What a tongue-twister that title is. So now we’ve gotten that out of the way, let’s move on to the more exciting stuff: How to use Kerberos SSO for SSH authentication in iDM Domain with AD Trust (a follow-on from How to configure Ansible Automation SAML SSO with Red Hat SSO).
Diving straight in, an SSH connexion to remote servers without a password is a useful function for interactive users and is often necessary for automated activities.
In this article I am going to run through enabling GSSAPI authentication (Generic Security Services Application Programming Interface), which is one of several options available. The concept is you authenticate on the client, which is usually your computer, and then SSH (or SFTP, SCP, SMB mount or any GSSAPI-enabled service) sends your credentials to the remote system where they are validated and then used to log you in. Depending on the software, there are two aspects which must be enabled in any client program: 1) command line options and configuration file settings, and 2) preference menu settings.
The following procedures describe the configuration required to enable GSSAPI authentication:
Kerberos Authentication from Linux Command Line
- Modify the SSH configuration in /etc/ssh/ssh_config to enable GSSAPI:
GSSAPIAuthentication yes GSSAPIDelegateCredentials yes - Login to the machine with a given user to obtain the Kerberos ticket.
- Verify the Kerberos ticket:
[testuser@archivemigrations.org@ssodb04 ~]$ klist Ticket cache: KCM:794602128:21655 Default principal: testuser@ARCHIVEMIGRATIONS.ORG Valid starting Expires Service principal 05/04/22 10:08:44 05/04/22 20:08:34 krbtgt/EXAMPLE.NET@ARCHIVEMIGRATIONS.ORG renew until 06/04/22 10:08:34 05/04/22 10:08:34 05/04/22 20:08:34 krbtgt/ARCHIVEMIGRATIONS.ORG@ARCHIVEMIGRATIONS.ORG renew until 06/04/22 10:08:34 05/04/22 10:08:44 05/04/22 20:08:34 host/ssodb03.example.net@EXAMPLE.NET renew until 06/04/22 10:08:34 - Login to another host using SSH –K:
[testuser@archivemigrations.org@ssodb04 ~]$ ssh -K ssodb03 Last login: Mon Apr 4 20:08:44 2022 from 172.16.156.160 [testuser@archivemigrations.org@ssodb03 ~]$ Using Putty for Kerberos Authentication
- Login to a Windows machine using your credentials.
- Open Putty and navigate to Connexion → SSH → Auth → GSSAPI and configure GSSAPI (as indicated below):
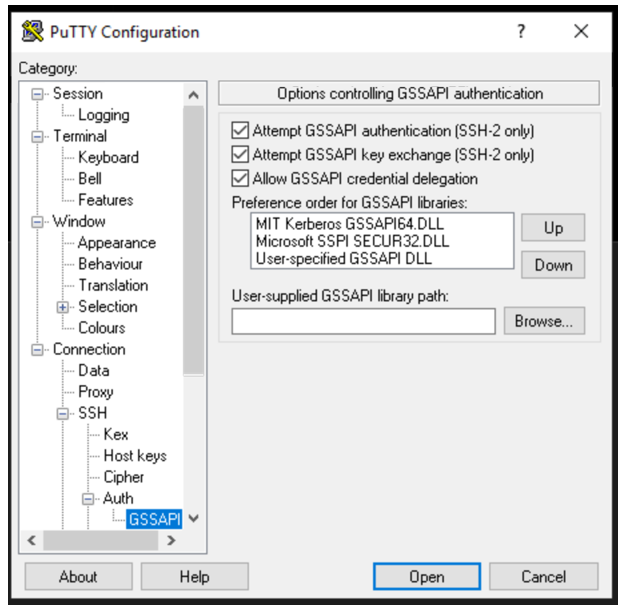
- Navigate to Connexion → Data and select ‘ Use system username’:
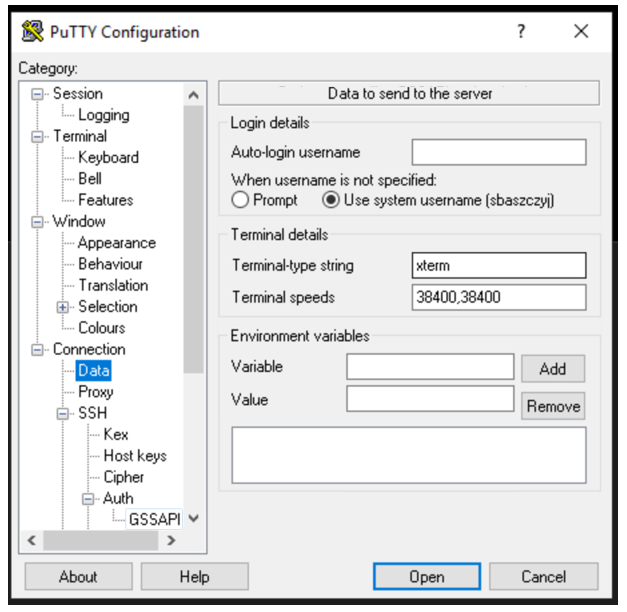
- Navigate to Session and specify the server to connect to. Save the session:
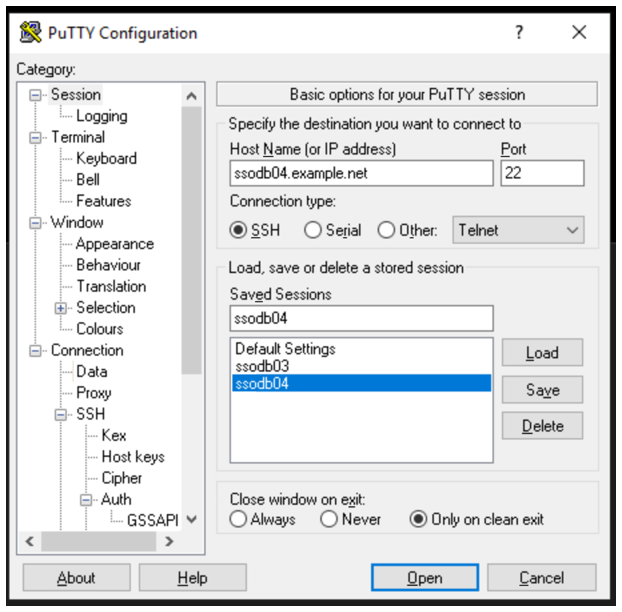
- Click Open and enjoy the SSO.
Using MobaXterm for Kerberos Authentication
- Ensure you are using the latest version of MobaXterm.
- Open MobaXterm and navigate to Settings → Configuration.
- Select SSH tab and configure the settings as indicated below. Ensure you enter the Domain you are going to use:
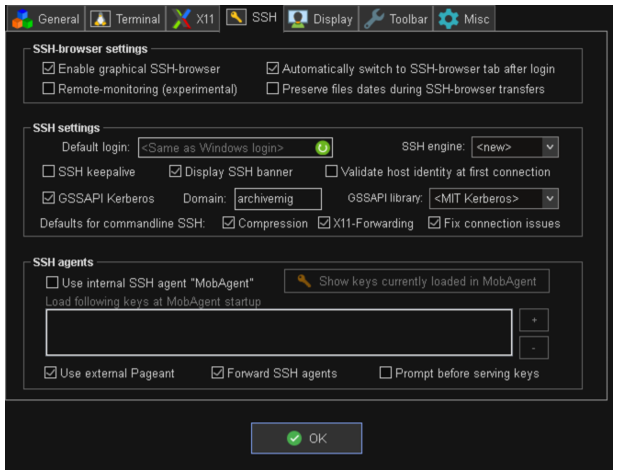
- Click OK.
- Create a new connexion and configure it as indicated below. Ensure the ‘Specify username’ is set to default. This indicates the system username (the username you used to login to the workstation) is going to be used:
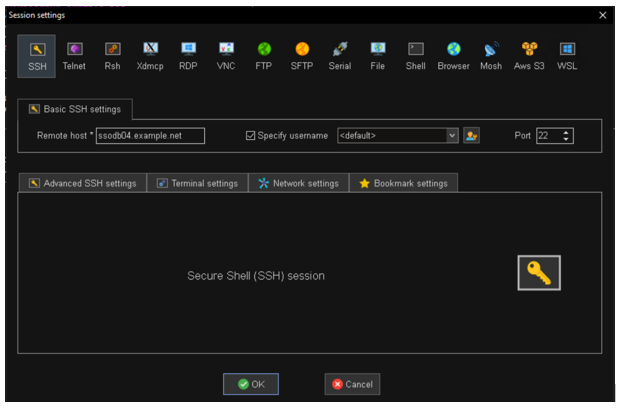
- Click OK and connect.
Well this brings us to the end of my brief guide on configuring Kerberos SSO for SSH authentication in Red Hat’s Identity Management with AD Trust. In my next article I’ll be discussing Kerberos authentication for multihomed servers (so stay tuned!).
As always, if you have any feedback or questions, we’d love to hear from you, or if you’re interested in learning more about Red Hat Identity Management we’d be more than happy to have a chat with you.











