The Complete Guide to Microsoft Defender for Endpoint
In today’s digital landscape, where cyber threats are constantly evolving and becoming increasingly sophisticated, the need for robust cybersecurity solutions has never been more critical. Organisations and individuals alike face the daunting task of safeguarding their sensitive data, digital assets and operations from the relentless onslaught of cybercrime.
To combat these challenges, Microsoft offers a comprehensive suite of security tools and features called Microsoft 365 Defender. At the heart of this suite lies a powerful weapon in the fight against cyber threats – Microsoft Defender for Endpoint.
Microsoft Defender for Endpoint is an enterprise endpoint security platform that goes beyond traditional antivirus protection. It is a cutting-edge, cloud-powered solution designed to proactively prevent, detect, investigate and respond to advanced threats across multiple platforms. By leveraging the latest in behavioural sensors, cloud security analytics, and threat intelligence, Defender for Endpoint empowers organisations to stay ahead of the curve and maintain a strong security posture.
In this comprehensive guide, we will take you on a journey through the world of Microsoft Defender for Endpoint. We will explore its inner workings, unveil its remarkable features, and showcase real-world examples of its efficacy in thwarting cyber threats. Additionally, we will delve into the migration process, helping organisations smoothly transition to this state-of-the-art security solution.
WHAT IS MICROSOFT 365 DEFENDER?
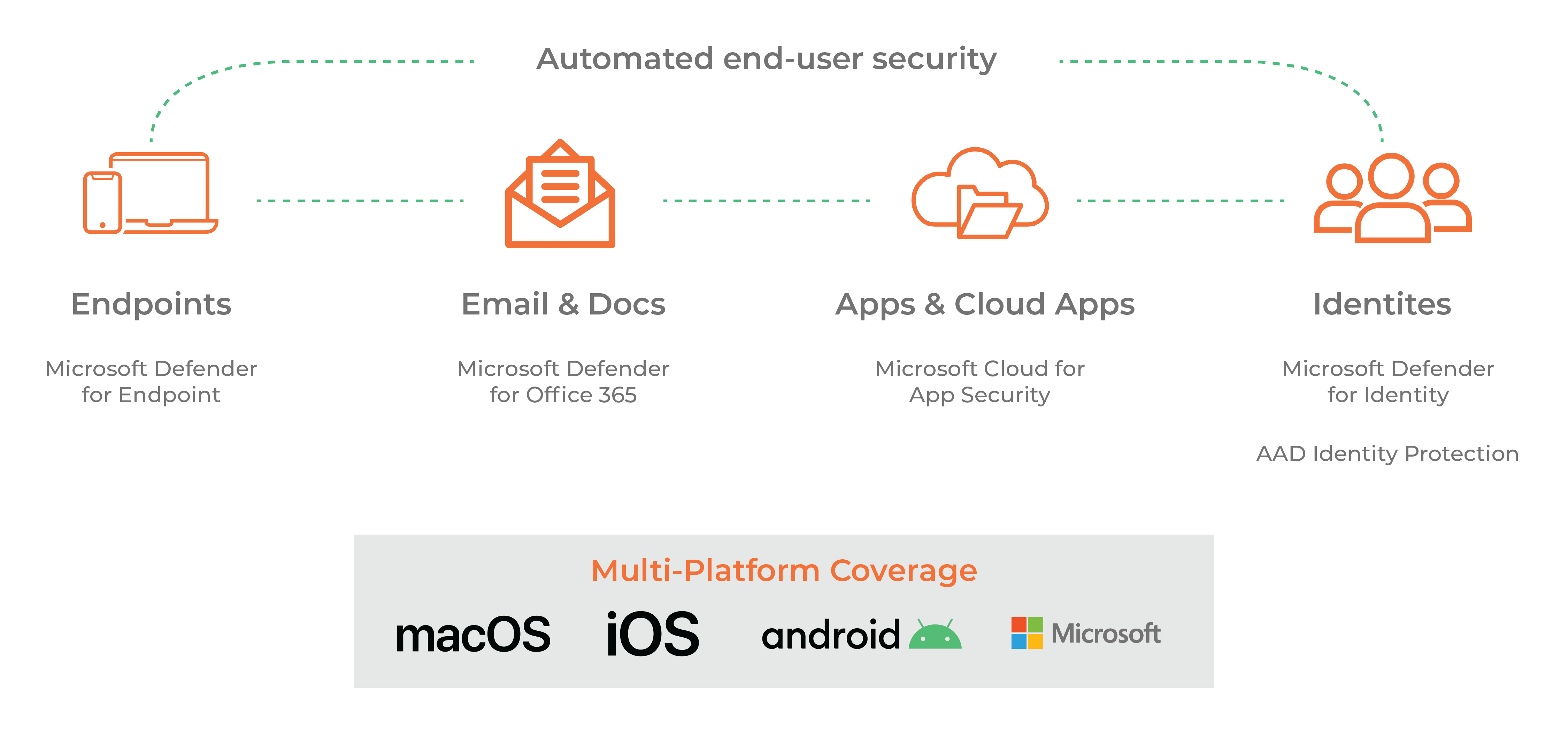
Microsoft 365 Defender is a unified pre- and post-breach enterprise defence suite that natively coordinates detection, prevention, investigation and response across endpoints, identities, email, and applications to provide integrated protection against sophisticated attacks. The following image displays the complete array of products within the Microsoft 365 Defender suite.
HOW IT WORKS
Microsoft 365 Defender uses behavioural sensors, cloud security analytics, and threat intelligence to prevent, detect, and respond to advanced threats on different platforms. It provides real-time protection against advanced threats on endpoints and helps detect and investigate identity-based attacks in real time. It also offers vulnerability management and assessment, attack surface reduction, automatic investigation and remediation and managed hunting services.
FEATURES AND BENEFITS
Let us cover six ways organisations can use Microsoft 365 Defender to enhance their overall security posture.

Threat Detection and Response: Microsoft 365 Defender utilises advanced threat intelligence and machine learning algorithms to detect and respond to various cyber threats. It continuously monitors and analyses data across endpoints, email, and cloud applications to identify suspicious activities, malware and other indicators of compromise. This enables organisations to quickly detect and respond to potential cyberattacks, minimising the impact of security incidents.
Endpoints: Microsoft Defender for Endpoint (MDE), provides comprehensive endpoint protection against a wide range of threats on different device types, such as laptop and mobile devices. MDE runs Next Generation Protection on the local devices and provides real-time data to the Defender cloud service. By securing endpoints, organisations can significantly reduce the risk of successful cyberattacks.
Defender for Endpoint is already part of the Windows operating system which makes the devices easy to configure and onboard to the Defender cloud service, depending on how you manage your Windows endpoints, Defender can be integrated with Microsoft Intune to easily onboard and configure devices using relevant policies. MDE also supports macOS, Linux, iOS, and Android.

Email and documents: Microsoft Defender for Office 365 safeguards organisations against email-based threats, including phishing attempts, malicious attachments, and business email compromise (BEC) attacks. It employs advanced threat intelligence, anti-phishing technologies, real-time link scanning to detect and block malicious emails, protecting users from falling victim to cybercrime through email-based attacks.

Identities: Microsoft Defender for Identity and Entra ID (Azure Active Directory) help organisations enhance their identity and access management practices. It enables organisations to enforce strong authentication, implement multi-factor authentication (MFA) and manage access controls to prevent unauthorised access to sensitive resources. By securing user identities, organisations can thwart common cybercrime tactics, such as unauthorised access and credential theft. The Defender portal will receive signals from Entra ID and endpoints, as well as Active Directory domain controllers in a hybrid environment. This way Defender can alert to potential compromised accounts and behaviour anomalies from your Active Directory.
Cloud Apps: Microsoft Defender for Cloud Apps (MDAC) provides visibility and control over 25,000 cloud applications, including Office 365, detecting and mitigating risks associated with cloud usage. It helps organisations identify and respond to potential data breaches, unauthorised access, and risky user behaviours within cloud services. MDAC is used with Conditional Access policies to manage what activities users can perform on their devices, for example blocking of downloads from the company OneDrive to a personal computer. By monitoring and securing cloud applications, organisations can better protect their data and mitigate cloud-related cyber risks.

Unified Security Management: The Microsoft 365 Defender portal offers a centralised management console for monitoring and managing security across services within the Microsoft 365 Defender suite. It provides a unified view of security events, alerts, and recommendations, enabling organisations to streamline their security operations and respond effectively to cyber threats.
TOP CYBER CRIME STATISTICS

Global
- The global annual cost of cybercrime is predicted to reach $8 trillion annually
in 2023 - The next five years are due to see a 15% increase in cybercrime costs reaching
10.5 trillion by 2025 - 80% of reported cyber crimes are generally attributed to phishing attacks in
the technology sector - Cybercrime earns cybercriminals $1.5 trillion every year. Small businesses
account for 43% of cyber attacks annually - 2021 was one of the costliest years in terms of data breaches through
phishing attacks in the last 17 years - Ransomware will cost its victims around $265 billion annually by 2031
- Around 236 million ransomware attacks occurred globally in the first half of
2022.

US
- Data breaches cost businesses an average of $4.35 million in 2022
- 1 in 2 American internet users had their accounts breached in 2021
- 53.35% of US citizens were affected by cybercrime in the first half of 2022
- Around 1 in 10 US organisations have no insurance against cyber-attacks

UK
- 39% of UK businesses reported suffering a cyber-attack in 2022
- The average cost of a cyber-attack for a smaller business is £4200 with the cost to medium and large businesses rising to £19,400 and that doesn’t take into account the potential damage to the businesses reputation and loss of confidence from clients and consumers

AUS
- There is a rise in the average cost per cybercrime report to over $39,000 for small businesses, $88,000 for medium businesses, and over $62,000 for large businesses. An average increase of 14%
- Ransomware attacks have increased by nearly 500% since the start of the COVID-19 pandemic
MICROSOFT DEFENDER FOR ENDPOINT
Earlier in the guide we discussed all the products in the Defender suite and this section will dive deeper into Microsoft Defender for Endpoint and its features and give some real-world examples.
Microsoft Defender for Endpoint is an enterprise endpoint security platform designed to help enterprise networks prevent, detect, investigate, and respond to advanced threats. It is an industry-leading, cloud-powered endpoint security solution that helps to secure against ransomware, file-less malware and other sophisticated attacks across platforms.
Defender for Endpoint uses a combination of technology built into Windows and Microsoft’s robust cloud service. It offers advanced post-breach detection sensors collecting a vast array of behavioural signals from your machines. It also offers next-generation antimalware, attack surface reduction rules, device control (such as USB), endpoint firewall, network protection, web control / category-based URL blocking, device-based conditional access and controlled folder access.
HOW IT WORKS
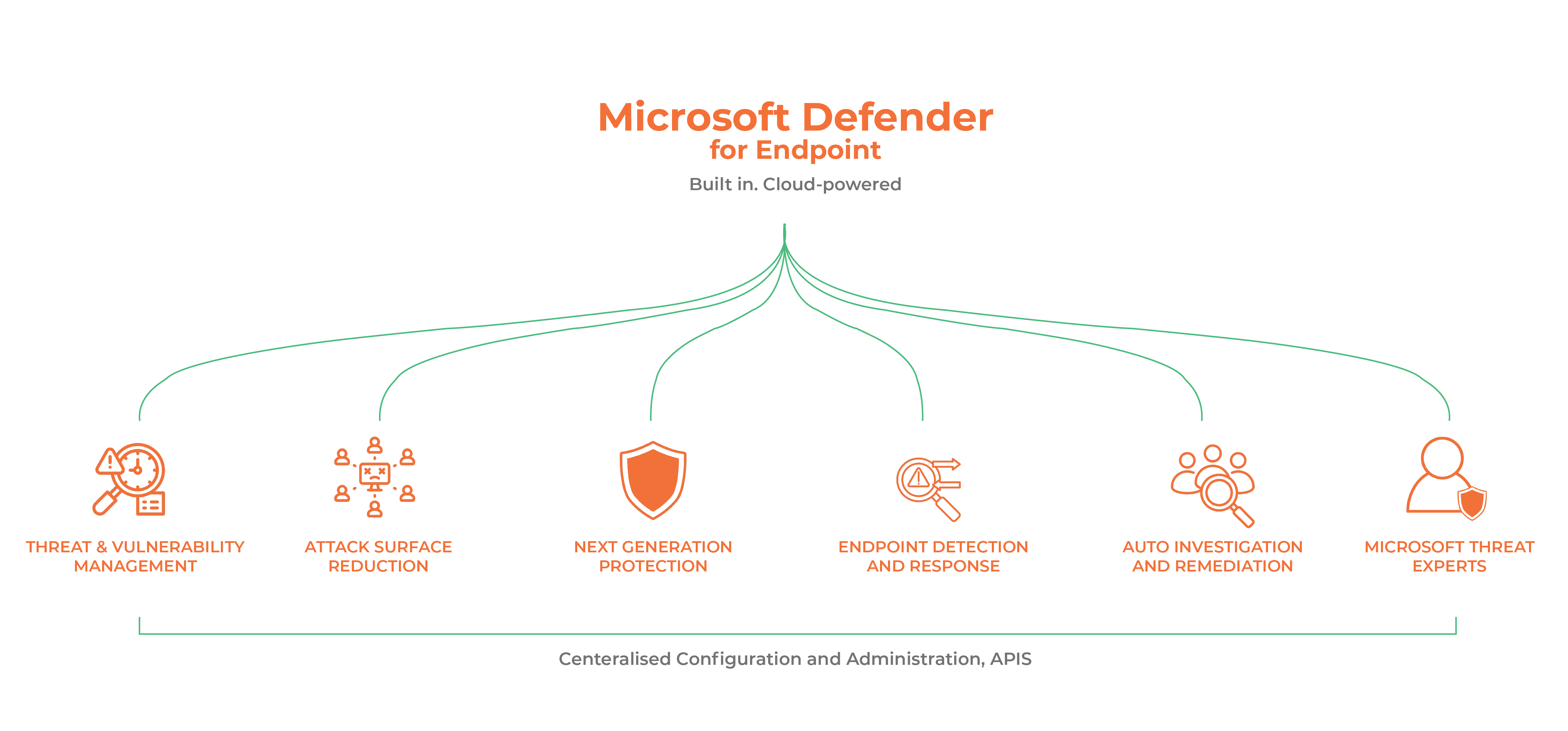
Microsoft Defender for Endpoint uses behavioural sensors to monitor system activities and detect suspicious behaviour. It also uses cloud security analytics to identify potential threats in real time. Threat intelligence is used to identify known threats and provide insights into new ones. Microsoft Defender for Endpoint also offers vulnerability management and assessment capabilities that help businesses discover security vulnerabilities and prioritise them with security recommendations.
Microsoft Defender for Endpoint can operate as Microsoft Endpoint Detection and Response (EDR) to form a security solution that helps organisations detect and respond to advanced threats on their endpoints. It provides real-time visibility into security incidents and provides automated responses to remediate threats. Microsoft Defender for Endpoint is an EDR solution that uses behavioural sensors, cloud security analytics, and threat intelligence to prevent, detect, and respond to advanced threats on Windows, Linux, Mac, iOS, and Android devices. It also offers vulnerability management and assessment, attack surface reduction, automatic investigation and remediation, and managed hunting services.
FEATURES AND BENEFITS
Microsoft Defender for Endpoint offers a wide range of features and benefits that help protect your organisation from advanced threats. It delivers preventive protection, post-breach detection, automated investigation and response for endpoints. It has two plans: Plan 1 and Plan 2.

Plan 1 offers capabilities such as:
- Advance security features: Next-generation protection (includes
antimalware and antivirus) - Attack surface reduction: Reduces the attack surface, for example
blocking MS office products from creating child processes - Manual response actions: For example, isolating a device by disconnecting
it from the organisations network - Centralised management in the Microsoft 365 Defender portal
- Security reports: Easy access to information about detected threats and
actions to address those threats - Device Compatability: Support for Windows 10, Windows 11, iOS, Android,
macOS, and Linux devices
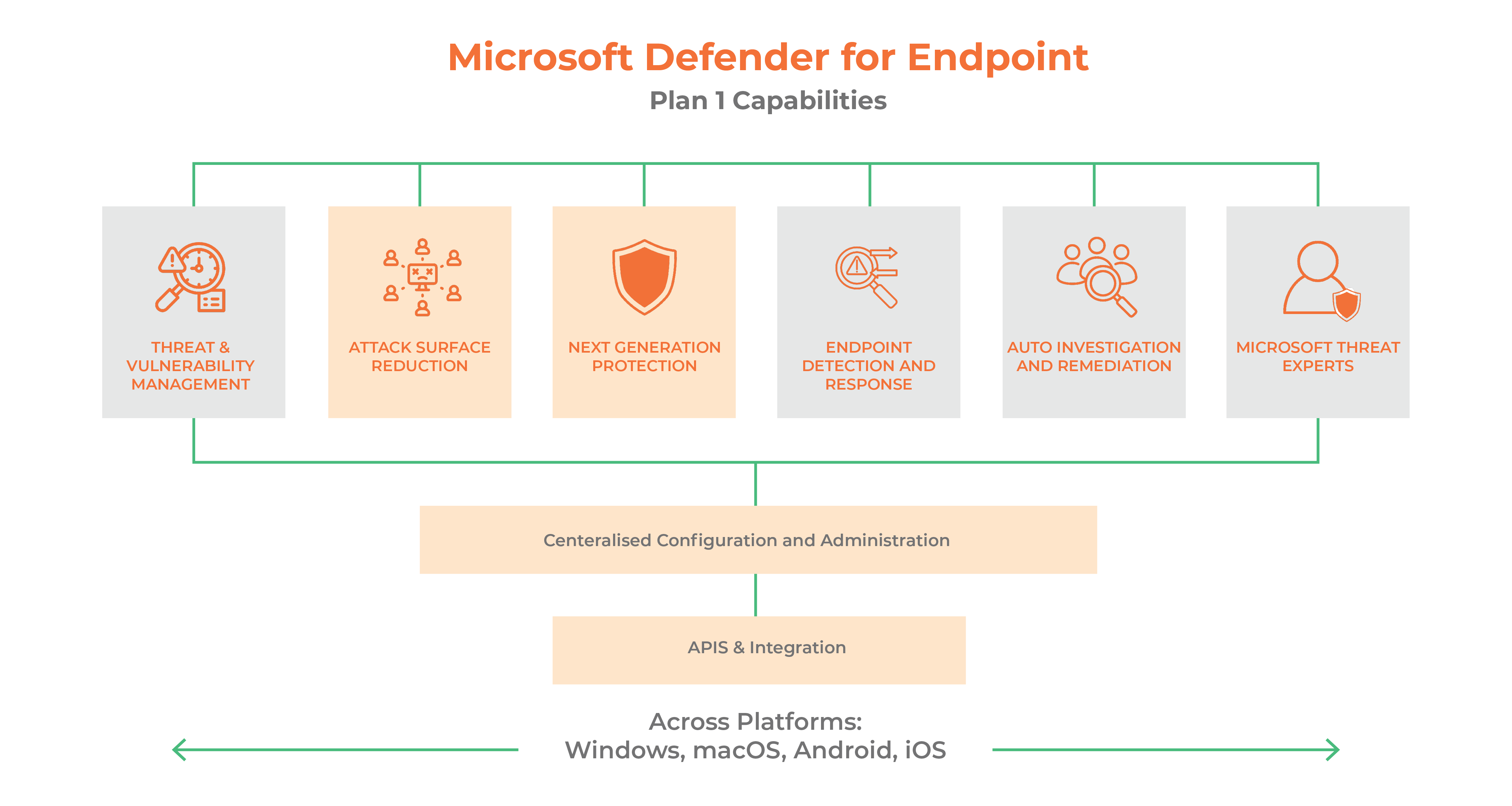

Plan 2 has all of the Defender for Endpoint Plan 1 capabilities, plus:
- Threat and vulnerability management: Using sensors within the tool, Microsoft Defender for Endpoint will discover, prioritise and remediate misconfigurations within the endpoints in real-time. Using insight into application usage patterns, Microsoft Defender for Endpoint can prioritise the highest value assets, such as business-critical applications, confidential data and highest value users against these types of attacks
- Device discovery: Helps you find unmanaged devices connected to your corporate network without the need for extra appliances
- Device inventory: Shows a list of the devices in your network where alerts were generated. By default, the queue displays devices seen in the last 30 days. At a glance you’ll see information such as domain, risk level, OS platform and other details for easy identification of devices most at risk
- Threat Analytics: A set of reports from expert Microsoft security researchers covering the most relevant threats. Each report provides a detailed analysis of a threat and extensive guidance on how to defend against that threat. It also incorporates data from your network, indicating whether the threat is active and if you have applicable protections in place
- Automated Investigation and Response (AIR): AIR capabilities are designed to examine alerts and take immediate action to resolve breaches automatically and without the need for manual intervention by a security analyst. AIR capabilities significantly reduce alert volume, allowing security operations to focus on more sophisticated threats and other high-value initiatives
- Advanced hunting: Advanced hunting is a threat-hunting tool that uses specially constructed queries (using Kusto Query Language) to examine the past 30 days of event data in Microsoft 365 Defender. Organisations can use advanced hunting queries to inspect unusual activity, detect possible threats, and even respond to attacks. For example, lookup processes that performed LDAP authentication with clear text passwords on endpoints
- Endpoint Detection and Response (EDR): When a threat is detected, alerts are created in the system for an analyst to investigate. Alerts with the same attack techniques or attributed to the same attacker are aggregated into an entity called an incident. Aggregating alerts in this manner makes it easy for analysts to collectively investigate and respond to threats
MIGRATING TO DEFENDER FOR ENDPOINT
At Insentra, we are working with many customers looking to migrate from third party endpoint protection products to Microsoft Defender to streamline and simplify their security solutions and operations.
By including Defender for Endpoint as part of the operating system in Windows, Microsoft have streamlined the migration and onboarding process.
Devices can be on-boarded into Microsoft Defender for Endpoint while running a third-party endpoint protection solution. This enables an organisation to run for a period of coexistence, while collecting security signals from endpoints and without reducing their security posture. When ready, the organisation can remove the third-party agent which automatically puts Microsoft Defender into active mode, leaving no gap in protection.
The high-level migration process from an existing 3rd part solution is broken down into 3 phases.

PHASE 1 - PREPARE
- Update devices
- Prepare you team
- Configure device proxy and internet settings

PHASE 2 - SETUP
- Re-install Microsoft Defender Antivirus (if
required) *MDE is part of the OS in Windows
10/11, so typically is still installed but disabled - Onboard devices and enable Microsoft Defender
Antivirus in passive mode - Run a detection test to confirm that onboarding
was successful - Configure policies and settings
- Get updates for Microsoft Defender Antivirus

PHASE 3 - SWITCH
- Uninstall non-Microsoft endpoint
protection product - Switch Defender Antivirus to active mode
- Run a simulation to prove end-to-end
protection
REAL-WORLD EXAMPLE
Consider a medium-sized company using Microsoft Defender for Endpoint as part of their cybersecurity strategy. They have numerous endpoints (desktops and laptops) used by employees for day-to-day work. Let’s look at a scenario where an employee at a company receives a malicious email containing a disguised link, which if clicked, will trigger a ransomware attack.
Here’s how Microsoft 365 Defender can intervene and stop the attack:

Email Protection: Microsoft Defender for Office 365, the email security component of Microsoft Defender for Endpoint, scans incoming emails in realtime. It uses advanced anti-phishing technologies and threat intelligence to detect and block malicious emails, including those with suspicious links or attachments.

Link Scanning: When the employee receives the malicious email, Microsoft Defender for Office 365 scans the link embedded within it. It compares it against known malicious URLs and checks if it leads to a potentially harmful website.

Real-Time Analysis: Microsoft Defender for Endpoint analyses the behaviour of the suspicious link in real-time. It uses machine learning algorithms and heuristics to determine if the link poses a potential threat. It considers factors such as the website’s reputation, previous encounters with similar links, and known patterns of malicious behaviour.

Block and Alert: If Microsoft Defender for Endpoint determines the link is indeed malicious, it takes action. It can block the employee’s access to the website, preventing them from clicking on the link and exposing their system to the ransomware attack. Simultaneously, it alerts the security team about the attempted attack, providing them with details and insights for further investigation.

Incident Response: Upon receiving the alert, the security team can initiate incident response procedures. They can leverage the investigation capabilities of Microsoft Defender for Endpoint to analyse the attempted attack, identify any potential indicators of compromise, and take appropriate measures to contain and mitigate the threat.

Automated Investigation: With Microsoft 365 E5 licencing or the Microsoft Defender for Endpoint Plan 2 add-on organisations can leverage Automated Investigation and Response (AIR) capabilities. Given the never-ending flow of threats, security teams often face the challenge of addressing the high volume of alerts. Imagine having a virtual analyst in your Tier 1 or Tier 2 security operations team. The virtual analyst mimics the ideal steps that security operations would take to investigate and remediate threats. The virtual analyst could work 24×7, with unlimited capacity and take on a significant load of investigations and threat remediation.
LICENSING
Microsoft Defender for Endpoint licencing essentially comes in two flavours, Plan 1 and Plan 2 (see the above graphic on page 6/7 for the feature comparison).
Plan 1 is included with:
- Microsoft 365 E3 with the Microsoft 365 E5 Security add-on
Plan 2 is included with:
- Windows 11 Enterprise E5/A5
- Windows 10 Enterprise E5/A5
- Microsoft 365 E5/A5/G5 (which includes Windows 10 or Windows 11 Enterprise E5)
- Microsoft 365 E5/A5/G5/F5 Security
- Microsoft 365 F5 Security & Compliance
CONCLUSION
Microsoft Defender for Endpoint is a crucial component of the Microsoft 365 Defender suite, offering comprehensive endpoint protection against a wide range of cyber threats. By using behavioural sensors, cloud security analytics, and threat intelligence, Defender for Endpoint provides real-time detection and response capabilities, helping organisations quickly identify and mitigate potential security incidents.
With its advanced threat detection and response features, Microsoft Defender for Endpoint empowers organisations to safeguard their endpoints, prevent ransomware attacks, and protect against file-less malware. Its integration with other Microsoft Defender products, such as Defender for Office 365 and Defender for Identity, strengthens overall security posture by providing protection against email-based threats and enhancing identity and access management practices.
Moreover, Microsoft 365 Defender’s centralised management console streamlines security operations, offering a unified view of security events, alerts, and recommendations.
As cybercrime continues to pose significant risks to organisations worldwide, the need for robust cybersecurity solutions offered by Microsoft Defender for Endpoint becomes increasingly evident. With its comprehensive features and benefits, coupled with seamless onboarding for existing Windows users, migrating to and adopting Defender for Endpoint can be a strategic move towards enhancing an organisation’s cybersecurity resilience.
By leveraging the capabilities of Microsoft Defender for Endpoint, organisations can proactively detect, respond and mitigate cyber threats, ultimately safeguarding their sensitive data, digital assets, and operations from the ever evolving landscape of cybercrime.
DOWNLOAD THE COMPLETE GUIDE

Thank you for downloading the Complete Guide to Microsoft Defender for Endpoint.
We’ve sent a copy to your inbox. Remember to mark hello@insentragroup.com as a “safe sender”, and to check any junk or spam folders so you receive your copy.


We’ve sent a copy to your inbox. Remember to mark hello@insentragroup.com as a “safe sender”, and to check any junk or spam folders so you receive your copy.
Consult Chat Discuss with our experts!
With the understanding that not all email archive migration projects are the same, our Email Archive Pre-Planning Assessment supports the diverse conditions found in organisations of all sizes, from enterprise environments to small businesses.
What kind of data are you migrating? Whether you are still in the planning phase or have begun your migration journey, you face a complex task.
According to a recent study conducted by Gartner, 83% of data migration projects either fail or exceed their budgets and schedules. It’s not a hidden fact that data migrations can be complex and stressful, however careful preparations will prove invaluable during the migration.









