In the ever-evolving landscape of cybersecurity, staying ahead of vulnerabilities and ensuring the integrity of your systems is paramount. Red Hat Enterprise Linux (RHEL) has long been a trusted choice for many organisations, and its robust security features are a major factor in its popularity. However, even the most secure systems can be susceptible to vulnerabilities. To address this, Red Hat offers a powerful combination of tools – Red Hat Insights and Ansible Automation.
In this comprehensive guide, we will walk you through the process of patching RHEL vulnerabilities using Red Hat Insights and Ansible Automation. Whether you’re a seasoned Linux administrator or just beginning your journey, this step-by-step tutorial will empower you to proactively manage vulnerabilities and optimise your system configurations.
Before we dive into the nitty-gritty of the patching process, let’s ensure you have the necessary prerequisites in place. You’ll need:
Prerequisites:
- Red Hat Enterprise Linux 8+: Ensure your system is running on this version or later.
- Red Hat Insights Client: Install and register your device with Red Hat Insights, requiring an internet connection.
- Red Hat Subscription: Access to cloud.redhat.com is essential, so make sure you have an active subscription.
- Red Hat Account: You’ll need a Red Hat account to access the required resources.
Insights Client installation
Note: Make sure you have the repositories enabled and access to the Internet as the insights client will require communication with the Red Hat’s cloud portals.
- Install insights client
dnf install insights-client - After installing the client, register your system with Red Hat Cloud Insights using the following command. This will connect your RHEL 8 system to Red Hat Insights, and it will start uploading data for analysis.
insights-client --register - After installing the client, register your system with Red Hat Cloud Insights using the following command. This will connect your RHEL 8 system to Red Hat Insights, and it will start uploading data for analysis.
insights-client --register - Enable the Insights client to auto-upload data hourly:
systemctl enable insights-client.timer
systemctl start insights-client.timer - By default, the insights-client’s timer is set to 1h. If you want to change the timer, use the following command:
systemctl edit insights-client.timer
[Timer]
OnCalendar=hourly
RandomizedDelaySec=14400 - If you don’t want to wait for the daily automatic upload, you can manually upload data using:
insights-client --upload - To ensure that your system is registered and is sending data, run the following command:
insights-client --status - If everything is set up correctly, you should see a message similar to the one below:
insights-client --status
System is registered locally via .registered file. Registered at 2023-02-09T16:09:54.762936
Insights API confirms registration. - Finally, log into the Red Hat Cloud Insights web console to view your system’s data. Your system should appear in the inventory.
- Navigate to https://console.redhat.com/insights/dashboard and enter your credentials
- In the left pane, click Inventory → Systems
- Confirm the registered server is on the list of servers
Red Hat Insights Integration with AAP
- Navigate to Ansible Automation Platform GUI and login with privileges to allow you creating credentials, inventories, projects and templates
- Navigate to Credentials and create a new credential:
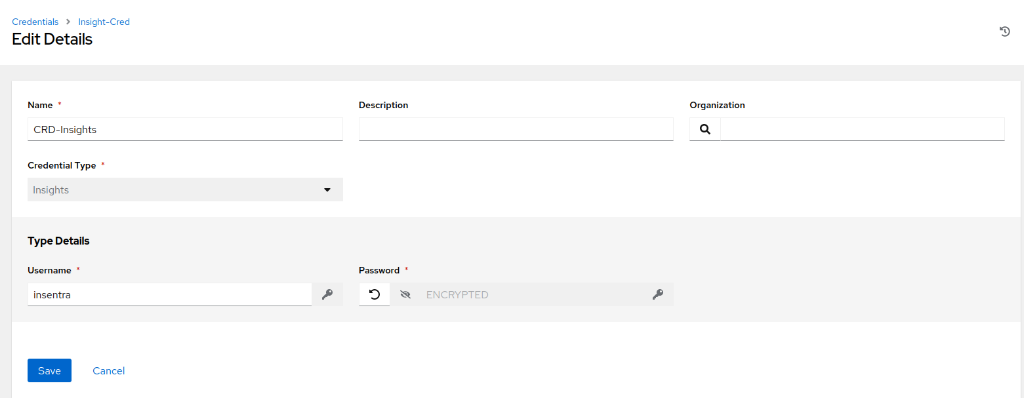
- Click Save
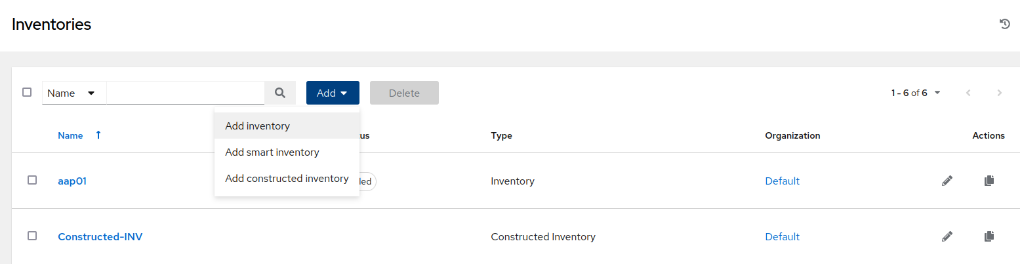
- Navigate to Inventories and create a new Inventory, selecting Add inventory:
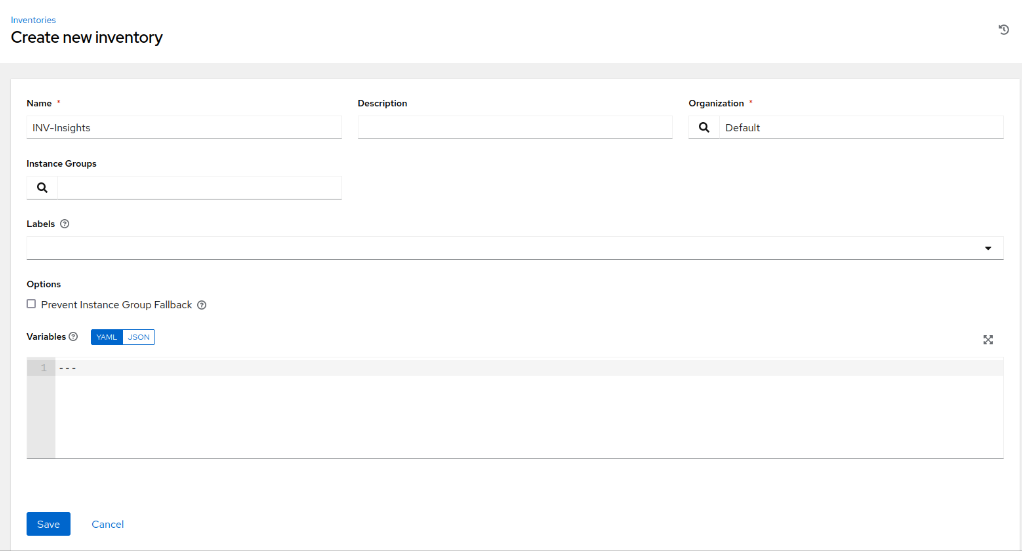
- Click Save and click on Sources
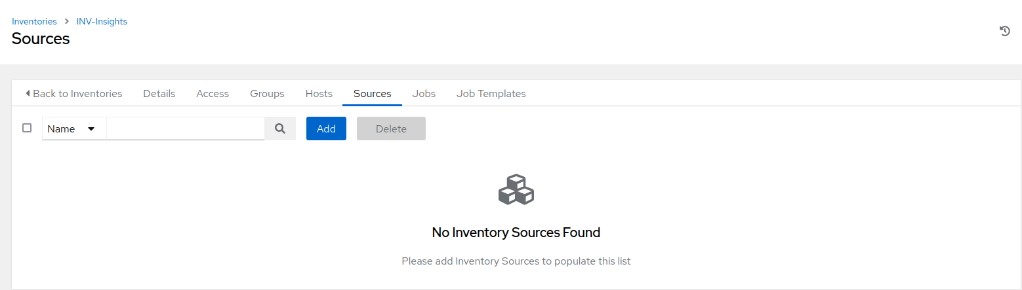
- Click Add to add a new source
- Specify a name and select Red Hat Insights as the source type. If the credential created in the previous step is the only one associated with Insights, it will be automatically selected; otherwise, choose the appropriate credential from the list. To ensure the inventory stays up to date, I enable the options for “Overwrite,” “Overwrite Variables,” and “Update on Launch”. Click Save
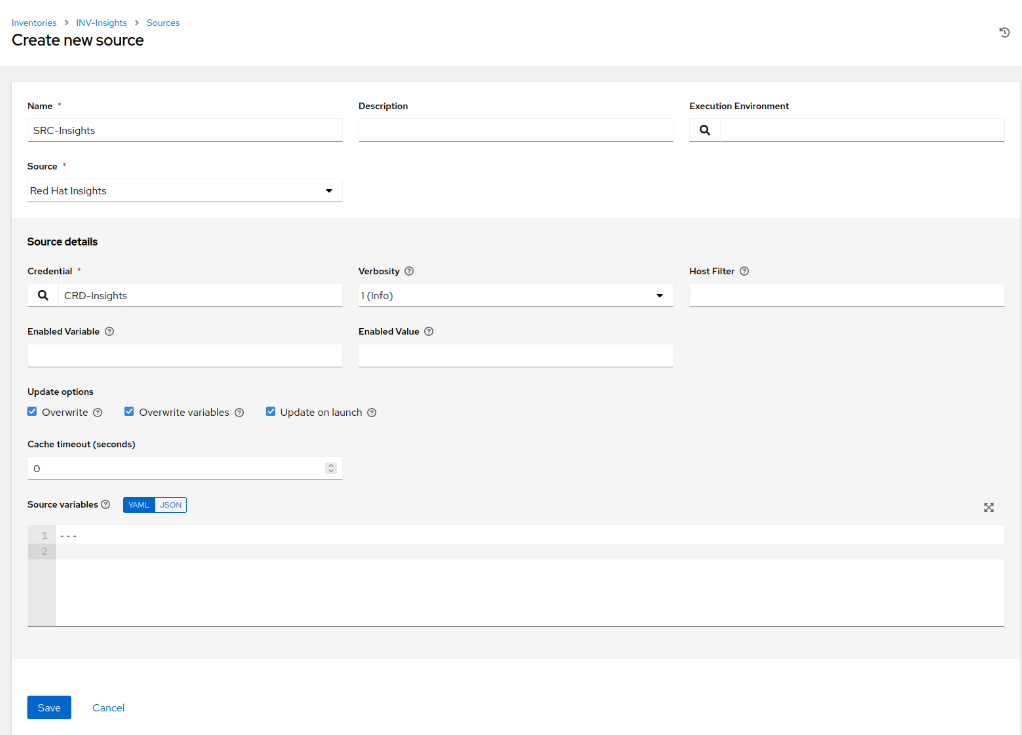
- Navigate to the ‘Projects’ section and create a new project. Fill in the name, specify an organis
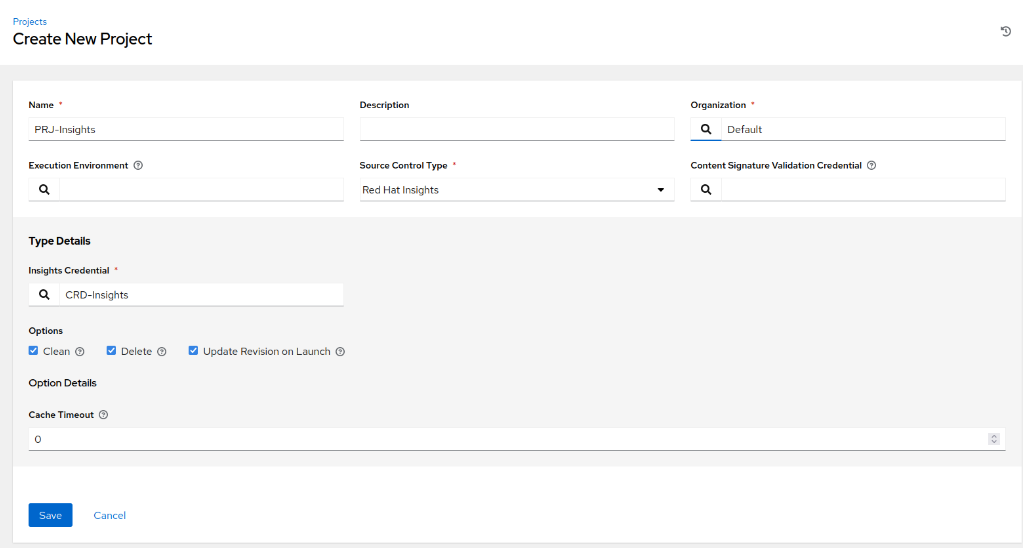
zation (if applicable), and choose an Execution Environment. Set the ‘Source Control Type’ to ‘Red Hat Insights’. If the credential you created in the previous step is the only one associated with Insights, it will be auto selected; otherwise, pick the appropriate credential from the list. To make sure we’re using accurate projects sourced from Red Hat Insights, enable the options for ‘Clean’, ‘Delete’, and ‘Update Revision on Launch’. Click Save.
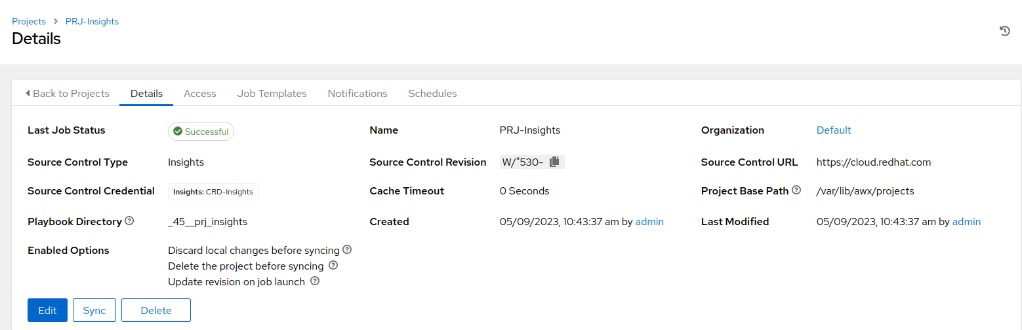
- After saving the project, a Sync job will automatically initiate to synchronise Insights with the Ansible Automation Platform (AAP). If everything is configured correctly, the ‘Last Job Status’ should display as ‘Successful’.
- We will skip template creation for now. Let’s address Red Hat Insights Console and select some vulnerabilities to patch
Selecting Vulnerabilities in Red Hat Console
- Navigate to https://console.redhat.com/insights/dashboard
- Several methods are available for patching the system, and we will focus on addressing systems with known exploits. If any of the registered systems contain a package vulnerable to a known exploit, this information will be displayed on the dashboard
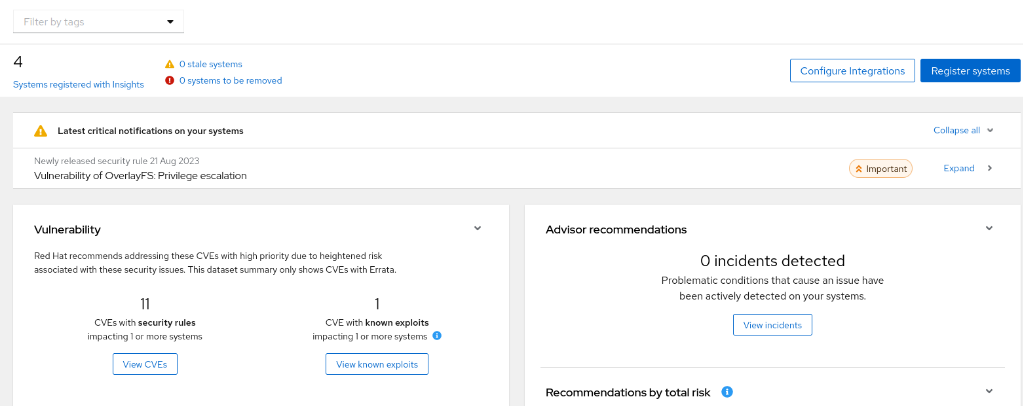
- Click on View known exploits. You will be taken to CVEs
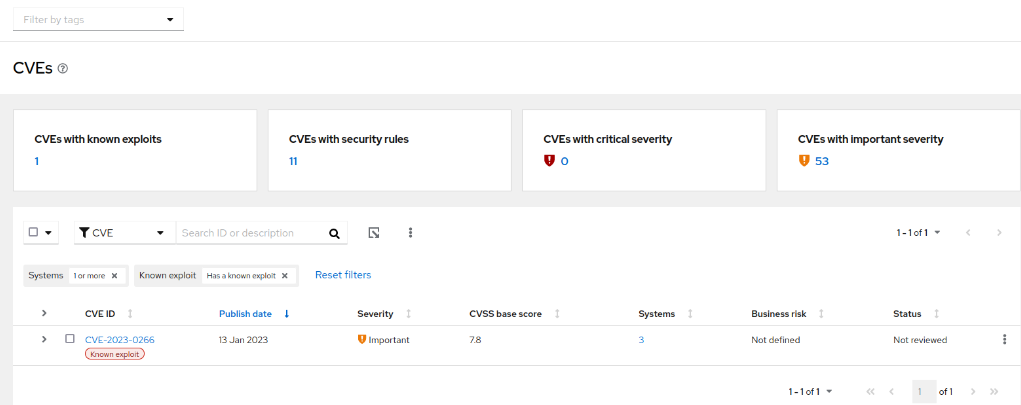
- Click on the number of impacted systems (3 in this example), select the server(s) on which the CVE will be patched and click on Remediate button
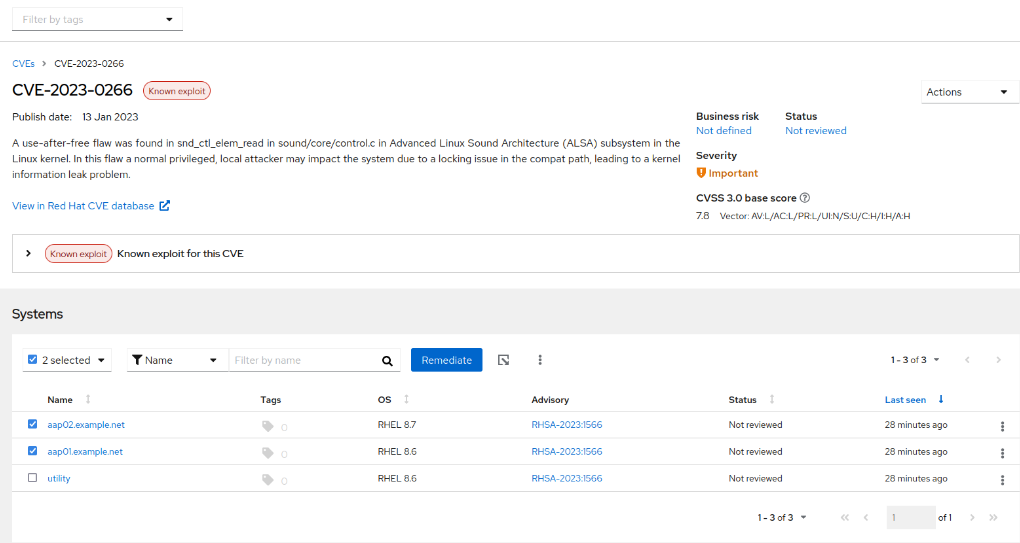
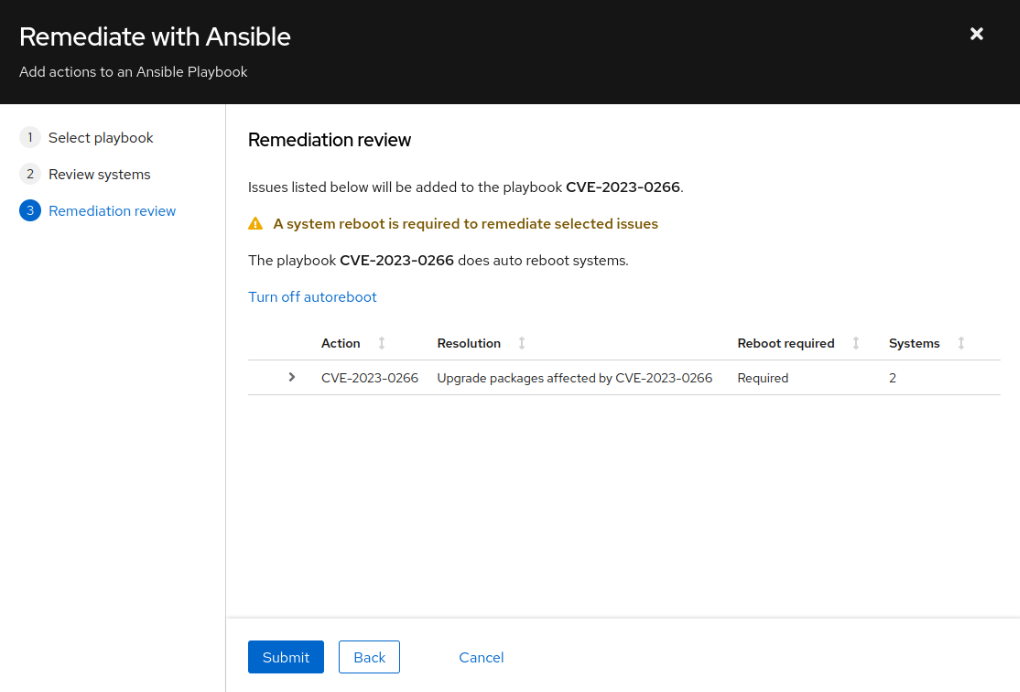
- You can either create a new playbook or augment an existing one. If you need to isolate CVEs (Common Vulnerabilities and Exposures), we recommend creating a new playbook. Be aware that the playbook’s name will be selectable in the Ansible Automation Platform (AAP) template, as the AAP Project sync will import all playbooks created in the Insights Portal. In this example, a new playbook’s name will be related to the CVE which will be patched: CVE-2023-0266. Click Next
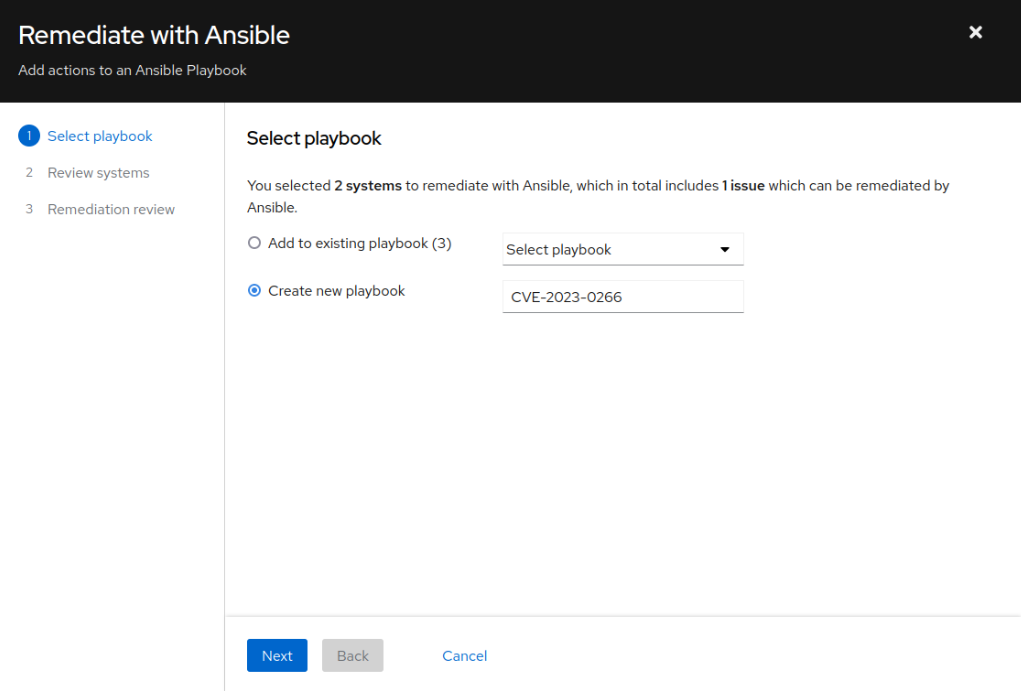
- Review the systems to be patched (add or remove) and click Next
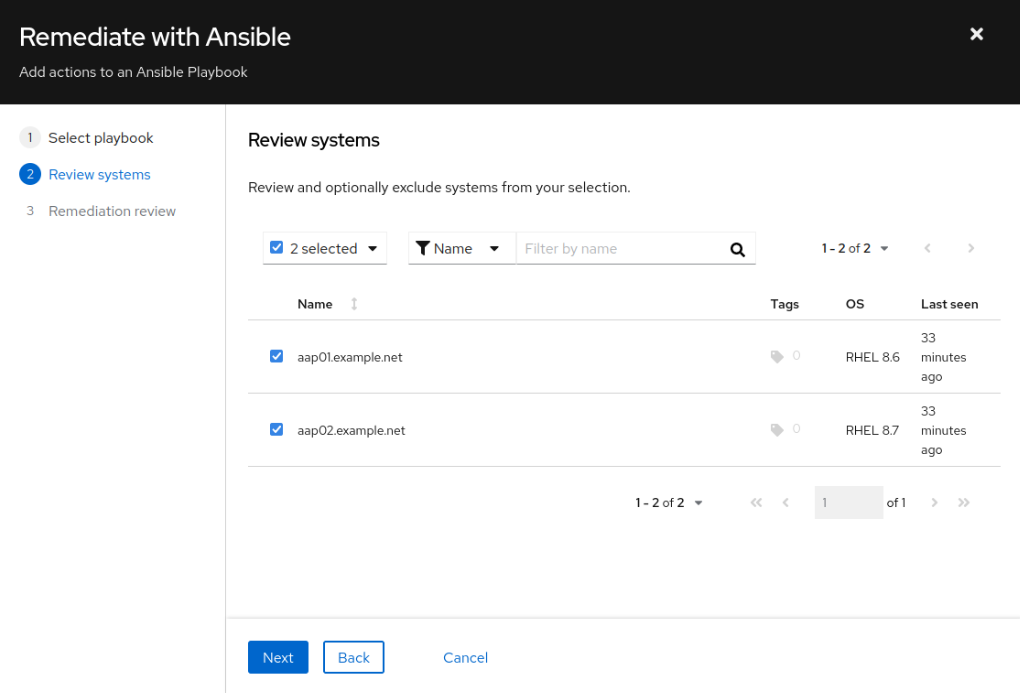
- Click on Submit. The playbook will be created on the portal
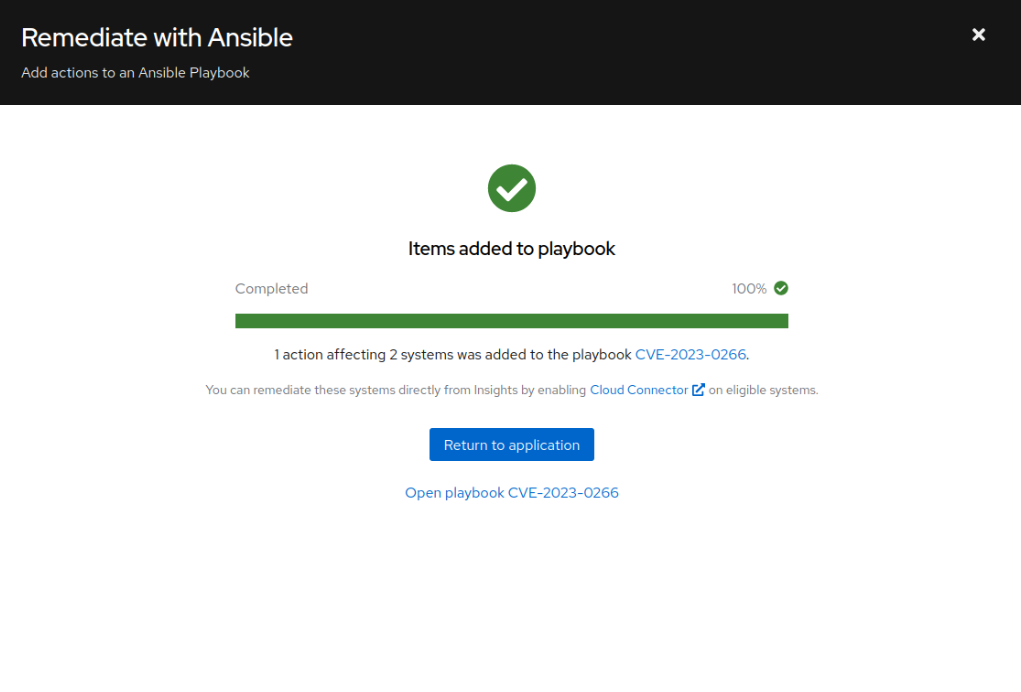
Putting All Things Together
- Navigate to AAP GUI
- Navigate to Projects and click Sync Icon next to PRJ-Insights created in the previous step. This is necessary to clone all the playbooks which were created in the previous steps and make them available for use in a template
- Create a new job Template, selecting inventory and project created in the previous steps. Do not forget to select Credentials
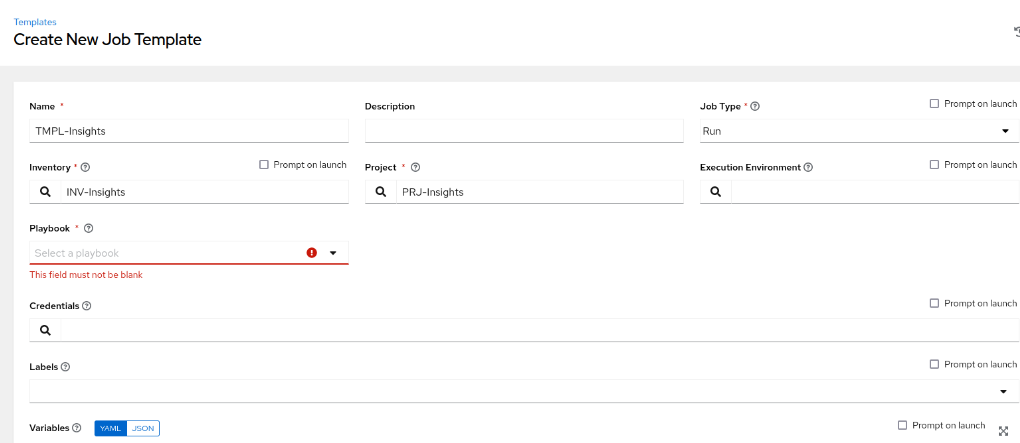
- Click on the ‘Playbook’ field and select the playbook that we previously created in the Insights portal. Since we gave it an easily identifiable name, it should be straightforward to locate. In our case, we named the playbook ‘CVE-2023-0266’. Click Save
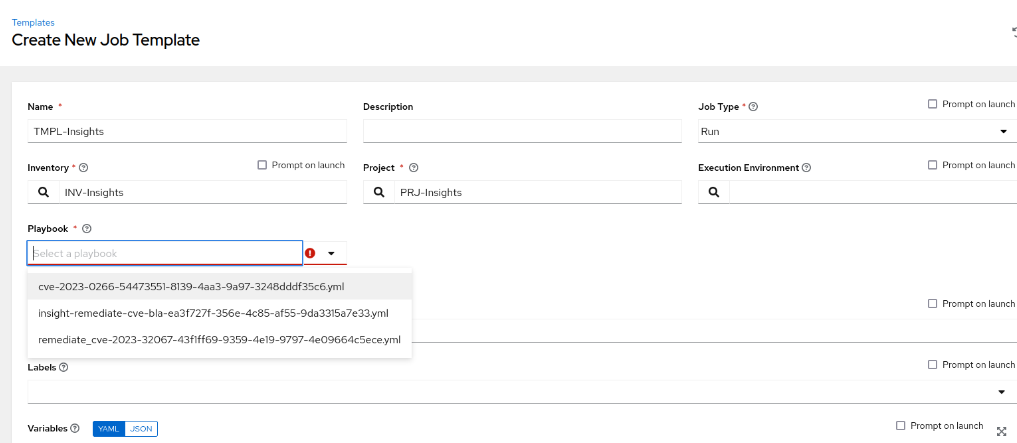
- Click ‘Launch’ and monitor the job output. Remember that when we created the playbook, we specified certain servers. Therefore, even if our inventory includes multiple servers, the template execution with this particular playbook will be restricted to those selected servers. Also note, that the CVE required a reboot, as a result, at the end of the patching, the systems will be rebooted:
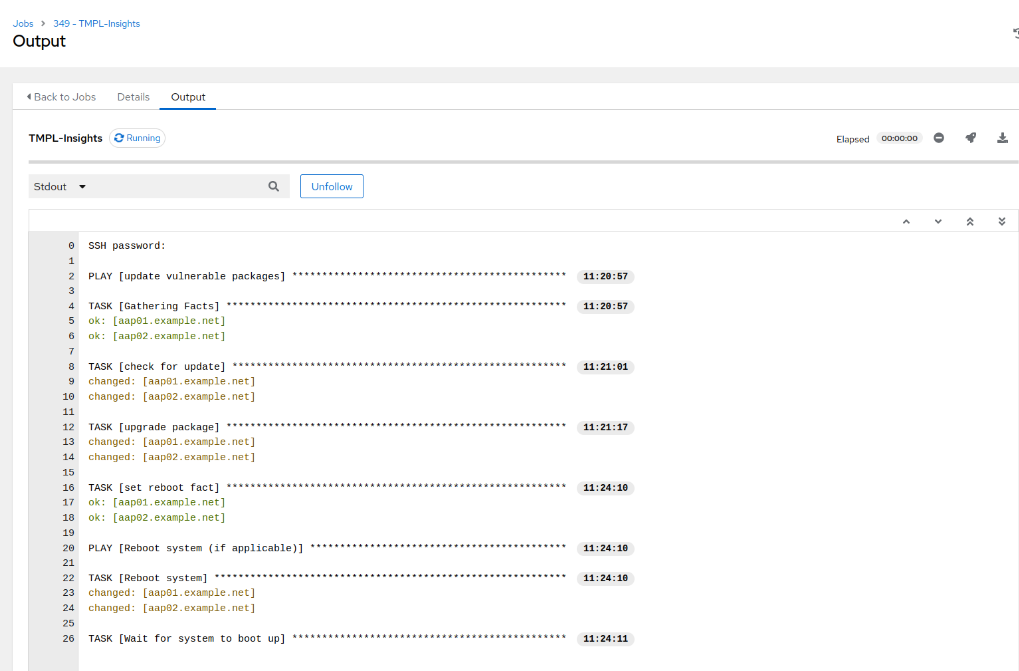
And there you have it—a comprehensive guide to integrating Red Hat Insights with Ansible Automation Platform, all the way from initial setup to targeted playbook execution. With these tools at your disposal, you’re well-equipped to proactively manage vulnerabilities and optimise your system configurations.
But remember, our experts at Insentra are always here to help you take the next step. If you have questions, need assistance, or want to explore even more ways to optimise your IT environment, don’t hesitate to contact us.
Happy automating!