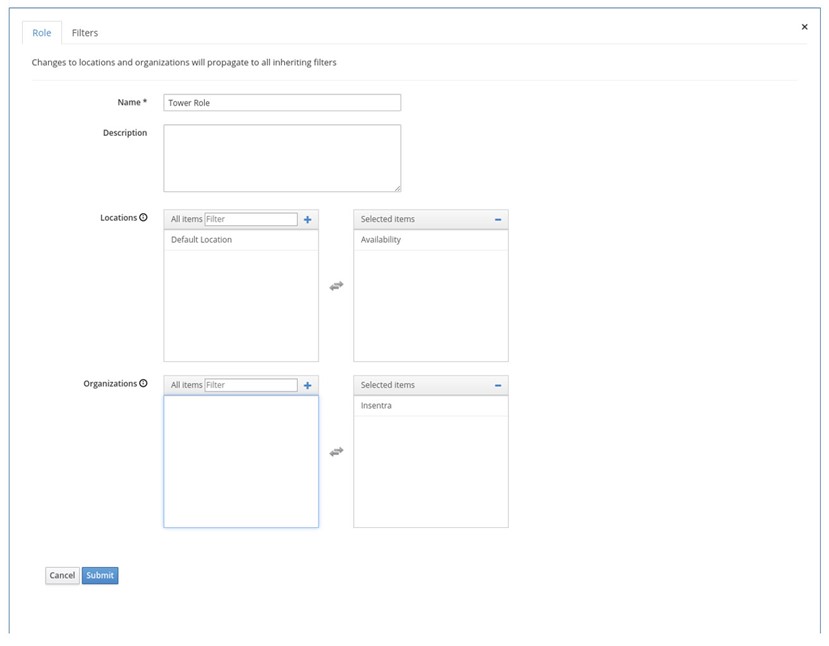
2. Create a Role with a meaningful name. For example ‘Tower Role’.
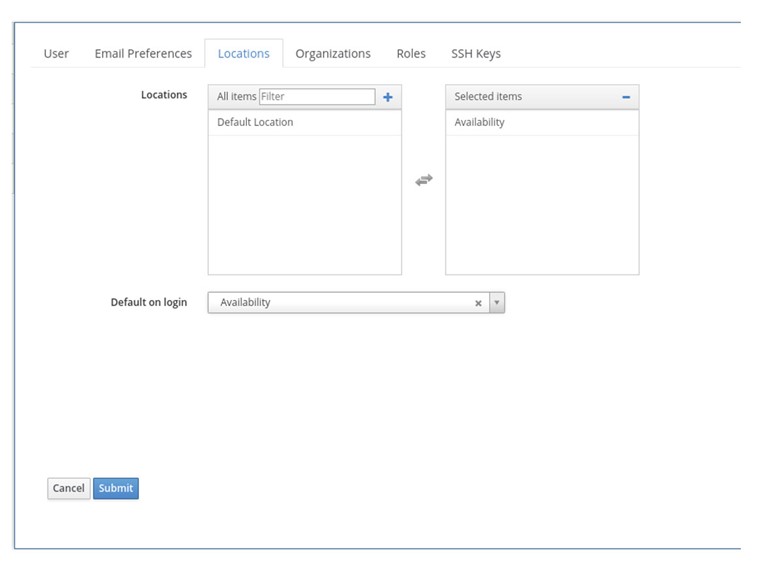
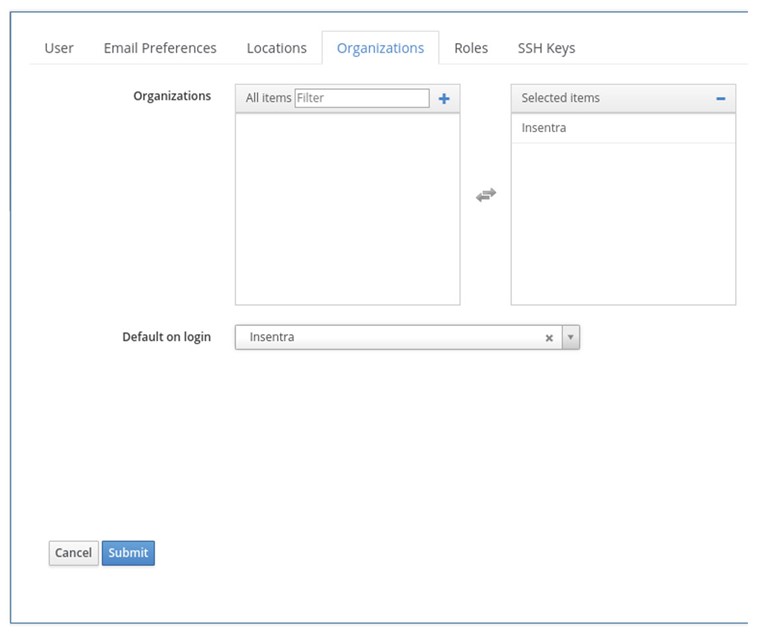
3. Click on a new Role and select Locations and Organisations:
4. Click on Filters and create a new filter
5. Select Fact Value Resource Type and view_facts as Permissions. Leave Unlimited selected and click Submit
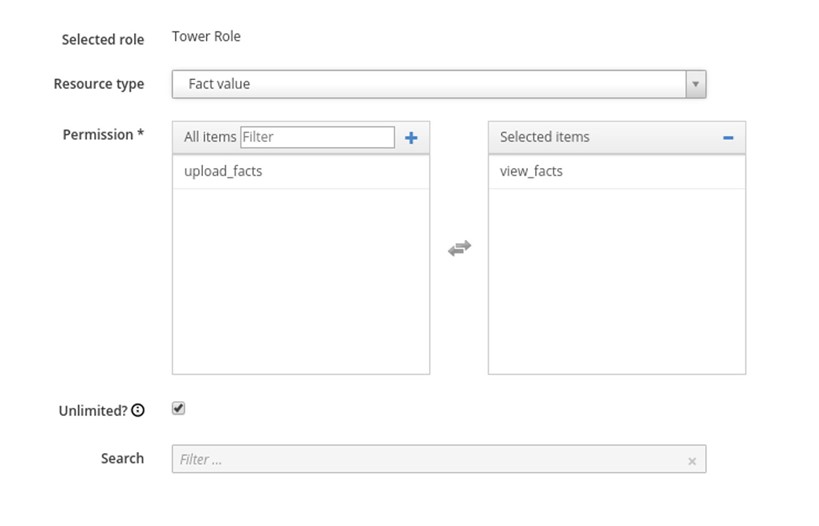
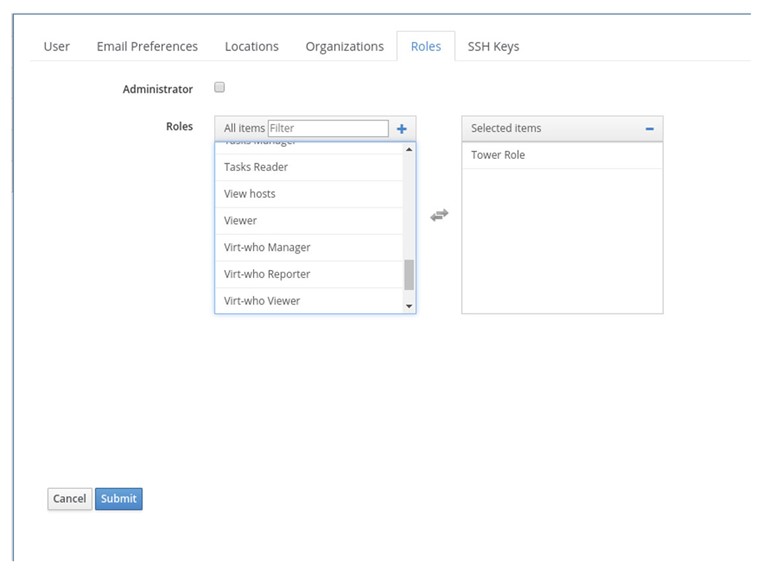
6. Create another filter and select Host as a Resource Type and view_hosts for the Permissions:

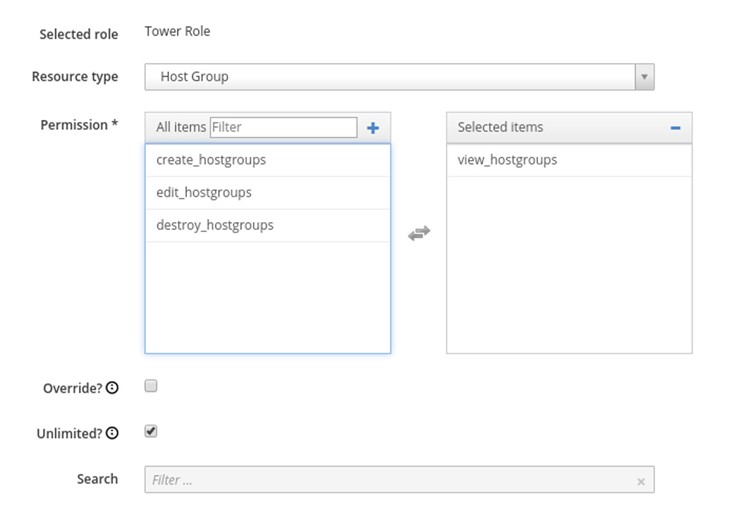
7. Create another filter and select Host Group as the Resource Type and view_hostgroups for permissions.
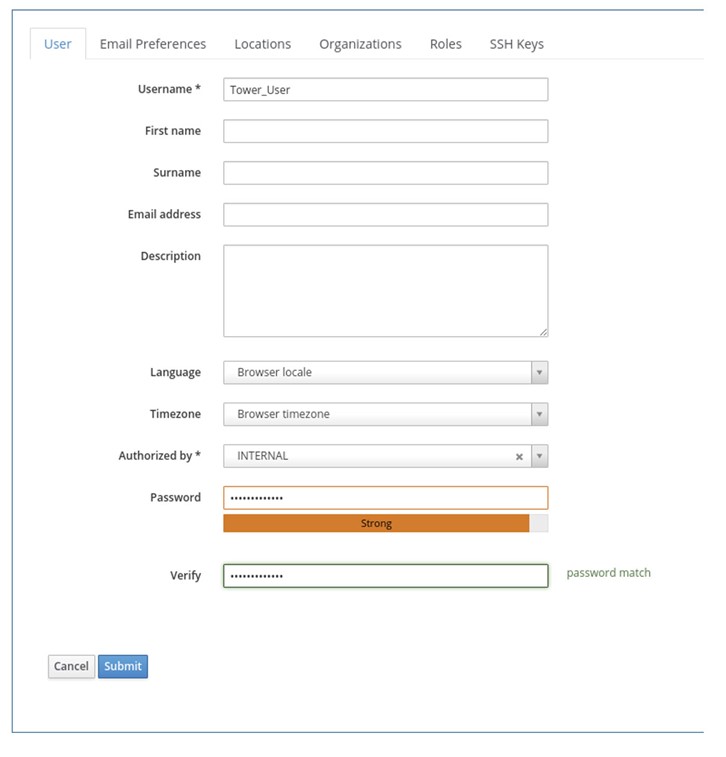
8. Create a Satellite User with Tower Role as a Role
Next steps will be executed on the Ansible Tower.
- Log into the Ansible Tower with Administrative privileges
- In the right top corner, click on a cog
- Click Credentials
- Click Add
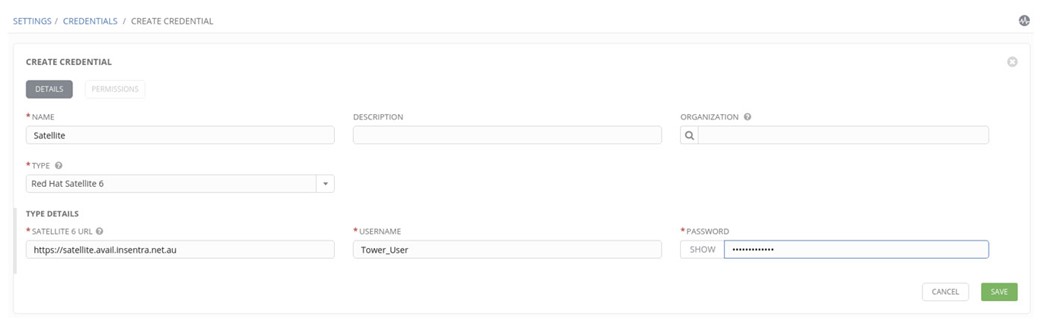
- Specify the Name, Type, URL and username/password as created in Satellite 6
6. Create the Inventory which will point to Satellite 6:
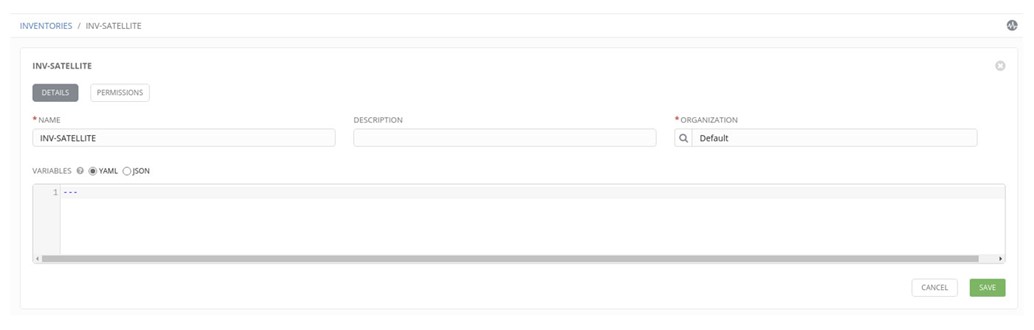
7. Click on a newly created inventory and click Add Group (Note: the latest version of the Ansible Tower has slightly different UI but the concept is the same).
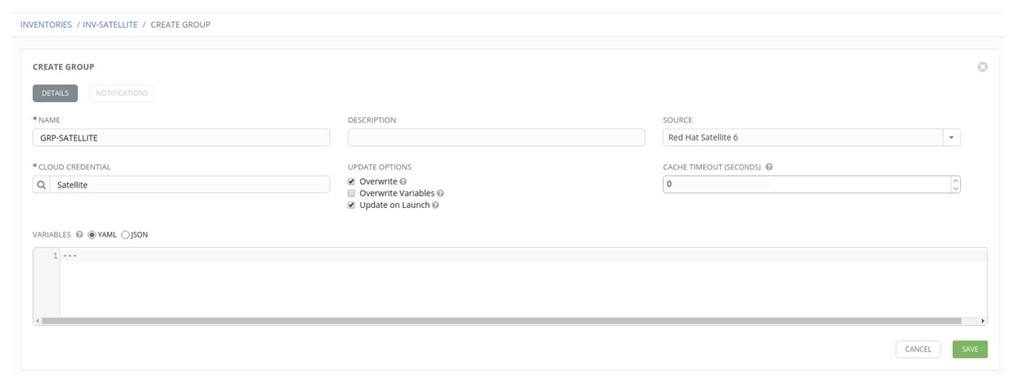
8. Verify if the Dynamic Inventory is working as expected. Click on INV-SATELLITE and next to GRP-SATELLITE, click on the refresh symbol (two arrows in a circle). If everything is working as expected, you can find the JOB under the JOBS:
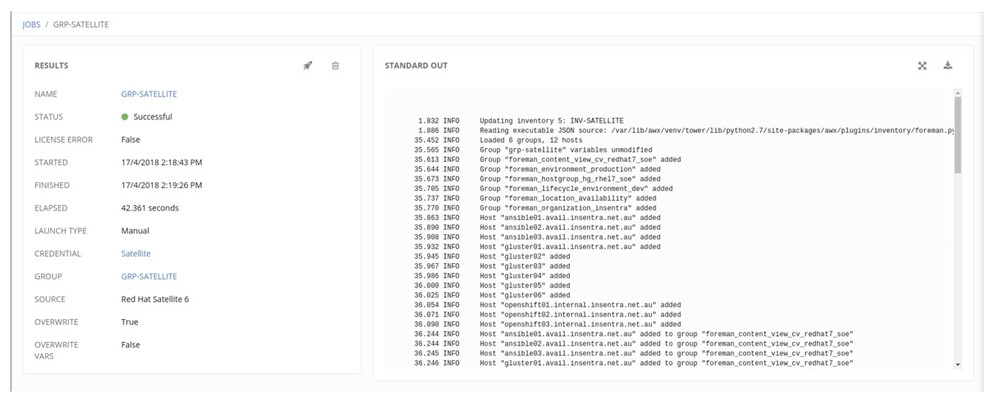
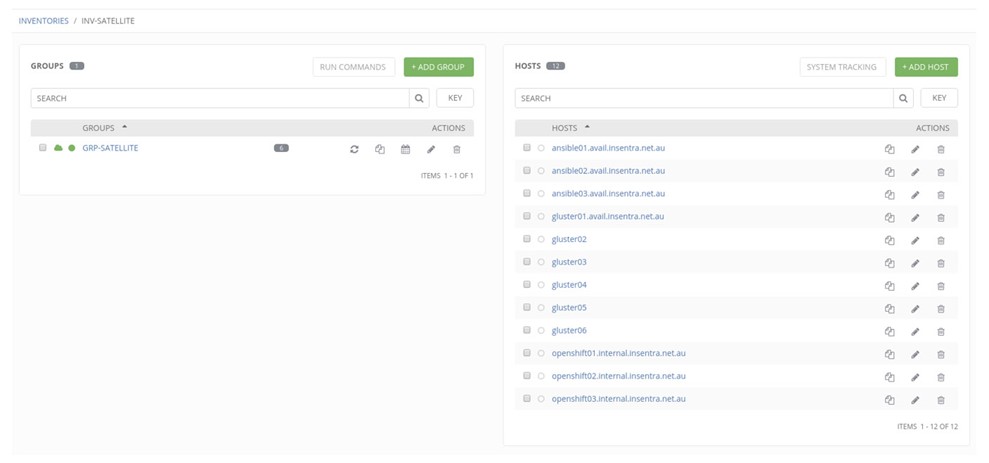
Now. Let’s create a simple Template with a Provisioning Callback. Note that the UI in the latest version of Ansible Tower is slightly different.
1. Create a Template and select Inventory which was created earlier and the Machine Credentials. Select ‘Allow Provisioning Callbacks’ and generate a ‘Host Config Key’. Click Save
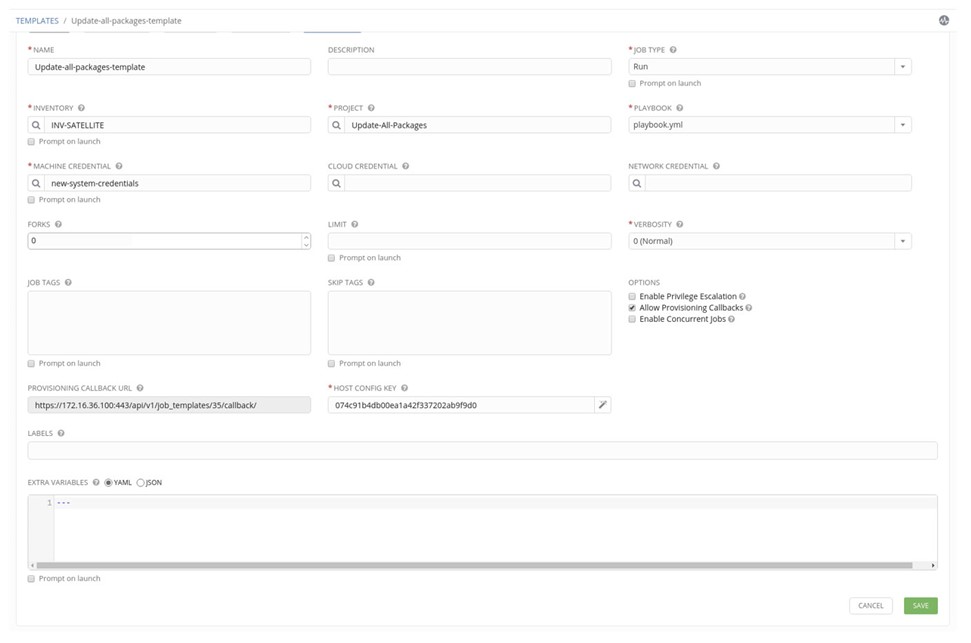
The next step will be done on the Satellite.
1. In the Host groups select the Host Group you want to use for the provisioning and navigate to Parameters.
2. Add following parameters:
| Name | Value | Description |
| ansible_tower_provisioning | true | Enable tower provisioning |
| ansible_tower_fqdn | tower.example.net | URL of the Ansible Tower |
| ansible_job_template_id | 35 | The Job Template ID. It can be found in the Provisioning Callback URL: https://172.16.36.100:443/api/v1/job_templates/35/callback/ |
| ansible_host_config_key | 074c91b4db00ea1a42f337202ab9f9d0 | Host Config Key. Can be found in the Template configuration. |
3. Provision a host using modified Host Group
So what was the outcome?
During provisioning, the ansible provisioning_callback snippet is executed if the Parameter ‘ansible_tower_provisioning’ is set to ‘true’. This snippet will create a service on the machine being provisioned which in turn will execute the curl command using other elements configured in the Parameters of the Host Group. If all the steps are successful
• First – the dynamic inventory of the Satellite will be executed in Ansible Tower
• Second – The execution of the Ansible Tower Template which will be only used against the machine which executed the provisioning callback
All the Ansible Tower executions can be verified in Jobs.










