WHAT IS IT?
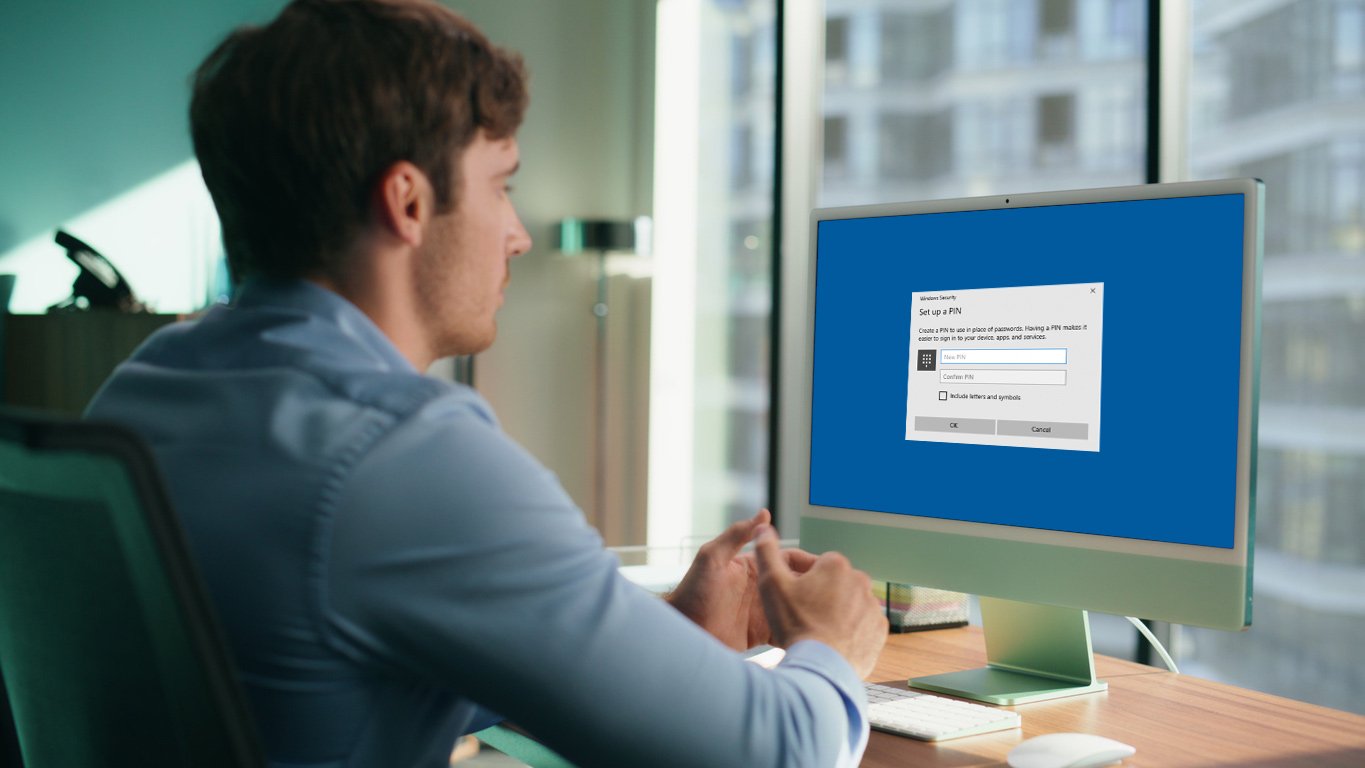
Windows Hello, or Hello for business. A name we’ve all heard at some point I’m sure, it’s that pop-up you get on a new device that asks you to set up a PIN number when logging in right?
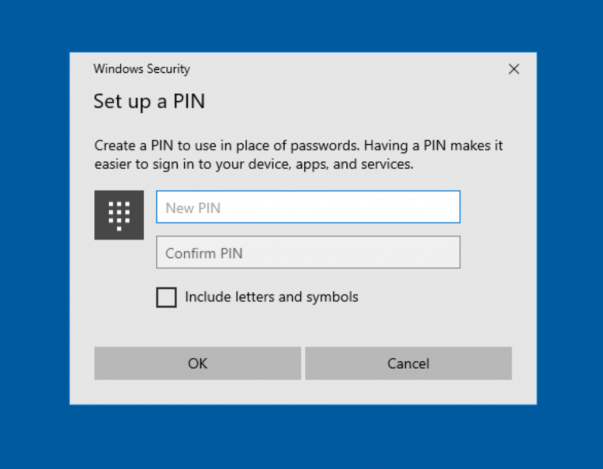
Well, the more you dig into Hello for business, the more interesting it gets. There is a plethora of different ways that you can authenticate your users and you can set up multiple conditions that need to be met to achieve access. These don’t have to be physical actions for your end users to complete either, they can be passive factors to improve the robustness of your existing cyber security practices.
Recently while working with one of our clients in the financial sector, there was a requirement to lock down access, while causing as little disruption to the end user as possible. We achieved this by utilising a feature of Windows Hello for business called “Multifactor Unlock”.
While it is good practice to replace user passwords with a PIN or biometric verification, a second layer of verification is now a standard practice. When the term “Multi Factor Authentication” (MFA) is thrown around, the first thing you think of is a text message to your phone, or a code from an authenticator app. While that is correct, there is another side to it. Users do not want to have to enter a code or receive a call / text every time they log into their device, while this is commonplace to access certain resources it seems that the line has been drawn at the login screen of the physical device in front of you.
HOW DOES IT WORK?
So, what could be done if PINs alone don’t meet your company’s security needs, you want to prevent your end users from sharing their credentials or you have a need for your organisation to comply with a regulatory two-factor authentication policy?
Using Multi Factor Unlock has three stages
- First unlock factor credential provider
- Second unlock factor credential provider
- Signal rules for device unlock
These can be customised to suit the specific needs of the business; credential providers can be any of the following:
- PIN
- Fingerprint
- Facial Recognition
- Trusted Signal
- (Phone proximity, Network location and more)
RECOMMENDATIONS
Microsoft recommends using either PIN, Fingerprint or Facial Recognition as the default First Factor, this is already most likely what is being used and allows the end user to have a familiar login experience.
For the second factor it is recommended to point towards “Trusted Signal” which we will explore in a moment, and a backup second factor such as PIN, Fingerprint or Facial Recognition to avoid situations where a trusted signal is not an option, and the end user still needs to be able to work. This can be set to any / all of the default first factors (PIN, Fingerprint, Facial recognition) however, whichever factor was used to satisfy the first unlock factor cannot be used to satisfy the second unlock factor. “Each factor can therefore be used exactly once” as Microsoft so eloquently puts it.
For example, if PIN, Fingerprint and Facial Recognition are set in both the first and second factor, and the user logs in using a PIN, the second factor options offered to the user will be Fingerprint or Facial Recognition.
TRUSTED SIGNAL
Now let’s look at the trusted signal. This is something that you can add to look for certain environmental criteria in the background, the end user wouldn’t necessarily need to interact during this part of the authentication, so from their perspective the login process would not change at all from what they are used to.
The following can be used as a trusted signal provider:
BLUETOOTH DEVICE
- Computer
- Phone
- LAN/Network Access Point
- Audio/Video
- Peripheral
- Imaging
- Wearable
- Toy
- Health
This will require a certain type of device to be connected to the computer. You are also able to specify the signal strength required to satisfy the unlock request and what the minimum signal strength is before it locks the screen (handy if users often forget to lock their workstations when leaving their desk, especially if working in a public space, or shared environment).
IP CONFIGURATION
You can define one or more of the following values to use the IP configuration of the computer at login
- IPv4Prefix
- IPv4Gateway
- IPv4DhcpServer
- IPv4DnsServer
- IPv6Prefix
- IPv6Gateway
- IPv6DhcpServer
- IPv6DnsServer
- dnsSuffix
WI-FI
You can define one or more of the following values to use a specific network SSID or even access point MAC addresses, helpful for if you wish to seamlessly satisfy the second factor in an office environment.
- SSID
- Mac address of the wireless access point (BSSID)
- Security Type
TRUSTEDROOTCA
Contains the thumbprint of the trusted root certificate of the wireless network. This may be any valid trusted root certificate and you are able to define the required signal strength.
IMPLEMENTATION SCENARIO
In the scenario I mentioned earlier, our client opted to require Fingerprint or Facial Recognition as the First unlock factor and chose Trusted Signal and PIN for the second factor.
The trusted signal was set to look for a phone to be connected or a list of MAC addresses of their office access points, meaning that if the end user was in the office, then the second factor would be automatically satisfied. However, if the user was working outside of the corporate environment their business mobile phone would need to be connected via Bluetooth and within a certain range, or their PIN would need to be entered as well after satisfying the first factor of authentication.
Another scenario could be that if users are already using a PIN to access their device, then a second factor of fingerprint, or facial recognition could be added if for example, credential sharing is the specific issue that needs to be addressed and there is not a need for stringent security requirements.
This is one part of a much larger approach to improving cyber security. If you would like to know more then get in touch with us today!
RELATED ARTICLES
Microsoft registration of MFA and SSPR
Changes to Azure AD Multi Factor Authentication (MFA) Numbers for Hybrid Scenarios
Evolution Mail Agent with EWS and Multi Factor Authentication