Having the ability to Active Directory Domain Join (ADDS) an Azure Storage account has changed the game for many organisations deploying file service into Azure. I wrote previously about the options for storing container workloads such as FSLogix Containers in Azure, one of them being native Domain Joined Storage accounts.
There are a few steps in Domain Joining and configuring the Storage Accounts, which can be a little confusing the first time you run through the process. Microsoft provides some OK documentation and some baseline PowerShell modules which drives the process (AzureFilesHybrid) and Mr Brinkhoff has a good guide to help you out from a base walkthrough. If you get any of the process wrong, or it fails at all, it can be a little finicky to fix (depends how far you get).
I have put together a script to help automate the entire process, specifically aimed at configuring Storage Accounts for FSLogix Container workloads to support your EUC environment. The script automates the following components for you:
- Downloads and installs the AZFilesHbrid PowerShell Module if it does not already exist
- Domain Joins an existing Azure Storage Account
- Configures the required IAM roles for specified users (such as WVD or Citrix users) to access the share, as well as configuring specified Admin roles to allow for NTFS permission management (Elevated Contributor)
- Configures the required NTFS permissions on the root share to allow for FSLogix Container creation (via the new-smbconnectioncommand and the storage account key from the specified storage account)
The script contains a couple of basic parameters allowing you to break out the tasks as required, or simply alter an existing configuration.
- JoinStorageAccountToDomainsimply grabs the defined Storage Account and Active Directory Domain Joins into the specified OU. I default to using a ServiceLogon account rather than a computer account
- ConfigureIAMRolessets the Storage File Data SMB Share Contributor role for the specified user groups (think of this as the share permission on-premises) and the Storage File Data SMB Share Elevated Contributor role for the specified administrators (this is required for admins to alter NTFS permissions if not using the storage account keys to map the drive and set them)
- ConfigureNTFSPermissionssets a base level of NTFS permissions for FSLogix Container access via the new-smbmapping command leveraging the Azure storage account access key (I look for the default “Key1”) and utilizing icacls
- DebugStorageAccountDomainJoindebugs any Domain Join issues (this is just calling the AZFilesHybrid Debug commands)
You will need to alter some basic variables for your environment in the script, it is very self-explanatory, but a brief outline as follows:
- SubscriptionIdYour Azure subscription ID
- ResourceGroupNameThe Resource Group your storage account resides in
- StorageAccountNameThe name of your storage account
- ShareNameThe Share name defined in your storage account (Eg, Containers)
- DomainAccountTypeEither a ServiceLogon or ComputerAccount. I default to ServiceLogon
- OUThe OU for the storage account ServiceLogon or ComputerAccount to be created. I default to using the OrganizationalUnitDistinguishedName switch, so you need to specify your OU by its Distinguished Name
- FSContributorGroupsGroups to assign the Storage File Data SMB Share Contributor roles (Such as Citrix or WVD user groups)
- FSAdminUsersAdmin users to assign the additional Storage File Data SMB Share Elevated Contributor Roles (admins who can change NTFS permissions on the root share). I was too lazy to split out the roles, so the admins also get Storage File Data SMB Share Contributor and Storage File Data SMB Share Reader
- DownloadUrlThe current download URL for the current AZFilesHybrid Module
- ModulePathPath to download and load the AZFilesHybrid Module
- DriveLetterDrive letter to use in the new-smbmapping session to set the default NTFS permissions for containers. I default to X the drive is cleared post setting permissions
- JSON allows for the input to be JSON based rather than defining variables in the script
- JSONInputPathspecifies the JSON input file
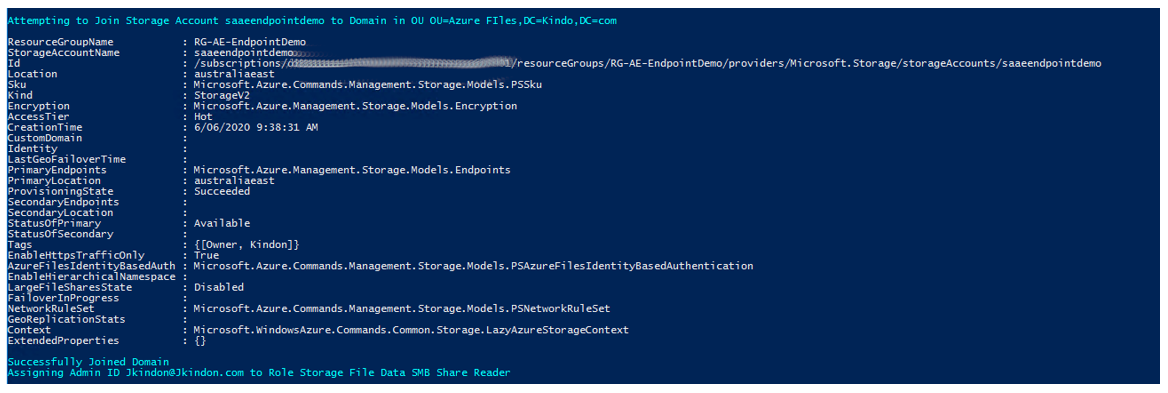
At the end of a run using the JoinStorageAccountToDomain, ConfigIAMRoles and ConfigNTFSPermissions parameters, you should have a Domain Joined Storage Account
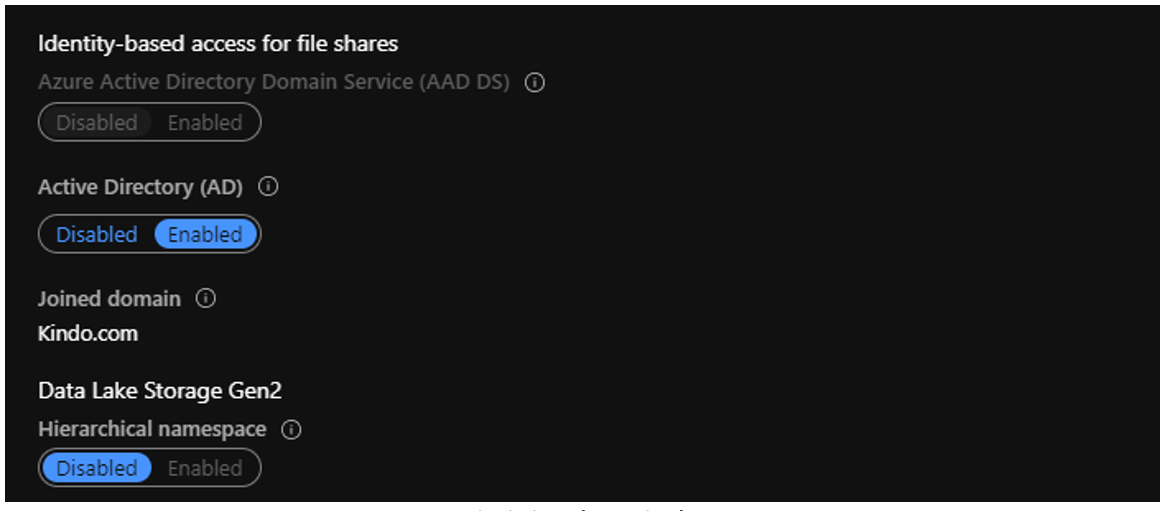
Domain joined to Kindo.com
With IAM roles configured on the file share

IAM Roles in place
And appropriate NTFS permissions for your Containers
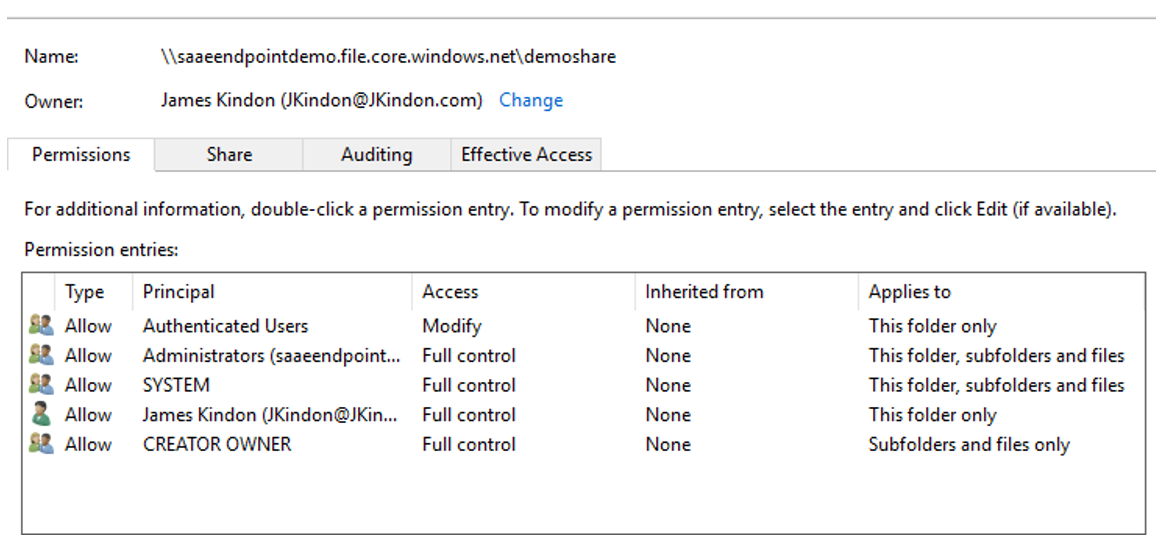
NTFS permissions on the root
I hope this helps those of you that are looking to consume Azure Domain Joined Storage Accounts for Container workloads. The script is located on my GitHub repo here – any suggestions or additions are welcome. There are a few more things I would like to add to it such as cleaning failed joins, but I wanted to limit the number of modules and dependencies required for now.
This blog was originally published on JKindon.com on 06/08/20 and shared with permission.











