Picture this: a bunch of big-name companies are rolling up to the Linux server party and they’re all like, “Hey, you know what this bash needs? Antivirus!” They’re waving their arms, tossing around buzzwords and acting like they’ve just invented the wheel.
Meanwhile, over in the corner is Red Hat, cool as a cucumber, leaning back with a smirk. They’re sipping on their coffee, watching the spectacle and they’re like, “Antivirus? Seriously? We’ve got SELinux, mate! As long as your Linux servers aren’t shaking hands with any of those non-Linux services, we’re all good. No need for any extra fluff.”
However, big-name companies won’t let up. “But what about the threats, the malware, the…” they sputter.
Red Hat just chuckles. “Look, if you keep your sticky fingers off our servers, no shady protocols, no weird implementations, SELinux has got this. We’re like a bouncer at a nightclub – we know who to let in and who to toss out.”
So now you’ve got this scene where big-name companies are trying to sell ice to Eskimos, and Red Hat’s just enjoying the show, probably thinking, “Mate, we’ve got it covered. Keep your antivirus; we’re good with our SELinux swagger.”
So, there’s Red Hat, chilling in the corner, confident as ever about SELinux keeping things in check. But then, just to make sure the party stays drama-free and to put an end to all the antivirus chatter, they decide to throw in a little surprise of their own: Red Hat Insights with malware detection.
Red Hat stands up, clinks a glass to get everyone’s attention and says, “Alright, listen up, folks. We heard you. You want malware detection? Boom! Here’s Red Hat Insights with malware detection. It’s like SELinux on steroids – your servers are now not just bouncer-protected, but they’ve got a whole security team on standby.”
Big-name companies pause, mid-buzzword, looking a bit flustered. “Uh, wait, what?”
Red Hat just grins, “Yep, you heard us right. We’ve got Insights now, sniffing out malware like a bloodhound. So, no need to worry your pretty little heads about our servers. SELinux and Insights – it’s a double whammy. Our servers are now a fortress, and your antivirus pitch? Consider it retired.”
With that, Red Hat sits back down, sipping their coffee, while the rest of the room starts to realise that maybe, just maybe, they underestimated the cool cat in the corner. And from then on, no one dared to question the security of Red Hat’s Linux servers again.
Features of Red Hat Insights Malware Detection
Let’s get to business, shall we? This section will focus on the technical aspect of Insights malware detection.
The following outlines the elements of the Insight’s malware detection:
- IBM X-Force Threat Intelligence Signatures
Ever heard of the IBM X-Force AKA Red Hat’s secret weapon? They’re like the Sherlock Holmes of cybersecurity. They’ve got this regularly updated database of known threats. It’s like having a team of detectives constantly feeding us the latest scoop on the bad guys.
- YARA Signature Detection
YARA’s like the Swiss Army knife of malware detection. It describes malware types through patterns, with a set of strings and a Boolean expression defining a rule. Think of it as a super-sleuthing formula. When one or more conditions in a signature are found on a scanned RHEL system, YARA records a hit on that system.
- Malware Detection Service
Our service within Red Hat Insights doesn’t just sit around looking pretty. It actively scans systems using the signatures and patterns from our friends at IBM X-Force and YARA. It is like an around-the-clock security patrol.
- Integration and Reporting
Red Hat malware detection service isn’t just flying solo. It’s fully integrated into the Red Hat Insights platform. It’s like having a personal assistant that’s got it all covered. You can view and manage security alerts right alongside other system health and performance metrics. Think of it as your one-stop shop for everything your system needs.
So, to wrap it all up, Red Hat’s got the ultimate dynamic duo for malware protection. By combining the detective skills of IBM X-Force threat intelligence with the super-bouncer YARA-based scanning, Red Hat Insights delivers a powerhouse solution for detecting malware threats in the environment.
Insights Malware Detection Configuration
- If the insights-agent is installed, install the following package on a system:
# dnf install yara - Perform a test run, to validate the configuration
# insights-client --collector malware-detection - Once the test malware scan is finalised, navigate to cloud.redhat.com/insights/malware/signatures and verify if malware analysis is visible for the host in scope:
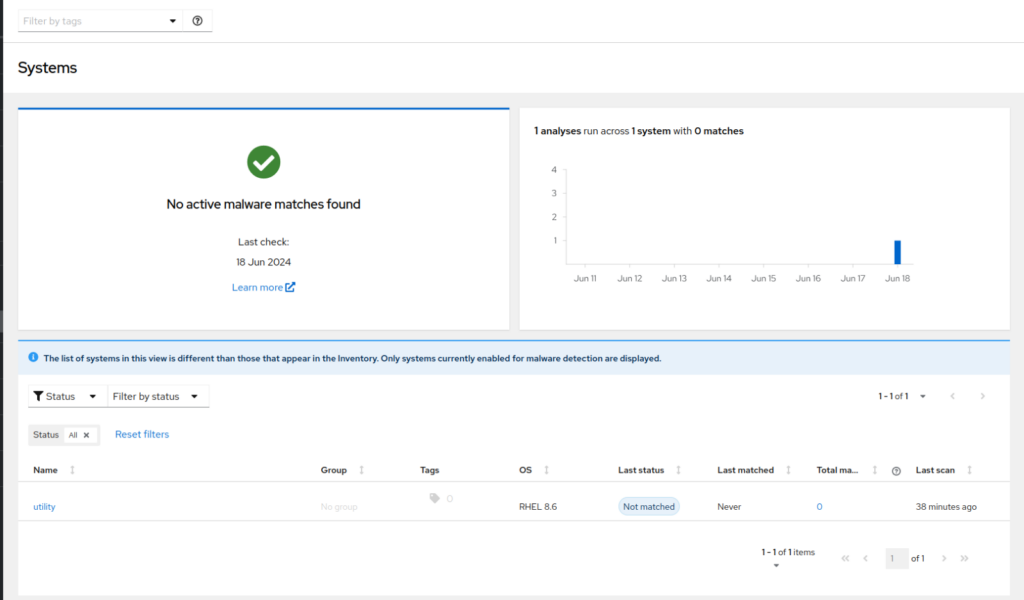
- Enable full malware detection on the system, modifying the configuration file:
# sed -i 's/test_scan: true/test_scan: false/'
/etc/insights-client/malware-detection-config.yml - Repeat the scan
# insights-client --collector malware-detection There you have it! Now you know how to leverage Red Hat Insights to protect your organisation against malware. If you’d like to learn more about Red Hat Insights, check out the Insentra Insights page for more helpful blogs like this. Contact us today for assistance on improving your security posture.