Taming the Device Zoo: The Ultimate Guide to Microsoft Intune

Table of Contents

INTRODUCTION
Device management is just like zookeeping. Each device is like an animal that needs taking care of to ensure they’re healthy or functioning the way they should. Zookeepers must protect them against sicknesses and infections — or in the case of devices, malware and data breaches — that could put your entire zoo at risk.
And this new hybrid world of work has introduced new challenges in the landscape of device management. Remote and on-site employees use a mix of personal and company-issued laptops, smartphones and tablets, creating a chaotic zoo of devices. Now, it’s become more difficult to keep an eye on all the animals and ensure their safety.
The good news is there is a tool that could empower you to become a master device zookeeper.
Enter Microsoft Intune, a revolutionary endpoint management solution designed to address age-old device management issues, as well as new challenges brought by the new norm that is hybrid work.
In this eBook, we will explore the basics of Microsoft Intune, discovering how this powerful tool can help you wrangle your devices for ultimate security. Dive deep into features like configuration, app management and cloud integration, and master trainer tips and tricks for optimising workflow and fortifying your defences, keeping your digital zoo escape-proof.
WHAT IS MICROSOFT INTUNE?
Microsoft Intune is a mobile device management (MDM) and mobile application management (MAM) provider for all digital devices, including mobile phones, tablets, laptops and other mobile devices. Windows 10, Windows 11, macOS, Android and Apple iOS are all supported by Microsoft Intune – a cloud-based service which allows you ultimate control in how your organisation’s devices are used daily in the workplace. Intune is part of Microsoft 365 and can natively integrate with the full suite of Microsoft 365 products, including Entra ID. It can allow control over access (who and what users can access), as well as Microsoft Purview Information Protection, and data protection.

WHAT DOES MICROSOFT INTUNE DO?
Microsoft Intune allows you to manage devices and applications, including applying security and compliance polices. You can then use Entra ID to enforce access to your applications only from devices and applications that you trust. Intune also enables full control over corporate devices, enabling you to manage the end-user experience and deploy applications and updates to devices regardless of location.
You can deploy apps such as Office 365, Microsoft Teams and OneDrive as customised apps to managed devices.
One of the great features of Intune is controlling how users access company data on personal mobile devices. This enables you to manage applications, not the device, ensuring all company data stays protected and separate from personal data. There are endless opportunities and possibilities using Intune. A few key features include:

- Choose to go 100% cloud management with Intune, or co-manage corporate Windows PCs with Configuration Manager and Intune together
- Secure your company information by controlling the way users access and share information
- Set policies and configure settings on personal and organisation-owned devices to access data and networks
- Deploy and authenticate apps on devices
- Manage your devices to make sure they are compliant with your security requirements
- Manage your apps to ensure they stay up-to-date and comply with security requirements
HOW DOES MICROSOFT INTUNE WORK?
Even though Intune is a cloud-based product, it can integrate with Configuration Manager to control your domain-joined Windows devices that are already enrolled into Configuration Manager on-premises. We recommend that customers who have Configuration Manager already deployed transition to co-management with Intune and Configuration Manager, rather than move to Intune alone. This gives you the best of both solutions.
Below is a high-level diagram of the Microsoft Intune architecture. As you can see, the three main areas are configuring devices, protecting data, and managing apps.
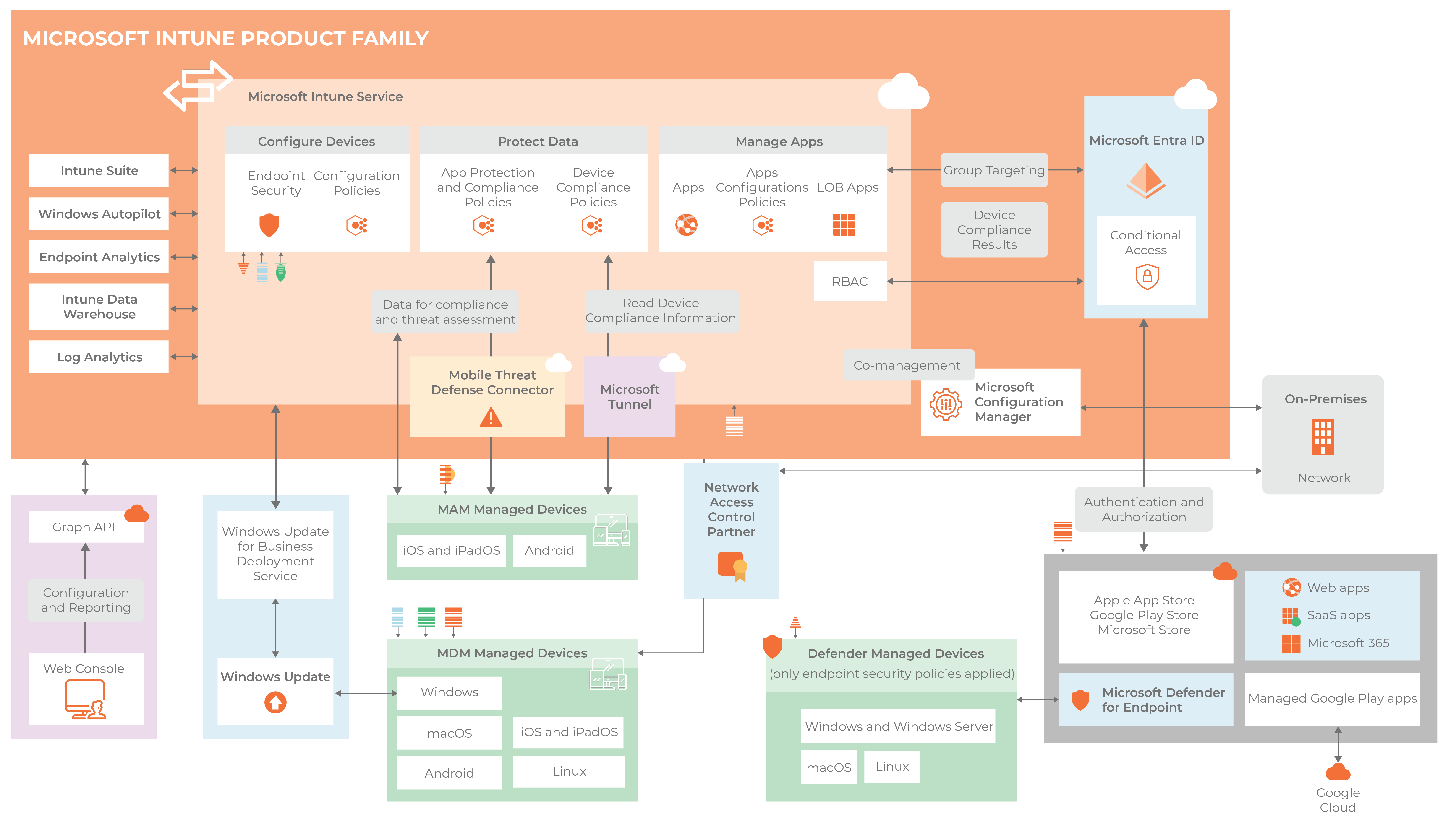
The common practices of using Microsoft Intune:
- Protecting your email and data in both Exchange Online and Exchange on-premises so it can be accessed by devices safely
- Issue corporate-owned devices such as laptops, tablets and phones to employees and enable them with a fully customised out of the box experience
- Enable employees to work from anywhere while still have full control over the user experience and device state
- Offering a “bring your own device” (BYOD) programme to allow employees to securely use the mobile devices they already own
MICROSOFT INTUNE FEATURES
Device Choice & Customisation

Mobile & PC Device Management
Intune allows you to manage devices using an approach that is right for the company. You may require full control over your organisation-owned devices, requiring devices to be enrolled into Intune, and covering settings, features and security.
Essentially, once enrolled, they will receive settings and controls through policies configured in Intune for the organisation. This could include settings such as enforcing BitLocker encryption, software updates, or something simple as a password policy.
The alternative approach is for personal devices where users may not want the organisation to have full control of their devices. This is where you and the end-user have two options:
- Enrol the device so the user has full access to company resources
- Use Intune app protection policies to enforce data protection policies in company apps such as Outlook, SharePoint and Teams
Intune gives administrators the ability to view a list of devices and pull an inventory for them. From there, admins can:
- Configure devices to ensure they meet the company’s security and health standards. For example, you may require devices to be encrypted
- Deploy certificates to allow devices to securely authenticate to Wi-Fi networks or VPNs
- Pull reports on device compliance and users
- Wipe devices or remove data from the device
Considering various regional compliance requirements, it’s also valuable to reference standards like E8, Cyber Essentials, or other relevant mandates, highlighting the importance of adhering to industry best practices for data security and compliance.

Data Protection
Microsoft Intune integrates Microsoft’s data protection and security services, allowing you to fully secure your corporate data.
Intune supports Microsoft Entra ID and Microsoft Purview Information Protection for access control, as well as other Microsoft 365 Apps suite of products. This enables you to remotely deploy apps such as Outlook for specific devices or specific users and control how these apps work if users access company data on their personal devices with app policies.
For example, you can prevent users from copying text or exchanging documents from a company app into an uncontrolled location such as a personal app. There are so many options here, and they allow you to build a solid governance plan.

Managed in the Cloud
Microsoft Intune is a cloud-based solution, enabling you to manage devices without the need to deploy additional on-premises infrastructure required to manage devices or incur costs for additional services.
Intune does integrate with and support several traditional on-premises solutions including Configuration Manager and Active Directory Certificate Services. As Microsoft continues to invest in Intune’s capabilities, you’ll have a path forward to continue to migrate away from on-premises solutions.

Flexible Pricing Plans
DEVICE CONFIGURATION
What is Device Enrolment?
Mobile device management (MDM), requires your devices to be enrolled into Intune, thus fully managing the device. Once a device is enrolled, it is issued an MDM certificate, which is used to communicate between the Intune service and the device. There are several methods to enrol devices you can choose from, depending on the type of device (Windows, macOS, iOS, Android), the device ownership (corporate or personal), and the management requirements (resets, locking).
You can learn more about device enrolment here: Enrollment guide: Microsoft Intune enrollment
Automatic Enrolment

APPLICATION MANAGEMENT
To avoid any issues when initially deploying mobile applications, app configuration policies can be utilised to work with the installation. This helps by assigning configuration settings to an end-user assigned policy prior to setup. These settings are then automatically supplied when the app is configured on the end-user’s device – leaving no outstanding actions for end-users. These configuration settings are unique to each user and for each app.
Configuration policies can be created and implemented to provide configuration settings for both Android and iOS/iPad OS apps alike. These configuration settings allow full app customisation by app management and configuration. Typically, these settings are actioned when the app is run for the very first time (when the app checks for these settings).
App configuration settings may require the following:
- Language settings
- Security settings
- Custom port
- Brand and company logo settings
App configuration policies are important and eliminate the potential of error if end users were to enter these settings themselves. They can also help to provide consistency across your organisation, reducing the need for helpdesk calls and ensuring the greatest efficiencies. By using app configuration policies, new app installations can be easier and quicker and processes more efficient.
Configuration parameters (and the implementation of these which are available) are set by app developers and creators. Always remember to seek validation in the form of legal documentation from these application vendors to ensure all configurations are available, and how these may potentially impact the application.
For some applications, Intune will populate the available configuration settings.

Assigning groups
App configuration policies can be assigned to groups of end-users and devices by using a combination of include and exclude assignments. Once and app configuration policy has been added, you can set the assignments to the policy. When setting assignments, you have the option to include and exclude groups of end-users for which the policy applies to. You can then choose to include one or more groups of end-users or devices.
Protection policies
App protection policies (APP) are rules which guarantee your company’s data is contained in a managed app and ensure it remains safe. A policy can be a set of actions which are restricted or monitored when the user is inside the app, or a policy could be a rule which comes into effect when a user tries to move or access corporate data and prevents them from doing so.
MAM app protection policies allow you to control your company data within your applications. Many Microsoft and third-party apps are supported and can be managed by Intune MAM. The official list can be found here: Supported Microsoft Intune apps | Microsoft Learn
Remote access
The benefit of controlling and protecting your applications with Intune is you have remote control over your apps and data. There are three ways you can wipe app data from Intune:
- MAM selective wipe
- Full device wipe
- MDM selective wipe
MAM selective wipe removed any company data from the app. When a user is using an app, a request is sent every 30 minutes to the Intune service. This check is also carried out whenever the user first launches the app and signs in with their work or school account.

Meanwhile, a full device wipe does what is says on the tin – removes all settings and user data from the device by resetting the device to factory defaults. The device is then removed from Intune.
Lastly, an MDM selective wipe removes any company data from the device. This is generally used for personally owned devices when retiring them from Intune but without needed to wipe the entire device due to personal data. There are a lot of things to think about with this option such as what type of device you are talking about so more information can be found here: Retire or wipe devices using Microsoft Intune | Microsoft Learn
Intune also offers integration with TeamViewer, which is an exclusive partnership. This allows further remote control and support capabilities to multiple platforms such as Windows, MacOS, iOS and Android devices. You can even go as far as gaining remote access to point of sale (POS) systems, kiosks and digital signage. It is very easy to configure as there is a pre-built TeamViewer Connector within Intune ready for activation.
By using TeamViewer, you can leverage real-time sharing to view issues and fix devices with minimal downtime or disruption. All data is end-to-end encrypted and not even TeamViewer can read the data in transit or at rest.
COPILOT IN INTUNE
Microsoft’s Copilot integration in Intune is a significant advancement in the realm of endpoint management, harnessing the power of artificial intelligence to streamline and enhance administrative tasks. Introduced in March 2024, Intune Copilot is designed to provide AI-driven recommendations tailored to organisational needs, optimising both user problem resolution and policy management with unprecedented efficiency and security.
Key Features and Benefits of Intune Copilot
AI-Driven Recommendations
Enhanced Policy Management
Comprehensive Device Context
User-Friendly Prompts and Guidance
Scenarios Benefiting from Intune Copilot
Efficient Troubleshooting
Simplified Policy Implementation
Best Practice Guidance
Integration with Microsoft Copilot for Security
Microsoft Copilot for Security is a generative-AI security analysis tool designed to help organisations quickly access information and make informed decisions that impact security and risk management.
Intune has capabilities powered by Copilot that utilise your Intune data to assist in managing policies and settings, understanding security posture, and troubleshooting device issues. There are two primary ways to access your Intune data using Copilot:
- Microsoft Copilot in Intune:
Copilot is integrated within the Microsoft Intune admin centre. The prompts and outputs provided by Copilot are in the context of Intune and your specific Intune data, making it an invaluable tool for IT admins and IT professionals. This article focuses on how to use Copilot within Intune, detailing the features and benefits available.
- Microsoft Copilot for Security:
This option is accessible via the Microsoft Copilot for Security portal, offering a broader security operations perspective. It provides insights not just from Intune but also from other enabled services like Microsoft Defender, Microsoft Entra ID and Microsoft Purview. This version of Copilot caters to the needs of Security Operations Centres (SOCs) but can also be used by IT admins to gain comprehensive security insights.
By adopting both Intune Copilot and Microsoft Copilot for Security, organisations can create a cohesive framework that enhances security operations. This integrated approach ensures a robust, unified defence against potential threats, optimising both endpoint management and organisational security. For more information on accessing your Microsoft Intune data in Copilot for Security, visit Access your Microsoft Intune data in Copilot for Security.
Future Outlook of Intune Copilot
As AI technology continues to evolve, Intune Copilot is expected to incorporate even more advanced features, further simplifying device management and enhancing security. Staying updated with these advancements will be crucial for organisations aiming to maintain a secure and efficient IT environment.
For more detailed information and to stay abreast of the latest developments, visit the official Microsoft Copilot in Intune page.
CLOUD-BASED SERVICE COMPARISONS
Description: A lightweight version of MDM provided by Microsoft.
Features:
- Enforces MDM policies and settings.
- Controls access to Office 365 data on supported devices.
- Allows remote wiping of company data from devices.
Inclusions:
- Typically included in most Office 365 subscriptions.
Limitations:
- Lacks MAM features.
- Limited configuration capabilities.
- No deployment functions or ability to remotely wipe apps.
Description: Microsoft’s comprehensive MDM and MAM solution for managing mobile devices and apps.
Features:
- Offers advanced MDM and MAM functionalities.
- Provides robust configuration capabilities.
- Enables deployment functions and remote wiping of apps.
Pricing:
- May require a separate, potentially more expensive subscription.
Advantages:
- Comprehensive management solution for both devices and apps.
- Greater flexibility and control over configuration and deployment.
- Enhanced security features compared to MDM for Office 365.
Description: On-premises solution for device management previously known as Microsoft System Centre Configuration Manager (SCCM or ConfigMgr)
Features:
- Widely used but complex to set up and maintain.
- Suitable for managing on-premises infrastructure.
Transition to Intune: Can be integrated with Intune for co-management or migration to cloud-based management.
Description: Cloud-based solution for modern device management.
Features:
- Allows moving away from on-premises infrastructure.
- Supports co-management with Configuration Manager.
- Doesn’t support image deployment but focuses on configuring devices with deployment profiles.
Description: Traditional method for managing on-premises infrastructure.
Features:
- Controlled devices/users using Group Policy Objects (GPOs).
- Not supported in cloud-based environments like Intune.
Description: Cloud-based alternative for managing devices/users.
Features:
- Utilises Configuration Profiles for policy management.
- Offers similar functionalities to GPOs but in a cloud-based environment.
CERTIFICATION
There is no specific certification for Microsoft Intune, as Microsoft now aim for role-based certifications, although there are few certifications which include Intune in the topics, such as:
- Microsoft 365 Certified: Modern Desktop Administrator Associate
- Microsoft 365 Certified: Enterprise Administrator Expert
INTUNE PRICING & LICENSING
- Microsoft 365 E5
- Microsoft 365 E3
- Enterprise Mobility + Security E5
- Enterprise Mobility + Security E3
- Microsoft 365 Business Premium
- Microsoft 365 F1
- Microsoft 365 F3
- Microsoft 365 Government G5
- Microsoft 365 Government G3
- Microsoft Intune for Education

Be careful here, though. The Intune device license is just a licensing construct and is not enforced. Consider the most common scenario for device-based licenses being kiosk devices that can be provisioned via Windows Autopilot and Intune, but automatically sign into the device with a local account. These devices are typically used for shared or public use scenarios. If a licensed user never signs into the device, additional applications and update may never be processed by the device.
Microsoft Intune Plan 2
An add-on to Microsoft Intune Plan 1 that offers advanced endpoint management capabilities. Intune Plan 2 is included in Microsoft Intune Suite.
Microsoft Intune Suite
An add-on to Microsoft Intune Plan 1 that unifies mission-critical advanced endpoint management and security solutions.
TAME THE DEVICE ZOO WITH INTUNE
Device zookeeping is no easy feat, especially with today’s growing culture of BYOD and the increasing number of data breaches. As such, zookeepers must arm themselves with the right tools that make their jobs easier and keep their device jungles safer. This is exactly what Intune does.
With Intune, you gain customisation and management features and capabilities that allow you to configure each device uniquely, allowing you to ensure each endpoint’s security.
However, we understand if your IT team does not have the time or resources required to master a new tool. That’s where Intune Managed Service comes in. Insentra’s team of Intune gurus handle everything, ensuring your devices and more importantly your users, stay secure and happy. With expert tamers keeping an eye on your devices, you can rest assured on focus on other IT tasks, knowing your digital zoo is always safe and healthy in Insentra’s hands.
WHY INSENTRA
WE DARE TO BE DIFFERENT
Insentra is a collaborative IT Services partner delivering specialised Advisory, Professional and Managed Services. Our Partner-centric model provides you direct access to industry expertise.
We believe great business relationships start with trust. We are 100% channel focused meaning we only transact and deliver services exclusively with our Partners.
Our dedication to you is based on our vision to be the number one channel services company on the planet. We do this by being the best version of ourselves, creating an outstanding environment for our team, loving the work we do and amazing each other and our partners in every way.
We are and always will remain a PartnerObsessed™ company.
DOWNLOAD BROCHURE

Thank you for downloading The “Taming the Device Zoo: The Ultimate Guide to Microsoft Intune.”

We’ve sent a copy to your inbox. Remember to mark hello@insentragroup.com as a “safe sender”, and to check any junk or spam folders so you receive your copy.

We’ve sent a copy to your inbox. Remember to mark hello@insentragroup.com as a “safe sender”, and to check any junk or spam folders so you receive your copy.