One of my colleagues, Nick Thomas, wrote a great blog on “The Ultimate Guide to Microsoft Intune”. If you are new to Intune, head over to his blog to get further information on what it can do for your organisation. For those of you who have already adopted Microsoft Intune, please continue reading!
I was recently involved in migrating a customer’s mobile devices from their current Mobile Device Management (MDM) solution to Microsoft Intune. The customer has a strict “Apple only” mobile policy with a mix of end-users using either corporate and/or personal devices. The customer was flexible around enrolment options and wanted to test several scenarios, however, they had 2 essential requirements:
- The device could not be erased during the migration from their current MDM solution to Microsoft Intune, and
- Only work accounts were to be added to the Microsoft mobile apps i.e. they didn’t want to permit end users to add personal accounts to Outlook or OneDrive mobile apps.
NEXT STEPS
During the discovery process we decided all iOS devices would be enrolled using the Intune Company Portal app which would allow users to gain access to the customers email, files, and apps. Once the device is enrolled it would then become managed, allowing the customer to assign policies. I uploaded the device serial numbers as corporate identifiers then used an Azure AD dynamic security group to determine which were corporate and which were personally owned devices. There was a standard compliance policy applied to all devices and corporate owned devices had specific configuration profiles applied based on business requirements. Conditional Access policies and app protection policies were applied to all apps.
RESOLUTION
To ensure we met the two essential requirements for the customer, the following was implemented…
It was decided all users would enrol their device (regardless of whether the device is corporate or personal) using the Intune Company Portal app. However, the customer wanted to give their end users the choice of selecting whether the device was a corporate owned device or personally owned device which is easily configured within Microsoft Intune as follows:
- Browse to Microsoft Endpoint Manager admin centre > Devices > iOS/iPadOS > Enrolment type profiles
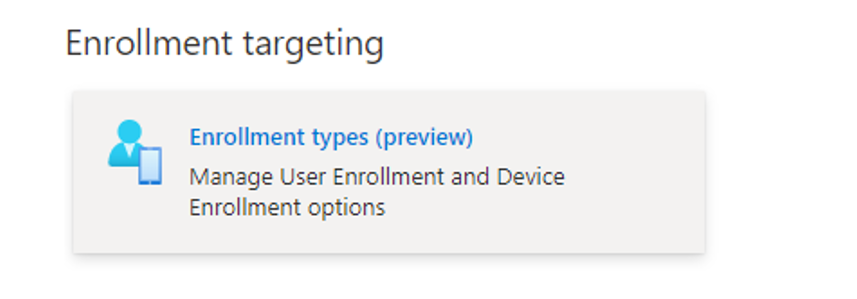
- Create a new iOS/iPadOS profile (give it a unique name)
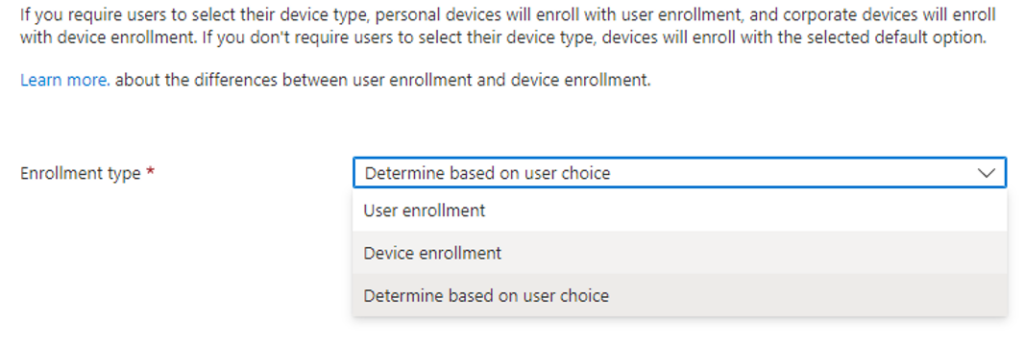
- Select enrolment type settings (for this scenario we want the user to make the choice)
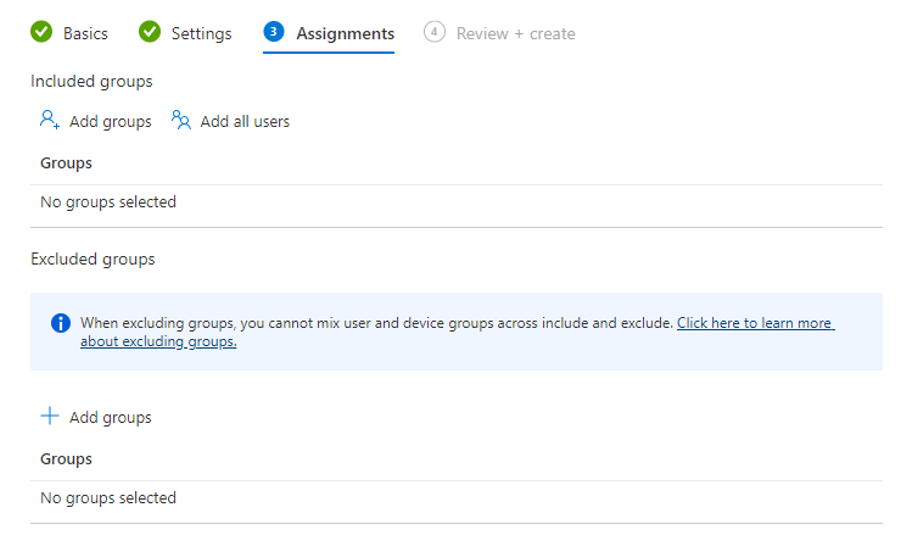
- Select your assignments and you are good to start testing enrolment
This is a very useful option for customers to implement and involves little to no disruption to existing end user devices. Microsoft have detailed the end user experience in a YouTube video which can be shared with end users as part of the change management process.
To ensure only work accounts can be added to the Microsoft mobile apps an app configuration policy needs to be implemented and assigned to each app you wish to protect. For this scenario, we are going to target Microsoft Outlook app.
- Browse to Microsoft Endpoint Manager admin centre > Apps > App configuration policies
- Create a new profile (give it a unique name) with the following settings
| Attribute | VALUE |
| Device enrolment type | Managed devices |
| Platform | iOS/iPadOS |
| Targeted app | Microsoft Outlook |
- Using the configuration designer, set the following
- Allow only work or school accounts set to Enabled is the important feature that will block personal accounts
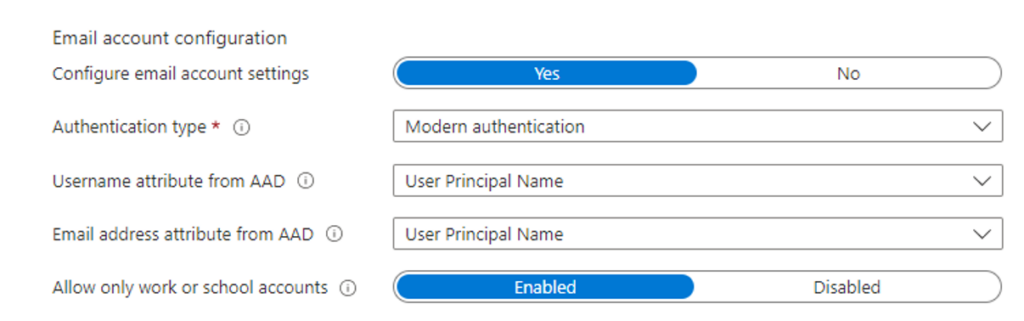
- Select your assignments and you can start testing
Unfortunately, Microsoft does not allow you to group apps into one app configuration policy. If you want to allow ‘only work account’ access to other apps you will need to replicate this policy for your chosen apps, replacing the target app with your desired app, for example, OneDrive.
If you want to know any further information around adopting Microsoft Intune and how Insentra can help, our Microsoft FastTrack services may be exactly what you are looking for!
Hopefully this has been informative and helpful! If you need any further clarification, or a no-thrills chat, contact us at Insentra.