Table of Contents
INTRODUCTION
Now that almost everything and everyone has gone digital, cybersecurity threats are everywhere. Hackers are getting smarter, their tools are more advanced and organisations face a constant risk of data breaches and system attacks. It’s like trying to guard a house when thieves keep inventing new ways to break in.
That’s where microsegmentation comes in—a fancy term for a simple idea. Instead of leaving your entire network wide open, you divide it into smaller, well-protected sections. Think of it as turning a single big house with open doors into a gated community where every room has its own lock. This approach helps stop attackers in their tracks, keeping them from moving freely and causing more damage.
UNDERSTANDING THE PROBLEM
According to Gartner, most networks today suffer from something called “network openness,” which means they are far too open. This is a big issue. Imagine this: once a hacker gets into one part of your network, it’s like they’ve been handed a skeleton key—they can roam around wherever they want. That’s how sensitive data gets stolen, systems get hijacked and organisations face chaos.
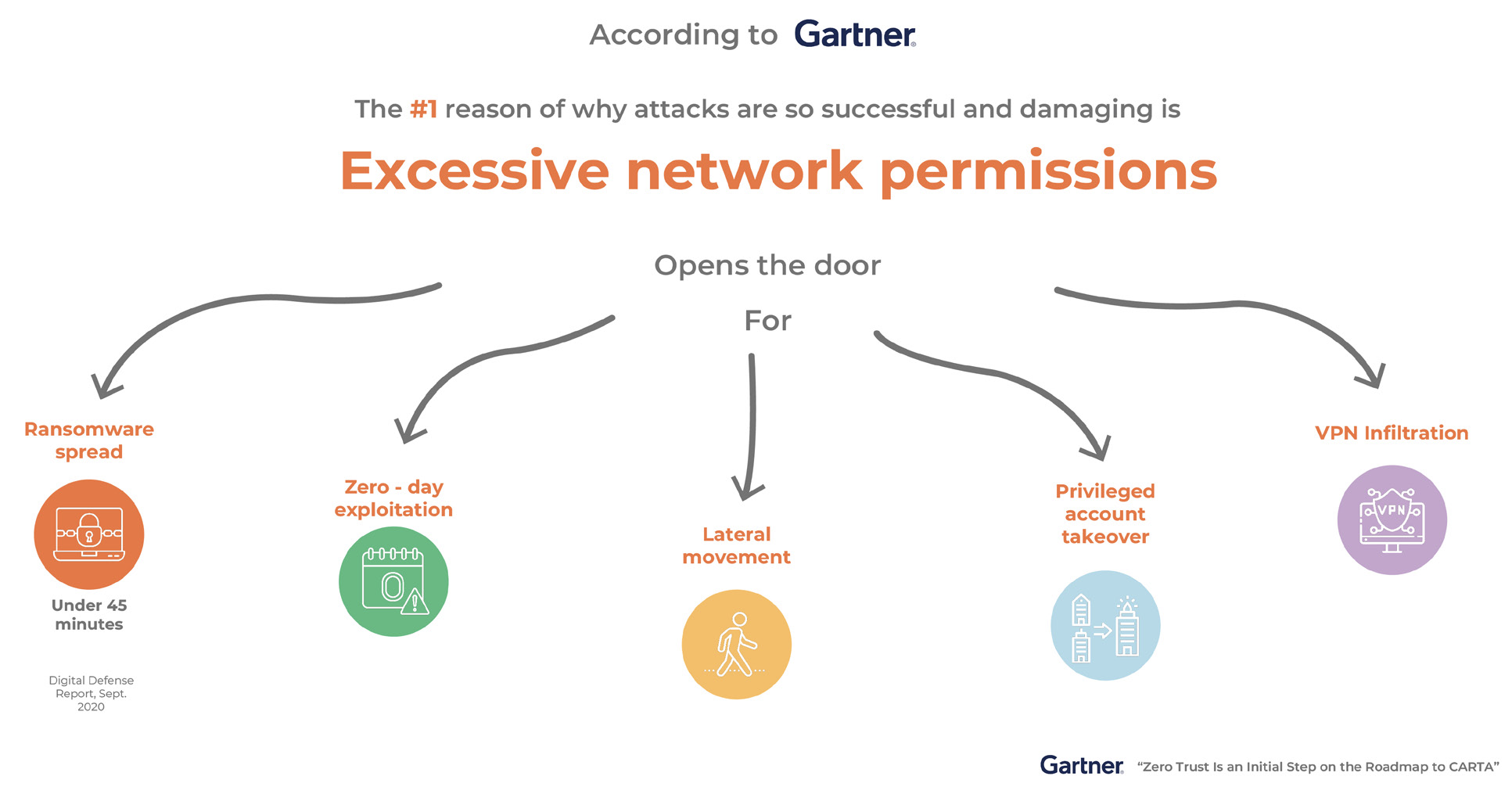
WHY ARE NETWORKS SO VULNERABLE?
01
Too Many Permissions
02
Hackers Moving Freely
03
Exploiting Unknown Flaws
WHY MICROSEGMENTATION MATTERS
According to IBM’s Cost of a Data Breach report, it takes an average of 266 days to identify and contain a data breach, with the average cost reaching a staggering $4.26 million. These figures highlight a glaring gap in security, giving hackers ample time to infiltrate, explore and steal data while remaining undetected.
The root of these successful breaches lies in the evolving threat landscape. The traditional “castle-andmoat” security model designed to protect the network perimeter—is no match against sophisticated threats that slip through the cracks. As more applications move to the cloud and organisations deepen their integration with partners, drawing a clear perimeter around the network has become a real challenge for security teams.
This perimeter-based approach works off the outdated idea that threats come from outside the network.
As a result, common solutions like IPS, IDS and firewalls mostly focus on North-South traffic (external to
internal).
It takes an average of 266 days to identify and contain a data breach, with the average cost reaching a staggering $4.26 million. 5
The problem is that most threats come from the inside the network. As IBM Distinguished Engineer Jeff Crume explains it, “You’re assuming the bad guy is on the outside, but what if that’s not the case? What if the bad guy is already on the inside?”
Over 75% of network traffic flows East-West—server-to-server communication within the network— creating the perfect route for lateral movement. Once inside, attackers can stealthily navigate East-West traffic, spreading across systems, looking for weaknesses and collecting data without triggering traditional perimeter defences.
To counteract this, organisations need to adopt modern security strategies that shine a light on East- West traffic, detect lateral movement and stop attackers in their tracks before they can exploit these blind spots. This is where microsegmentation comes in.
By breaking your network into smaller, controlled zones, you can make sure that even if one area is breached, the attacker can’t get far. It’s like having locked doors inside your house, so a thief in the living room can’t make it to the bedroom. This not only limits the damage but also gives organisations better control over who can access what.
WHAT IS MICROSEGMENTATION?
Let’s break it down. Microsegmentation is like creating mini fortresses within your network. Instead of having one big open space where everyone (and everything) can wander freely, microsegmentation divides the network into smaller, secure zones. Each zone has its own set of “rules” about who or what can enter, ensuring only the right people and devices get access.
Why does this matter? Well, it’s all about stopping hackers in their tracks. If they manage to break into one zone, they’ll find themselves stuck there, unable to roam around and cause more damage.
MICROSEGMENTATION IN ZERO TRUST
Microsegmentation is a natural fit for the zero trust approach, which follows the principle of “never trust, always verify.” By isolating each zone and enforcing strict access controls, microsegmentation ensures that no one—inside or outside the network—gets a free pass.
Every access request is verified, and even if attackers manage to break into one zone, they’re immediately contained, unable to move further. This makes microsegmentation a critical component of a zero trust security strategy.
According to the Gartner Market Guide for Microsegmentation, “By 2026, 60% of enterprises working toward zero trust architecture will use more than one deployment form of microsegmentation, which is up from less than 5% in 2023.”
By 2026, 60% of enterprises working toward zero trust architecture will use more than one deployment form of microsegmentation
THE CORE PRINCIPLES OF MICROSEGMENTATION
01
Granular Control
Think of it as setting boundaries at the smallest level. Instead of guarding just the front door of your network, microsegmentation keeps tabs on every room, closet, and drawer. It decides who can go where and under what conditions. For example, only your HR software might talk to the payroll system, while your marketing team’s tools are kept separate.
02
Containing Attacks
Hackers love to move around once they get inside a network. But with microsegmentation, they hit a dead end. Imagine a burglar breaking into one apartment but finding locked doors everywhere else. It’s especially handy against threats like ransomware, which spread by jumping from system to system.
03
Layered Security
Microsegmentation doesn’t just divide the network; it adds layers of protection. Even if one security measure fails, others are there to pick up the slack. It’s like having multiple locks on a door—host-based firewalls, software-defined networking, and hardware firewalls all work together to enforce the rules.
BENEFITS OF MICROSEGMENTATION
01
Stronger Security
By keeping your critical systems isolated and giving access only to those who truly need it, you reduce the risk of hackers or malware getting to sensitive data.
02
Easier Compliance
If your organisation has to follow rules like GDPR or PCI-DSS, microsegmentation is a big help. It gives you clear control and visibility over who has access to what, making audits less stressful.
03
Smoother Operations
Managing access across anetwork can be a headache, but microsegmentation simplifies things. With automation tools, you can create and enforce security rules without a ton of manual effort, saving time and cutting down on errors.
Microsegmentation is about taking control. It keeps your network safe, manageable and ready to tackle today’s cybersecurity challenges.
In short, microsegmentation is about taking control. It keeps your network safe, manageable and ready to tackle today’s cybersecurity challenges. Think of it as building a better, smarter defence system—one that works for you, not against you.
HOW MICROSEGMENTATION WORKS
Let’s walk through how microsegmentation actually happens. Think of it as setting up a superorganised security system for your network. It’s not about making things complicated—it’s about creating clear rules that keep your systems safe without slowing everyone down.
01
Lock the Doors First
The first thing you do is block all incoming traffic by default. Imagine closing every door in your house and locking them. Nothing gets in unless you explicitly allow it. This “default deny” setup is like putting up a big “No Entry” sign for anything suspicious. It’s your first line of defence against unauthorised access.
02
Decide Who Gets In
Next, you define who or what is allowed to communicate within the network. This step is all about setting boundaries based on what’s actually needed. For example, someone in the finance team doesn’t need access to marketing’s files, and vice versa.
You create these rules using tools like firewalls or software-defined networking (SDN). It’s a bit like giving each person a key that only opens the rooms they need to enter. This “least privilege” approach keeps things organised and limits potential risks.
03
Automate the Heavy Lifting
Manually setting up these rules for every single device or user can be a headache. That’s where automation comes in. Tools like Zero Networks use AI to analyse how your network behaves and automatically create the right rules for you.
Automation also helps spot and fix mistakes—because let’s face it, humans aren’t perfect. Plus, it ensures your security setup stays consistent, even as your network grows or changes.
04
Keep an Eye on Things
Once your microsegmentation is in place, the work doesn’t stop. Regular monitoring is crucial to make sure everything’s running smoothly. Think of it like checking your home security cameras to catch anything unusual.
Tools can alert you to anything suspicious, like someone trying to access areas they shouldn’t or unexpected traffic spikes. By staying on top of these alerts, you can quickly address any potential issues before they become big problems.
A Real-Life Example
Here’s how this works in action: One company used Zero Networks to automate their microsegmentation process. Everything was running smoothly when a ransomware attack hit. Thanks to microsegmentation, the attack was contained in one small part of their network, like a fire being locked in one room.
The result? No damage to critical systems and a lot less stress for their team. That’s the power of having these protections in place.
USE CASES FOR MICROSEGMENTATION
Here are some of the most common and impactful ways organisations use microsegmentation to strengthen their defences:
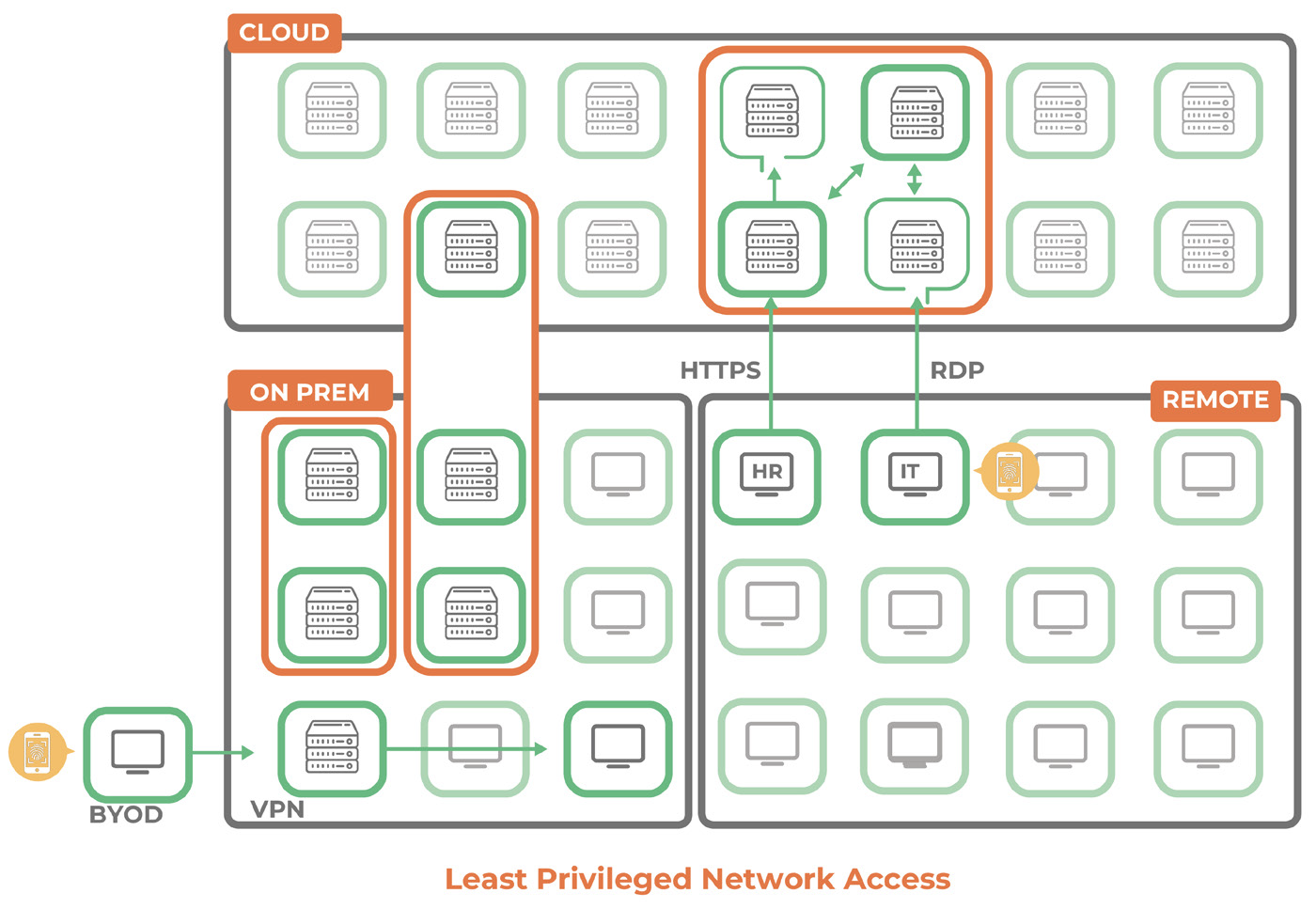
Application Ring-Fencing
Think of this as creating a secure bubble around an application. Application ring-fencing ensures that only the right users, devices or systems can interact with an application— and nothing else gets in or out.
Let’s take a financial app for instance. Microsegmentation can limit access to just your finance team. The web server tied to this app? It’s only allowed to talk to its back-end database servers. If you’ve got an HR app, you can restrict it so that only HR devices can connect, and only over the port where they get their work done.
Securing Remote Workforces and Vendors
Remote work and third-party vendors have become the norm, but you don’t need to give them full access to your network. Microsegmentation ensures that remote access is tightly controlled and limited to only what’s necessary.
Take a vendor using a VPN to troubleshoot an operational technology (OT) system. Instead of giving them access to your entire network— which is a disaster waiting to happe —you can segment their connection. They’ll only be able to access the OT system they need, and only after passing an identity check.
This targeted approach eliminates the “allaccess pass” problem that traditional VPN setups often create.
Supporting Cloud Migration
Migrating to the cloud can feel like opening Pandora’s box. But with microsegmentation, you can make sure only the right connections are happening between your cloud apps and on-premises systems.
Let’s say you’re moving an HR application to the cloud. You can set it up so that the app only talks to the on-premises database it needs and nothing else. This way, even as you embrace the cloud, you’re keeping a tight grip on security.
Microsegmentation ensures that your hybrid environment doesn’t turn into a free-for-all.
Privileged Just-in-Time Access
We all know that admin accounts are prime targets for attackers. With microsegmentation, you can make sure those accounts are only active when absolutely necessary, and only for as long as they’re needed.
Picture this: an IT admin needs to troubleshoot a server. Instead of leaving access open all the time, microsegmentation can grant them temporary access after they’ve verified their identity, say, with multi-factor authentication. Once their session is over, access is automatically revoked.
It’s like giving someone the keys to a safe for just a few minutes and then taking them back when they’re done. This approach massively reduces the chances of attackers exploiting those high-privilege accounts.
Environment Separation
Ever had a situation where something in your development environment accidentally spilled over into production? Not fun. Microsegmentation keeps those environments separate and safe from one another.
For example, your production systems can be walled off, so they only communicate with other production systems. Development servers? They’re stuck in their own sandbox, unable to poke around where they shouldn’t.
This separation improves security while keeping things organised and reducing the risk of errors that can disrupt your operations.
BEST PRACTICES FOR IMPLIMENTING MICROSEGMENTATION

Identify Critical Assets
Start by pinpointing the systems, applications and data that are most valuable to your organisation. These critical assets are the crown jewels of your network—customer databases, financial systems and intellectual property are prime examples. They’re also the most attractive targets for attackers.
Once you’ve identified these assets, segment them into their own secure zones. By isolating critical resources, even if other parts of the network are compromised, attackers will hit a wall when they try to access sensitive data.

Scale Slowly
After identifying and segmenting critical assets, start applying microsegmentation rules slowly to other parts of your network. A phased approach lets you test policies, iron out any kinks and refine processes, and get a feel for how segmentation impacts your environment.
Scaling slowly also reduces disruptions and ensures a smoother rollout. Once everything’s running smoothly, expand the strategy step by step. Scaling gradually ensures you avoid unnecessary disruptions while building a network-wide security framework that’s both effective and manageable.

Enforce Least Privilege
At its core, microsegmentation is about limiting access. The principle of least privilege means that users, devices and applications should only have access to what they absolutely need to get their jobs done—nothing more.
As mentioned in our previous example, your HR team doesn’t need access to financial systems, and your marketing tools shouldn’t connect to customer databases. By setting strict rules around who or what can access each segment, you significantly reduce the chances of a breach spreading through your network.

Automate Where You Can
Managing microsegmentation manually can get overwhelming fast, especially as your network grows. That’s where automation comes in. Tools powered by AI and machine learning can analyse traffic patterns, automatically create rules and flag anomalies—all while keeping everything consistent.
Automation doesn’t just save time; it reduces human error and ensures your policies are applied correctly. For instance, platforms like Zero Networks use AI to streamline the entire process, making it easier to deploy and maintain microsegmentation at scale.

Keep an Eye on Things
Once microsegmentation is up and running, don’t just set it and forget it. Continuous monitoring is essential to spot gaps, unusual activity or areas where your policies could be tighter. Automated tools can help by alerting you to unauthorised access attempts or unexpected traffic patterns.
Regular audits are also a must. They help you stay compliant with regulations and give you a clearer picture of how well your segmentation strategy is working. By staying proactive, you can keep improving and adapting your defences to stay ahead of potential threats.
ZERO NETWORKS: SIMPLIFYING MICROSEGMENTATION
Microsegmentation is a great tool for boosting network security, but let’s be honest, its deployment and management can get pretty complicated.
This is where Zero Networks steps in. They’ve taken a different approach, making it easier for organisations of all sizes to adopt and maintain a solid microsegmentation strategy.
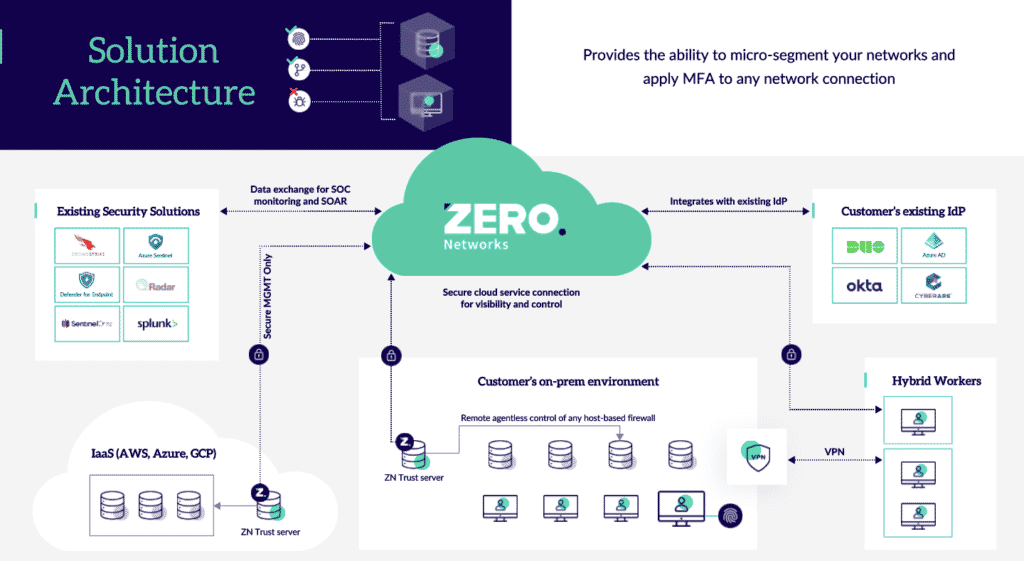
Agentless Deployment
Traditional microsegmentation often means installing software on every device, which can be a pain for IT teams—time-consuming, prone to errors and resource-heavy.
Zero Networks cuts out that hassle with agentless deployment. There’s no need to install extra software on each endpoint or device, so you can get started with segmentation much faster. It also reduces the load on your IT team, making the whole process more efficient and streamlined.
Zero Networks takes care of the heavy lifting, so your team doesn’t have to worry about
managing individual installations.
Automated Rule Creation
When you’re setting up microsegmentation, you typically have to define hundreds or even thousands of rules to control traffic between users and devices. But with Zero Networks, automation is a game-changer.
Their AI-driven learning mode automatically generates segmentation rules based on the real behaviour of your network traffic. No more spending days manually setting up rules—Zero Networks handles it for you. This means fewer mistakes and more accurate, context-aware rules that keep your network safe.
Just-in-Time Multi-Factor Authentication (MFA)
Privileged access is a prime target for cybercriminals, so securing it is a must. Zero Networks goes a step further with Just-in-Time MFA. Rather than requiring constant multi-factor authentication, this method only asks for it when access is actually needed. This ensures that only the right people can access sensitive resources, but it doesn’t add unnecessary steps for users.
By applying MFA to privileged access, organisations can dramatically reduce the chances of an internal or external breach.
Unified Dashboard
As your network grows, keeping track of assets and security rules can get overwhelming. Zero Networks simplifies this with a unified dashboard, where IT teams can manage all network assets from one place.
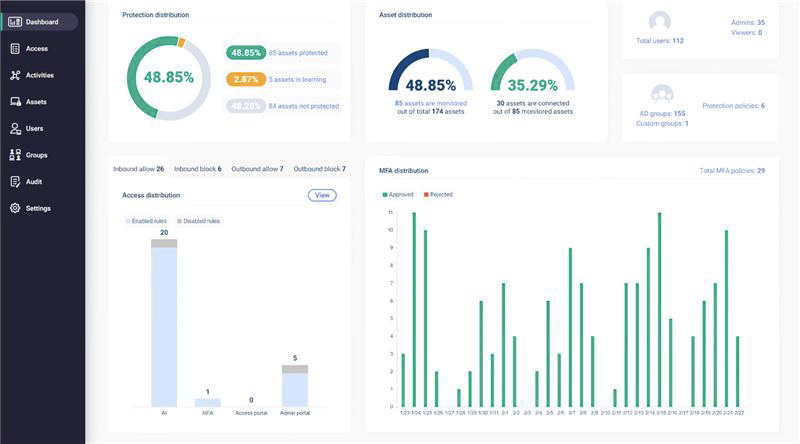
The dashboard gives you real-time visibility into everything—security policies, segmentation rules, user activity—so you can easily monitor, manage and respond to potential threats. With everything in one place, it’s faster and easier to stay on top of network security, no matter how complex your environment gets.

CASE STUDY
THE CHALLENGE
As a growing financial institution that’s expanding internationally, B. Riley Financial faced challenges managing network security. Manual processes for creating and maintaining security rules were time-consuming and prone to gaps, leaving critical systems exposed.
The team also faced insider threats, where an external attacker could gain access to a single system and then move through the network, escalating their privileges along the way.
THE RESULTS
In just a few weeks, B. Riley Financial implemented microsegmentation with Zero Networks, significantly improving its security posture. Automated rule creation and real-time monitoring reduced the administrative workload, allowing the team to focus on strategic priorities.
During internal penetration testing, the platform successfully blocked attack sequences that had previously bypassed defences.
THE SOLUTION
To tackle these issues, Aaron turned to Zero Networks’ microsegmentation platform. The platform’s agentless deployment allowed the team to segment the network without installing additional software on endpoints, streamlining implementation and reducing resource demands.
Zero Networks’ AI-driven rule creation automated the process of building security policies based on actual network activity, saving the team hours of manual effort. The unified dashboard provided centralised visibility, enabling Aaron’s team to monitor activity, manage policies and address potential risks in real time.
Together, Zero Networks’ features and tools allowed B. Riley Financial to isolate sensitive systems and prevent unauthorised lateral movement across the network.
“
I love several things about Zero Networks’ platform. When it comes down to the way that the product works, it works as advertised. It’s been very beneficial to the organisation thus far.”
– Aaron Goodwin
PROTECT EVERY INCH OF YOUR ORGANISATION
Microsegmentation is transforming network security, giving organisations a smarter way to tackle today’s advanced cyber threats. By isolating critical assets, restricting access and stopping attackers from moving across the network, it delivers a level of protection that traditional perimeter-based security just can’t match.
The advantages are clear: a smaller attack surface, greater visibility and stronger control over network traffic. And with solutions like Zero Networks bringing automation and AI into the mix, implementing microsegmentation becomes simpler, faster and far less resource-heavy.
In a world where cyber threats are only getting more sophisticated, microsegmentation is no longer optional. It’s a must-have for organisations that want to protect their data, assets and reputation. By adopting this proactive approach, businesses can stay ahead of threats and strengthen their overall
security posture.

ABOUT ZERO NETWORKS
Founded in 2019, Zero Networks is a simple, fully automated platform for zero trust segmentation and remote access. Zero Networks’ microsegmentation offering is automated, agentless and MFApowered to stop lateral movement and block ransomware. The Identity Segmentation solution provides unprecedented control of admin and service accounts, to enable the principle of least privilege. And the advanced ZTNA solution allows an enterprise to securely connect employees and vendors to its network, without compromising speed or performance.
Offered on a single platform and user interface, Zero Networks is making true Zero Trust architecture a reality for enterprises of any size. For more information, please visit www.zeronetworks.com.
ABOUT INSENTRA
Insentra is a truly collaborative IT Services Partner delivering a range of specialised Advisory, Professional and Managed Services, transacting exclusively through the IT channel. Our partner-centric business model provides our Partners and their clients with access to technologies, industry expertise and accountable outcomes.
Our service offerings cover technologies by Microsoft, Citrix, Red Hat, AvePoint, IGEL, Rimo3, Nulia and many more across modern workplace, cloud, collaboration, security, support, migrations and more. We love what we do and are driven by a relentless determination to deliver exceptional service excellence. The combined individual skills, experiences and perspectives of our crew enable us to achieve powerful results for our Partners and their clients. For more information, visit www.insentragroup.com.





