The announcement, Login to Windows virtual machine in Azure using Azure Active Directory authentication, has opened up some very interesting use cases for secure management access to Azure environments.
If you haven’t seen this announcement yet, it allows you to sign into Windows VMs running in Azure with Azure AD credentials and manage access via Role-Based Access Control (RBAC) policies. In essence, it is creating an Azure AD join for the machine, so users can use their Azure AD credentials to authenticate to it with Remote Desktop Protocol (RDP).
This feature is supported on Windows Server 2019 Datacenter edition or Windows 10 1809 and later VMs running in Azure. It is worth mentioning that once you enable this capability on a VM, you cannot join it to a traditional AD domain (either on-premises or Azure AD DS). If you need to do so, you will have to disconnect the VM from your Azure AD tenant by uninstalling the extension.
HOW TO ENABLE THE FEATURE
When you provision a new VM, you now have the option to enable the feature.
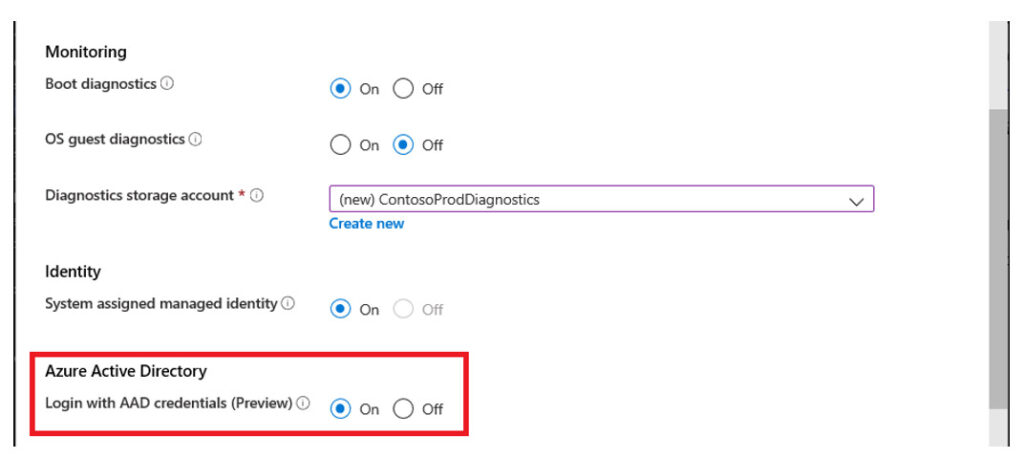
SECURING ACCESS
To establish an RDP connection to a VM with this feature, you must be connecting from a client which is either:
- Azure AD Joined
- Hybrid Azure AD Joined
- Azure AD Registered
There is now an Enterprise Application which represents this Authentication method, called “Azure Windows VM Sign-in” as shown below:
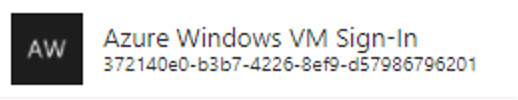
Azure Windows VM Sign-in will enable us to create conditional access policies for these connections, and from there we can do things like requiring the device to be marked as compliant by Endpoint Manager, or even require Multi Factor Authentication (MFA).
You may be thinking “how do I perform MFA with the standard Remote Desktop Client”? The answer is as easy as it is elegant… the MFA requirement can be satisfied if the user has signed into their endpoint device with Windows Hello for Business!
To test this functionality, I have configured a lab with the following:
- A Windows 2019 server in Azure with this feature enabled
- A user account with the RBAC permission
- A conditional access policy requiring MFA for “Azure Windows VM Sign-in”
- A Hyper-V VM, which is Azure AD joined with Windows Hello for Business configured I have observed the following in my tests
- If I sign into the VM with Windows Hello for Business I can log into the server with RDP
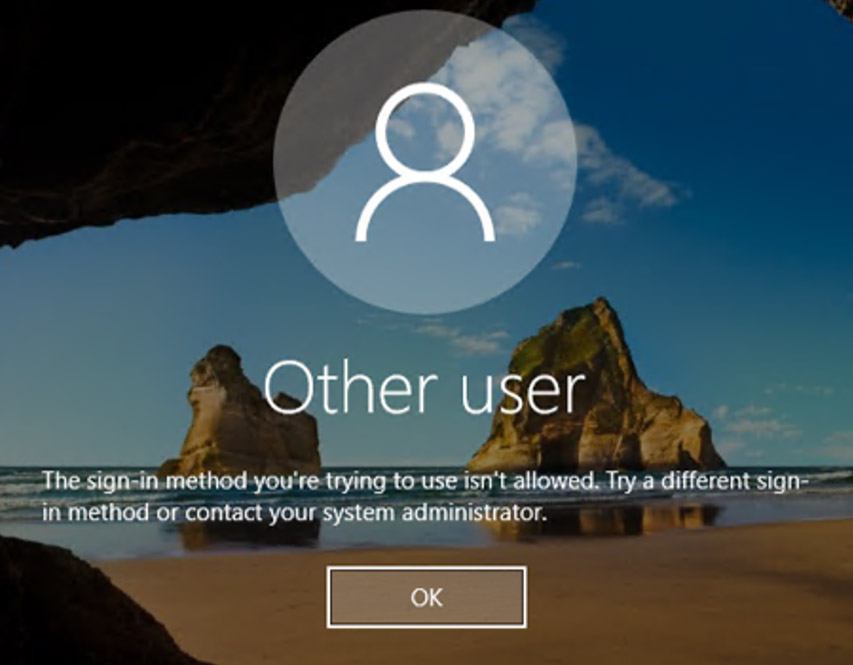
- If I sign into the VM with a password, I get the below error when trying to log into the server with RDP
TYING IT ALL TOGETHER
If we put all this together, we can achieve the following:
- Tightly control which accounts can sign in to the VM with RBAC, for both admin and user-level access
- Require users to use a corporate device and attest it aligns to an expected management and security posture
- Require they sign into their device with Windows Hello for Business and optionally mandate biometric methods
If you want to crank this up the next level for access to high-value resources, you can add time-based access controls, auditing and optional approval workflows by implementing:
- Privileged Identity Management (PIM) as part of Azure AD Premium 2 and require users to request elevation to activate their login RBAC role
- Just in Time VM access as part of Azure Defender and require users to request network-level RDP access to the VM
SUMMARY
Aside from the stated use cases in the announcement, I see this as a way to leverage the principles of Zero Trust to provide a secure privileged access workstation (PAW) jump box to manage cloud resources in Azure. On top of this, we can even incorporate some aspects of passwordless by leveraging Windows Hello for Business for second-factor authentication. All of this can directly tie into a Privileged Access Strategy as a part of a comprehensive implementation of the Enterprise Access Model.
For more information on security in Azure, my new blog series ‘Business Continuity and Protection from Malicious Attacks in Microsoft Azure’ is full of tips and tricks.